Become a broker partner with Mitigata
Cyber risks are complicated and it requires a special approach to deal with the underwriting process. We help you underwrite customised cyber policies.

What do we do for the broker? Scope of work
The hassle-free deal registration process
Cyber questionnaire assisted filing process
Cyber security scan report
Calculate your client’s cyber risk exposure
Quote creation and quote comparison reports
Know your policy session with a cyber underwriter.
Post-incident support for digital forensics and claims assistance
Introducing Mitigata’s Cyber Security console
Dashboard
- Real-time Monitoring: Continuously tracks and updates the organisation's cyber risk profile in real-time, allowing for immediate detection of potential threats.
- Customizable Views: Offers customizable dashboard views to cater to the specific needs and preferences of different users within the organisation, ensuring relevant data is always front and centre.
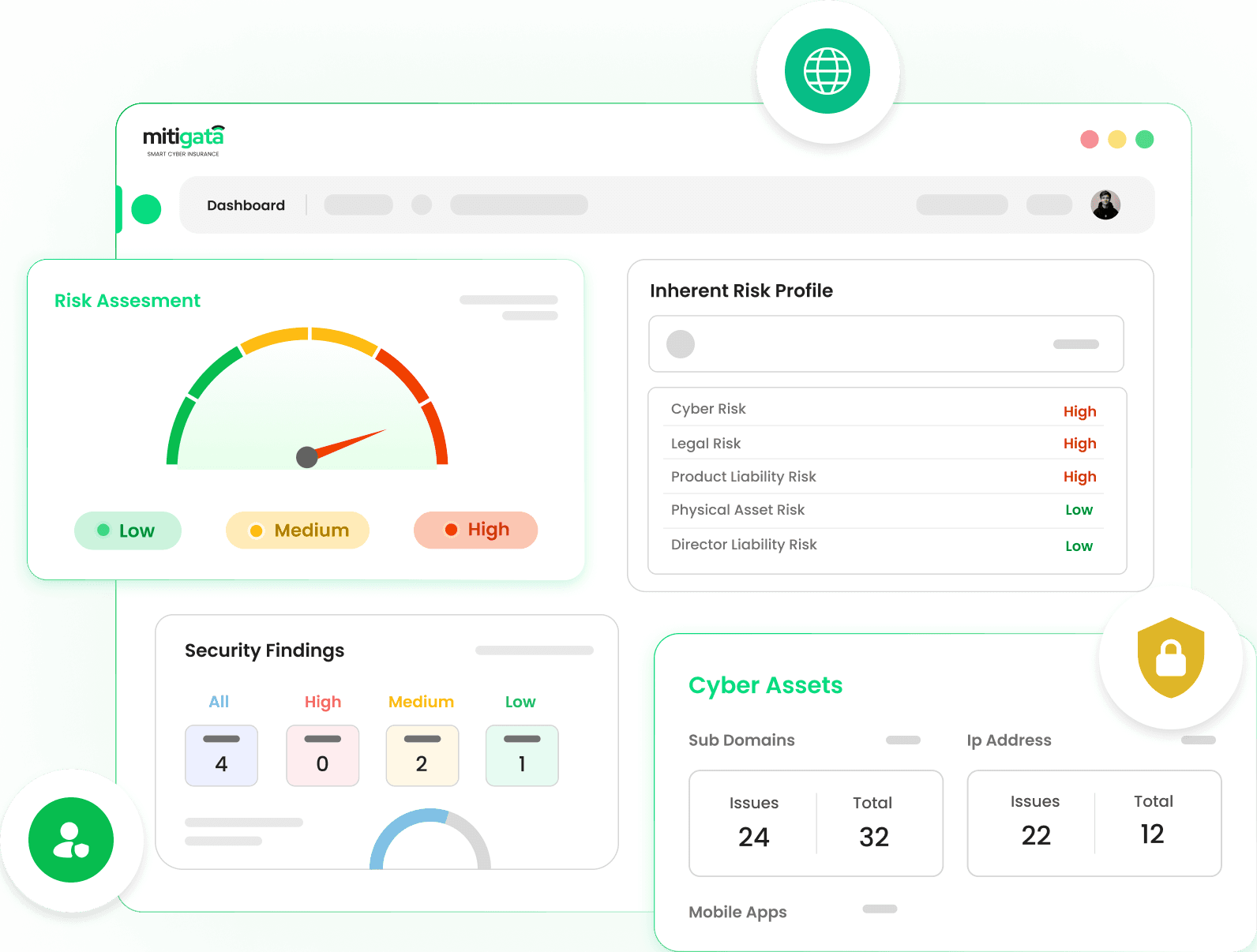
- Continuously tracks and updates the organisation's cyber risk profile in real-time, allowing for immediate detection of potential threats.
- Offers customizable dashboard views to cater to the specific needs and preferences of different users within the organisation, ensuring relevant data is always front and centre.

