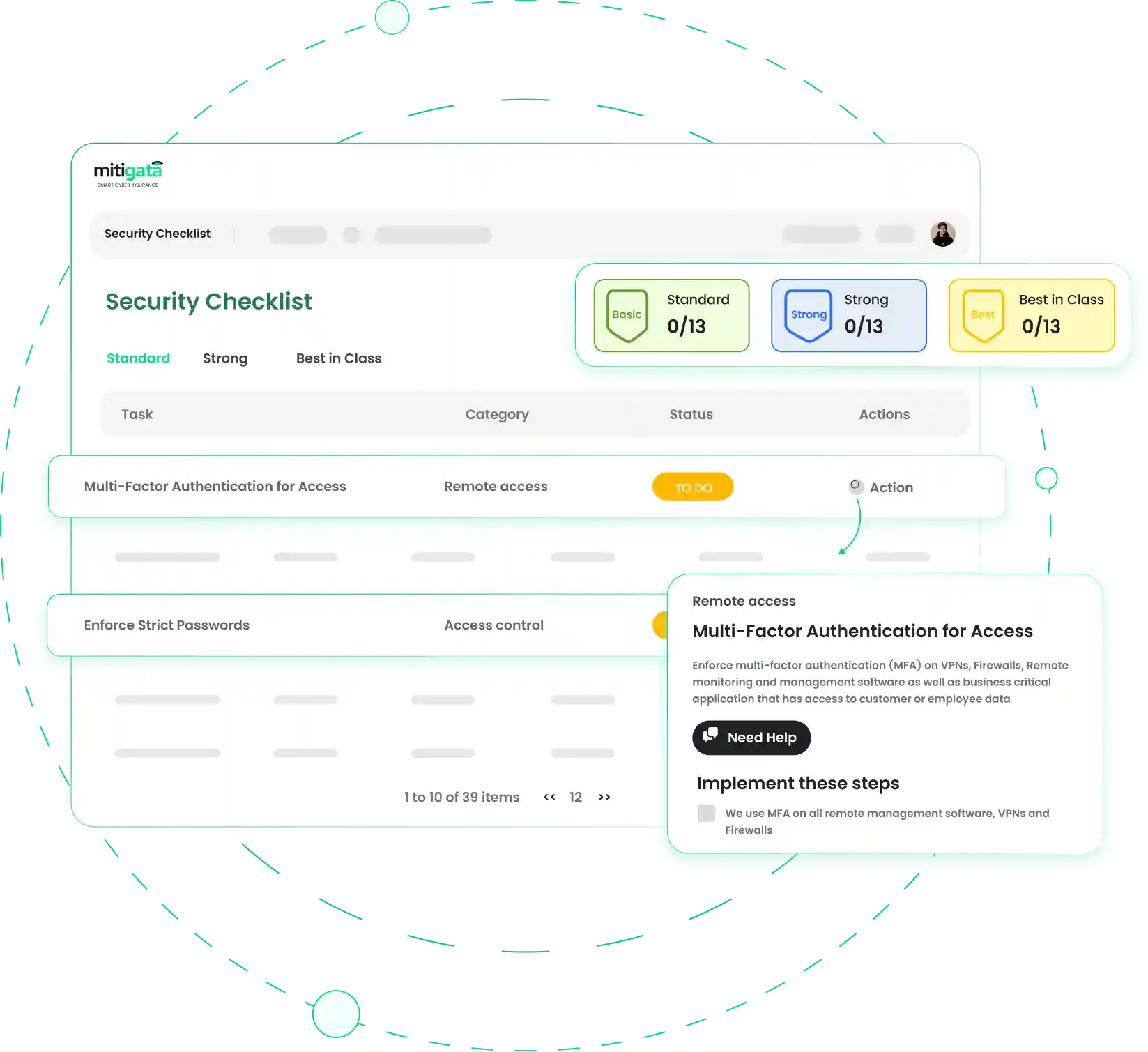
A Comprehensive Look at a Security Checklist in Cybersecurity
A security checklist is like a to-do list for your business's cybersecurity. It helps you cover all the critical areas that need attention, from securing sensitive data to preparing for cyber incidents. This checklist ensures your business is prepared to handle risks effectively.
Cybersecurity checklists are especially useful for businesses that may not have dedicated IT teams. They simplify complex security processes, making them easy to follow even for non-technical users.

Why Use a Security Checklist?
Prevent Data Breaches
Regular checks can spot weak points before hackers do.
Stay Compliant:
Ensure your business meets all required regulations.
Protect Sensitive Information:
Keep your customers’ and employees’ data safe.
Boost Confidence
Show stakeholders that your business takes security seriously.
What’s in a
Security Checklist?
Access Control
Limit access to sensitive files and systems.
Use strong passwords and change them regularly.
Enable multi-factor authentication (MFA) to secure logins.
Data Protection
Back up important data regularly.
Encrypt sensitive files to keep them safe.
Safely delete old files you no longer need.
Software Updates
Always install updates and patches for your software.
Remove any software or tools you no longer use.
Employee Awareness
Train your team to recognize phishing emails and scams.
Set clear rules for sharing sensitive information.
Vendor and Third-Party Checks
Review the security practices of vendors you work with.
Ensure third parties follow your company’s security guidelines.
Incident Preparedness
Create a response plan for cyberattacks.
Assign team members specific roles for handling incidents.
Test your plan regularly to ensure it works.
Security Checklist:
Examples of Items to Address
Vulnerabilities
Check for unpatched software, weak passwords, or misconfigured systems.
Threat Indicators
Look for signs of potential attacks, like unknown logins or strange data traffic.
Insider Threats
Watch for unusual activity from employees or contractors.
Active Cyber Insurance:
Adding an Extra Layer of Security
Mitigata’s Active Cyber Insurance works alongside your security checklist. While the checklist reduces risks, Mitigata’s insurance protects your business from financial losses if an incident occurs. Together, they form a practical solution for safeguarding your business.
Things You
Probably Wonder
A security checklist in cybersecurity helps organizations identify and implement key steps to prevent vulnerabilities. It ensures awareness, consistency, and adherence to best practices, enabling businesses to proactively strengthen their defenses against threats.
It includes tasks like managing access controls, updating software, and training employees.
Mitigata simplifies cybersecurity with tools, training, and insurance that align with the steps in your checklist.
A regular review ensures your cybersecurity measures are up-to-date with evolving threats and compliance requirements, minimizing vulnerabilities.
While it can't prevent all attacks, a checklist significantly reduces risks by strengthening defenses and improving response strategies.