What if I told you that 422 million data records were exposed in just Q1 of 2025?
Consider the extent of customer trust lost, intellectual property stolen, regulatory fines issued, and reputations irreparably harmed.
Most of the data breaches we see around are a result of human error, misconfigured tools, stolen credentials, and unchecked third-party access.
However, many businesses still underestimate the importance of Data Loss Prevention (DLP) solutions. As per reports, companies using AI-powered DLP and security automation reduced breach costs by up to 30% and cut detection-to-containment times by months.
In this blog, we’ll explore the key DLP solution features to look for, real-world use cases, and how to choose the right solution for your enterprise.
Mitigata: India’s Only Full-Stack Cyber Resilience Company
We partner with the world’s leading DLP providers, including Forcepoint, Symantec, Trellix, Proofpoint, Microsoft Purview, and others, to bring you enterprise-grade data loss prevention solutions at rates that are 30% less than market prices.
Why Mitigata leads the market in DLP services:
Partnership Power: Our partnerships with 500+ security OEMs mean we can provide you with multiple DLP options.
Full-Service Implementation: Our team provides end-to-end implementation and configuration support.
Zero Extra Costs: Unlike other suppliers, we will not burden you with any additional training or support costs that were not in the quote
Proven Success: We’ve gained the trust of 800+ firms across 25+ industries and achieved a record-breaking 100% retention rate.
Tailored Solutions + Seamless Integration: We only offer solutions that work flawlessly with your SIEM, EDR, or cloud security tools.
Data Doesn’t Leak on Our Watch
We deploy fast, integrate deeply, and don’t surprise with hidden costs – just ask our 800+ happy clients.

What is DLP and How Does It Improve Cybersecurity
Data Loss Prevention (DLP) is your organisation’s security system for sensitive information. It watches over your data everywhere it goes, whether it’s sitting in storage, moving across your network, or being used on someone’s laptop.
Here’s how DLP improves cybersecurity:
- Monitors data in motion (emails, uploads, file transfers)
- Scans data at rest (stored files and databases)
- Watches data in use (copy/paste, screenshots, AI prompt inputs)
- Stops insider threats, accidental or intentional
- Ensures compliance with regulations like GDPR, HIPAA, and India’s DPDP Act
Without DLP, you’re flying blind. Sensitive data can slip out of your perimeter without a trace.

Key Features of DLP Software
When evaluating a DLP tool, look for these core DLP software features that deliver true protection:
Data Discovery and Classification
Before you can protect data, you must first identify where it is stored, such as file servers, databases, endpoints, cloud storage, and collaboration platforms. Without this feature, you’re trying to protect data you don’t know you have, which is impossible
Look for:
- Automated scanning of structured and unstructured data
- Supports fingerprinting and exact data matching (EDM) for very sensitive records.
- Machine learning-based classification that improves its accuracy over time
- Pre-built classifiers for common data types (PII, PHI, PCI, and GDPR-protected data).
- Custom classification rules for your specific data types.
- To identify sensitive data in photographs and scanned documents, use Optical Character Recognition (OCR).
Multi-Channel and Real-Time Monitoring
Your DLP should detect and alert you the moment sensitive data moves in an unauthorised way.
Look For:
- Unified policy management across all channels (set once, enforce everywhere)
- Coverage of modern collaboration tools (Slack, Teams, Zoom, etc.)
- Monitoring of generative AI platforms (ChatGPT, Copilot, Bard)
- Mobile device support (iOS and Android)
- Support for both cloud and on-premise deployments
Explore the top DLP companies in India and learn which solutions offer the strongest protection for sensitive business data today.
Content Inspection and Context Analysis
Modern DLP uses behavioural analysis and contextual information to make smarter decisions about what’s risky and what’s normal business activity.
Look For:
- User and Entity Behaviour Analytics (UEBA) integration
- Machine learning that adapts to normal business patterns
- Risk scoring that prioritises incidents by severity
- Role-based policies that adjust controls based on job function
- Adaptive policies that consider multiple contextual factors
Your Data’s Bodyguard - On Duty 24/7
From policy to protection, our DLP solutions leave no gap unguarded, and our expert team never ghost you.

