All Industries For
Security Services
Mitigata provides security services and insurance for all industries, ensuring comprehensive protection against cyber threats.
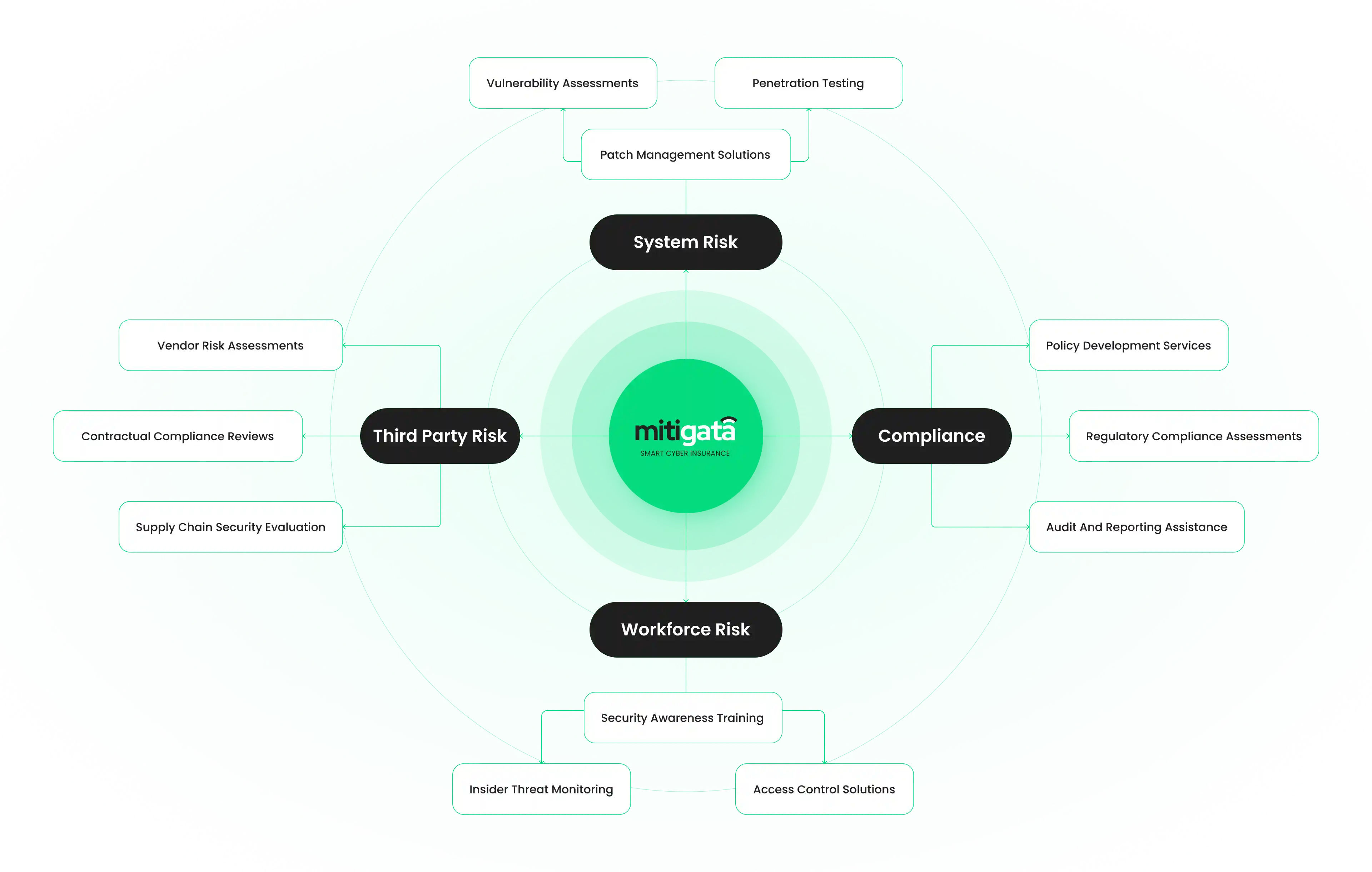
Security Services By Mitigata
Email Security
Defend against email phishing and malware attacks effectively.
Cloud Security
Protect sensitive data in cloud environments with robust measures.
Network Security
Safeguard your network infrastructure from cyber threats comprehensively.
Endpoint Security
Secure all endpoint devices against advanced cyber threats proactively.
VAPT Security
Identify and remediate vulnerabilities through comprehensive testing.

Mitigata's
SIEM Sizing Calculator
Your estimated data ingest:
0 GB
License Summary
Mitigata USPs Of Security Services
For Your Business
Things You
Probably Wonder
Common cyber threats include malware, phishing attacks, ransomware, insider threats, and denial-of-service (DoS) attacks, among others. These threats can target various aspects of a business's digital infrastructure, including email systems, cloud services, networks, and endpoints
Regulatory compliance ensures that businesses adhere to laws, regulations, and industry standards relevant to their operations. Compliance helps protect sensitive data, mitigate risks, avoid legal penalties, and maintain trust with customers, partners, and stakeholders.
Businesses can improve their cybersecurity posture by conducting regular risk assessments, implementing robust security measures such as firewalls and encryption, providing employee training on security best practices, maintaining up-to-date software and patching, and establishing incident response plans.
Employee training is crucial for cybersecurity as human error is often a leading cause of security breaches. Training programs educate employees on identifying and responding to cyber threats, practising safe computing habits, and understanding the importance of security policies and procedures.
Businesses can assess and manage third-party security risks by conducting vendor risk assessments, reviewing contractual agreements for security requirements, evaluating supply chain security practices, and establishing clear communication channels with third-party vendors to ensure compliance with security standards and protocols.
The SIEM Sizing Calculator helps estimate the resource requirements for deploying and managing a SIEM solution tailored to your organization’s needs.
The calculator analyzes key inputs like log sources, event volume, and retention requirements to provide an accurate sizing estimate for your SIEM infrastructure.
Proper SIEM sizing ensures optimal performance, cost efficiency, and the ability to handle your organization's security needs without over- or under-provisioning.