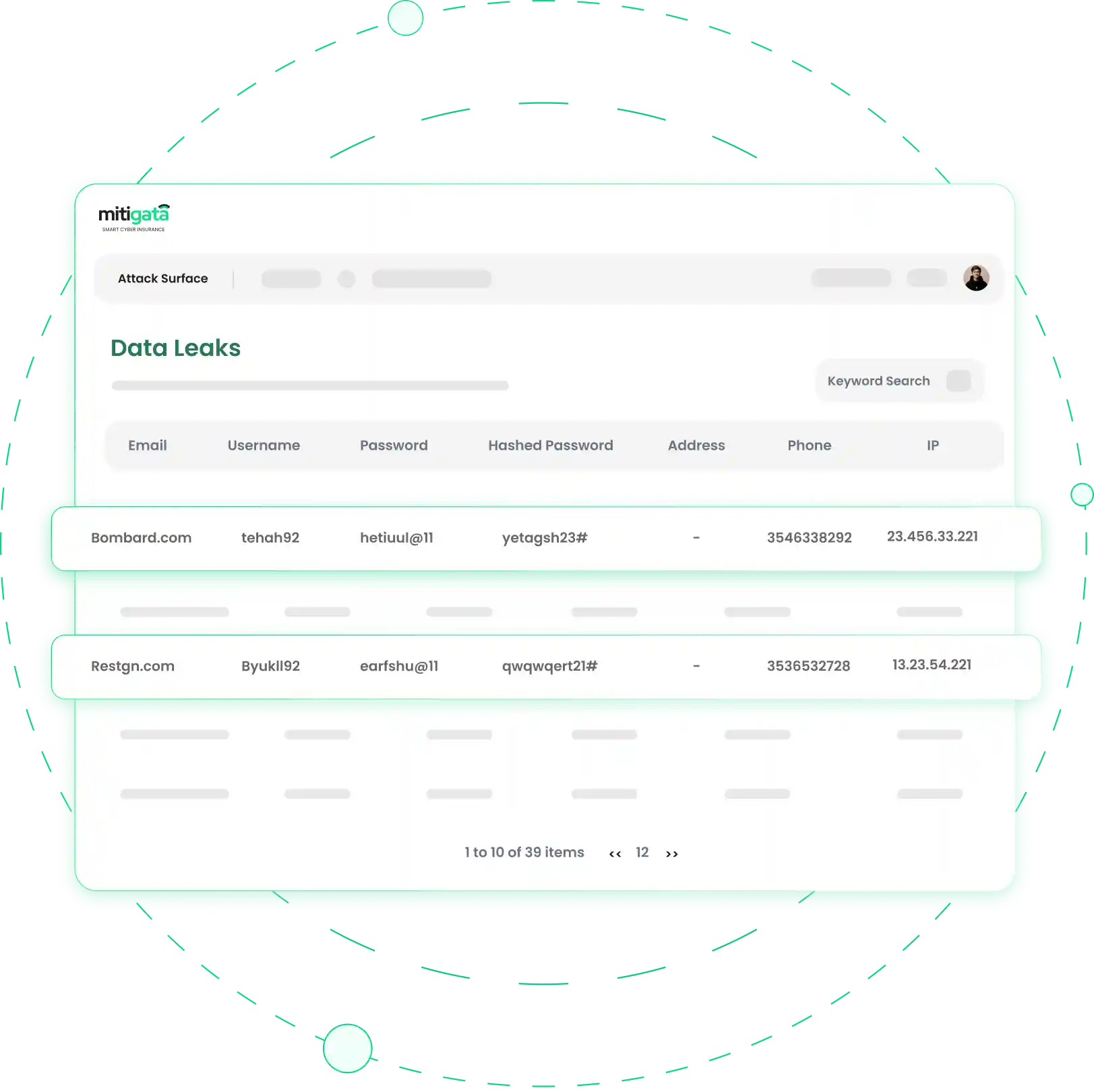
Data Leaks on Personal privacy and Data security
Data leaks in cybersecurity refer to unauthorised or unintended disclosures of sensitive or confidential information. These leaks can occur due to various reasons, and understanding them is essential for protecting data and preventing security breaches
Hacker Chatter: Dark Web Patrol Stay Ahead of Cyber Threats
Did you know your data could be lurking on the dark web? With our Hacker Charter, you can monitor if your data is being sold on the dark web. Whether it’s confidential information or personal data, you can contact Mitigata or use the Mitigata Console to delete or purchase the data to secure your company.

Strategies to Prevent
Data Leaks
Preventing data leaks in cybersecurity is crucial to protect sensitive information and maintaining the privacy and security of individuals and organisations. Here are some essential steps and strategies to help prevent data leaks
Penetration Testing
Penetration testing identifies vulnerabilities in your system, allowing for proactive remediation and enhanced security.
Phishing Simulations
Phishing simulations help educate employees and strengthen their ability to detect and avoid phishing attacks, reducing the risk of data breaches
Endpoint Security
Endpoint security solutions provide robust protection for devices and networks, mitigating the risk of data leaks and unauthorised access.
Things You
Probably Wonder
Data leaks refer to unauthorised or unintended disclosures of sensitive or confidential information, posing significant risks to personal privacy and data security.
Preventing data leaks is crucial for protecting sensitive information, maintaining privacy, and safeguarding organisations against security breaches that could result in reputational damage and financial losses.
Penetration Testing involves simulating cyberattacks to identify vulnerabilities in systems and applications. By conducting regular penetration tests, organisations can proactively identify and address security weaknesses, reducing the risk of data leaks.
Phishing Simulations involve simulating phishing attacks to assess employees' susceptibility to email-based threats. By training employees to recognize and report phishing attempts, organisations can mitigate the risk of data breaches resulting from social engineering attacks.
Endpoint Security solutions protect endpoints such as laptops, desktops, and mobile devices from cyber threats. By implementing robust endpoint security measures, organisations can prevent unauthorised access to sensitive data and mitigate the risk of data leaks.