Flexible Response Actions and Remediation
When DLP detects a policy violation, it needs options beyond just “block” or “allow.” Modern DLP solutions offer a range of response actions that balance security with business productivity.
Response options include:
- Block: Completely prevent the action
- Encrypt: Allow the transfer, but automatically encrypt the data
- Watermark: Add visible or invisible marks to track document usage
- Quarantine: Move suspicious files to a secure holding area for review
- Require Justification: Ask the user to explain why they need to perform this action
- Notify: Alert security teams without blocking the user
- Redact: Remove sensitive portions while allowing the rest of the content through
Endpoint Protection
Data doesn’t only reside in the cloud. DLP tools must secure endpoints, including laptops, desktops, and mobile devices.
Endpoint DLP capabilities include:
- Monitoring file operations (copy, move, delete, rename)
- Controlling USB and external device usage
- Managing printing of sensitive documents
- Preventing screenshots of confidential data
- Monitoring clipboard operations
- Enforcing encryption on stored sensitive files
Understand the differences between EDR, XDR and MDR and learn which detection approach best strengthens your organisation’s security posture today.
Cloud and SaaS Integration
Looking at the widespread usage of cloud tools in companies, this feature has become more than essential now. It is to provide protection to platforms like Microsoft 365, Google Workspace, Salesforce, Box, Dropbox, and hundreds of other cloud services.
Look for:
- Key SaaS platforms include O365, Google Workspace, and Salesforce.
- API integration for real-time monitoring, with Cloud Access Security Broker (CASB) features.
- Shadow IT discovery to detect illegal cloud services
- Data Loss Prevention for Collaboration Tools (Teams, Slack, Zoom)
- Protection for cloud-to-cloud data transfer
Policy Customisation and Automation
Every organisation’s data flow is different. A flexible DLP solution allows:
- Custom rule creation for departments or regions.
- Automated enforcement actions: block, encrypt, quarantine, or log.
- Machine learning-based adaptive policies that evolve with usage.
Premium Coverage Only At ₹4,200/Endpoint
Advanced DLP solution with full coverage, seamless onboarding, and 24/7 support. Get your free demo NOW.

Generative AI and Collaboration Tool Monitoring
As per a survey, 78% of companies use tools like ChatGPT, Copilot, and Notion AI in their everyday tasks. Looking at the expansion of generative AI tools in the workplace, this DLP feature is very important to consider.
It should be able to monitor and control how employees engage with such platforms to ensure that sensitive data is not accidentally exposed to these services.
Look for a tool that:
- Detect sensitive data being shared with generative AI tools.
- Monitor copy-paste actions or prompts containing confidential text.
- Apply AI-aware policies that balance innovation with security.
Reporting and Compliance Management
DLP generates massive amounts of data about how sensitive information moves through your organisation. Reporting features turn this data into actionable insights and compliance proof.
Look for a tool that:
- Generates compliance-ready reports for frameworks like GDPR, CCPA, or HIPAA.
- Offers dashboards for data flow visualisation and policy performance.
- Provides evidence for regulators during assessments.
Discover the best GRC tools and solutions that help businesses streamline compliance, manage risk and strengthen governance effectively.
Integration and API Capabilities
DLP doesn’t exist in isolation. It needs to share data with other tools, such as SIEM platforms, endpoint protection platforms, SOAR systems, threat intelligence platforms, and identity and Access Management (IAM) tools, etc.
Strong API and integration capabilities ensure DLP becomes part of your security ecosystem.
