Control your Attack in Minutes
Mitigata Automated Scanning and Monitoring finds your organisational risk and shows you how to fix it. Sign up with just your email address and start controlling your attack right away
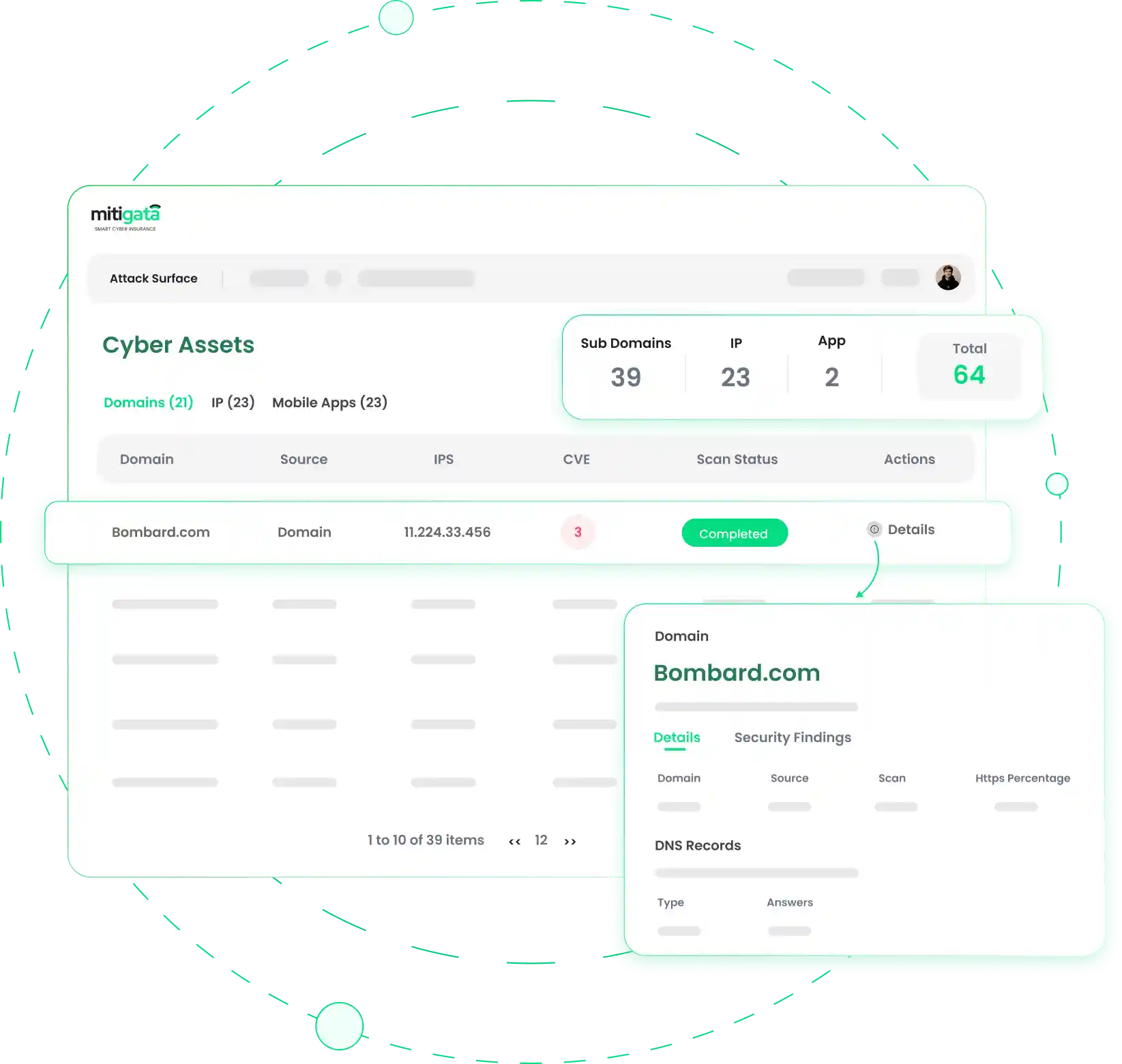
Attack surface identification and monitoring
Based on your email address alone, we will surface domains, subdomains, IP addresses associated with your organisation and create a custom view where you can explore all of these assets and understand what cybersecurity risks currently exist with them.

Vulnerability Management
Vulnerability module is a simple but exhaustive way to protect your system and its existing defences. It tracks controls, drives remediation as per SLAs, and maintains a clear audit trail. All as per your rules and policies.
Vulnerability Management
Mitigata's module ensures systematic tracking of controls, driving timely remediation, and maintaining a clear audit trail for comprehensive vulnerability management.
Scanning Integration
Seamlessly integrate scanning tools into your cybersecurity framework for continuous monitoring, while our breach response experts stand ready to contain and re-secure your network.
Resolving Threats
Mitigata's breach response experts swiftly contain cyber incidents, ensuring effective resolution and minimal disruption to your operations.
Risk Criticality Summary
Risk management is a crucial process that involves identifying, assessing, prioritising, and mitigating potential risks in order to protect an organisation's assets, reputation, and long-term viability. Effective risk management is not about eliminating all risks, but rather about understanding, quantifying, and managing them.
Things You
Probably Wonder
Attack Surface Monitoring involves continuously assessing and monitoring the digital assets, including domains, subdomains, IP addresses, and endpoints, associated with an organisation to identify potential vulnerabilities and security risks.
Mitigata's Automated Scanning and Monitoring tool identifies organisational risks based on email addresses alone. It surfaces domains, subdomains, and IP addresses associated with the organisation, allowing users to explore these assets and understand existing cybersecurity risks.
Vulnerability Management is a comprehensive approach to protect systems and defences by tracking controls, driving remediation, and maintaining a clear audit trail. It helps organisations prioritise and address vulnerabilities promptly, reducing the likelihood of successful cyberattacks.
Mitigata integrates scanning seamlessly into its platform, enabling organisations to conduct regular vulnerability assessments and identify security weaknesses across their digital infrastructure. This integration enhances visibility and allows for proactive threat mitigation.
The Risk Criticality Summary provides a concise overview of the organisation's risk landscape, highlighting critical vulnerabilities and potential threats. It helps prioritise risk mitigation efforts, allowing organisations to allocate resources effectively and reduce the likelihood of security incidents.