Insurance
- Immediate Quote Generation: Users can get insurance quotes instantly, simplifying the decision-making process for cyber insurance coverage.
- Transparent Claims Tracking: Offers a clear and straightforward tracking system for claims, providing updates at each stage until resolution.

- Users can get insurance quotes instantly, simplifying the decision-making process for cyber insurance coverage.
- Offers a clear and straightforward tracking system for claims, providing updates at each stage until resolution.

Detect the Undetected
- Real-Time Breach Detection: Continuously scans dark web forums, marketplaces, and encrypted platforms for leaked credentials, sensitive data, and stolen organizational information.
- Actionable Threat Alerts: Receive timely notifications whenever your organization's data or identifiers are found on the dark web.
- Tailored Risk Insights: Define specific keywords, domains, or identifiers unique to your business. Access detailed reports and actionable intelligence to identify vulnerabilities and safeguard your organization from emerging threats.

- Continuously scans dark web forums, marketplaces, and encrypted platforms for leaked credentials, sensitive data, and stolen organizational information.
- Receive timely notifications whenever your organization's data or identifiers are found on the dark web.
- Define specific keywords, domains, or identifiers unique to your business. Access detailed reports and actionable intelligence to identify vulnerabilities and safeguard your organization from emerging threats.

Security Checklist
- Automated Updates: Users can get insurance quotes instantly, simplifying the decision-making process for cyber insurance coverage.
- Customizable Tasks: Allows organisations to customise the checklist to fit their specific security requirements and priorities.

- Users can get insurance quotes instantly, simplifying the decision-making process for cyber insurance coverage.
- Allows organisations to customise the checklist to fit their specific security requirements and priorities.

Security Findings
- Severity Ratings: Classifies findings by severity levels, enabling users to focus on the most critical issues first.
- Integration with Remediation Tools: Offers seamless integration with third-party remediation tools for efficient issue resolution.

- Classifies findings by severity levels, enabling users to focus on the most critical issues first.
- Offers seamless integration with third-party remediation tools for efficient issue resolution.

Phishing Risk
- Automated Alerts: Sends real-time alerts for newly identified phishing risks, minimising the window of opportunity for attackers.
- Educational Resources: Provides access to training and resources to help employees recognize and avoid phishing attempts.

- Sends real-time alerts for newly identified phishing risks, minimising the window of opportunity for attackers.
- Provides access to training and resources to help employees recognize and avoid phishing attempts.

Marketplace
- Peer Reviews and Ratings: Includes user reviews and ratings for each cybersecurity solution, aiding in informed decision-making.
- Trial Offers: Many solutions come with trial offers or demos, allowing users to assess suitability before making a purchase.

- Includes user reviews and ratings for each cybersecurity solution, aiding in informed decision-making.
- Many solutions come with trial offers or demos, allowing users to assess suitability before making a purchase.

Claim Insurance
- Simplified Documentation Process: Streamlines the documentation process, making it easier for users to submit the necessary information.
- Expert Support: Offers direct access to insurance claim experts for personalised guidance and support.

- Streamlines the documentation process, making it easier for users to submit the necessary information.
- Offers direct access to insurance claim experts for personalised guidance and support.

Why choose Mitigata ?
Partner first approach
At the core of our business is a partner-first approach, ensuring your success. We provide the quickest SLAs, delivering fast and reliable service. Our cybersecurity expertise and advanced technical products empower you with the best tools to safeguard your clients, ensuring long-term partnerships built on trust and excellence.
Quickest SLAs
We understand the importance of time. With the quickest SLAs in the industry, we ensure that your requests are handled with priority, keeping your business running smoothly without delays. Experience unmatched responsiveness and efficiency.
Cyber security expertise
Our team of cybersecurity experts brings deep knowledge and experience to the table. We help you navigate the complex world of cyber threats, offering tailored solutions that protect your clients and reinforce your market leadership
Technical product
Our cutting-edge technical products are designed to provide seamless protection and integration. We offer innovative solutions that meet the demands of today’s digital landscape, enabling you to deliver top-notch security and value to your clients.
Best revenue-sharing model
A best revenue-sharing model ensures a fair distribution of profits based on contribution. It typically involves sharing a percentage of generated revenue between stakeholders, incentivizing performance and aligning goals. The model fosters collaboration, drives growth, and motivates partners or employees to achieve mutual success by tying rewards to results.
Existing partner
Mitigata Expert Team

Bhranti Shah
Chief Underwriting Officer

Avishkar Gaikwad
Head of International Business

Akshit Kaushik
GRC Expert

Mayank Morya
Security Expert

Archit Vyas
Head of Partnership

Akshaay Nataraja Murthi
Assistant Vice President- Liability and Special Risks