Look For:
- Pre-built integrations with major security platforms
- RESTful APIs for custom integrations
- Webhook support for real-time event notifications
- Standardised log formats (CEF, JSON) for SIEM ingestion
- Bidirectional communication to enable automated response
Common Use Cases of DLP Software
Understanding data loss prevention use cases can help you see the real-world value of these features:
| Use Case | Description | Example |
|---|---|---|
| Intellectual Property Protection | Prevents leaks of design files or source code from R&D teams. | A tech firm blocked unauthorised source code uploads to GitHub. |
| Regulatory Compliance | Ensures data handling meets industry or legal mandates. | A hospital met HIPAA compliance by monitoring patient data transfers. |
| Insider Threat Management | Detects and prevents data misuse or theft by employees. | An employee trying to email client lists externally was stopped instantly. |
| Cloud Data Control | Monitors and protects files shared in cloud apps. | A sales team’s Google Drive folder was flagged for sensitive pricing data. |
| Third Party Data Sharing | Tracks and limits what external vendors can access. | A finance firm restricted contractors to project-specific folders only. |
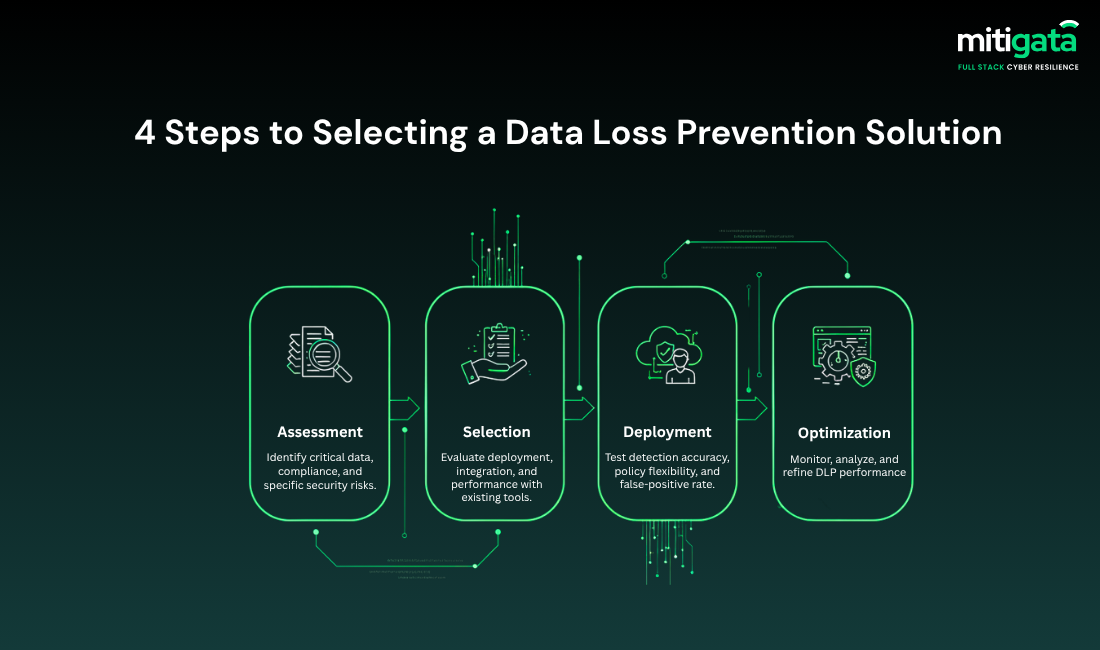
How to Choose a DLP Solution
The following are the points you need to consider while selecting the best DLP solution:
Evaluate Your Data Landscape
Determine what categories of data you need to protect, such as financial data, PII details or any other. Also, consider where it is stored (on-premises, cloud, endpoints).
Define Clear Objectives
Is your purpose to detect insider threats, protect intellectual property, or ensure compliance? Prioritise accordingly.
Evaluate Integration Capabilities
Choose DLP software that fits seamlessly with your existing tech stack such as SIEM, SOAR, and cloud apps.
Check for Scalability
Your data footprint will grow with your business. If you are investing in a DLP tool, make sure it scales across multiple geographies, departments, and platforms.
Account for User Experience
A DLP solution should help with the workflows, not interrupting them. Hence, select a solution that has clear enforcement action and minimal barriers.
Verify AI and Analytics Support
Cyberattacks evolve every day, and new threats keep coming up. Your solution should be able to use AI, ML, and user behaviour analytics to provide adaptive security.
Look for Expert Implementation Support
Even the best DLP tool fails without expert configuration. Partner with experienced providers like Mitigata who understand both technology and business risk.
Conclusion
Data is the backbone of every modern business, but also its greatest danger. Businesses require more than just firewalls and antivirus software to protect themselves against accidental leaks caused by AI tools and advanced insider attacks.
They require highly adaptable DLP solutions designed for today’s and tomorrow’s digital world. If you need a reliable partner to deploy and operate a DLP solution adapted to your needs, Mitigata provides unparalleled expertise.
Get in touch today to schedule a free DLP demo!

