Are you ready to lose ₹22 crore with just one careless click?
This is the average data breach cost in India.
In the past year alone, 67% of companies experienced a major data loss, and around 40% lost critical business information in cyberattacks.
Data is like the lifeblood for a business. It can be in the form of customer information, product designs, pricing models and financial records – all stored in emails, cloud apps and shared drives. Now, as data is so distributed, so is the risk of losing control over it.
Because companies are using more AI tools like ChatGPT and Gemini, there is a higher chance of sensitive information getting leaked.
The human element remains a challenge, but that’s where a well-implemented DLP strategy changes the game. In this blog, we’ll discover how DLP works, the latest trends shaping DLP tools, and best practices to keep your business safe.
Mitigata: India’s Only Full-Stack Cyber Resilience Company
We are partnered with 500+ OEMs, which enables us to deliver the best security solution to you as per your organisation’s risks and budget.
We’ve secured 800+ businesses across 25+ industries by offering comprehensive, intelligent protection that combines automation, policy intelligence, and cross-platform protection.
Here’s what makes Mitigata’s DLP solution stand out:
- Data Classification & Discovery
- Cross-Platform Support
- Real-time Monitoring & User Coaching
- Centralised Management via ePO
- ARM Device Support
Data Doesn’t Leak on Our Watch
We deploy fast, integrate deeply, and don’t surprise with hidden costs – just ask our 800+ happy clients.

What Is Data Leak Prevention?
To detect and prevent unauthorised transmission of sensitive information outside an organisation’s network, you need data leak prevention tools and processes.
In simple words, companies require DLP to make sure that confidential data never leaves the business environment without proper authorisation.
DLP works by understanding three critical things:
- Where is your critical data (on laptops, cloud storage, email servers, databases)
- How the data is moved by your employees (via email, USB drives, cloud uploads, copy-paste, screenshots)
- Which people can access it (employees, contractors, partners, applications)
Once DLP knows these three elements, it enforces policies that prohibit data exposure.
Explore the top DLP companies in India and learn which solutions offer the strongest protection for sensitive business data today.
| DLP Protection Layer | What It Guards | Example Scenario |
|---|---|---|
| Endpoint DLP | Devices such as laptops and desktops | Blocks copying the customer database to a USB drive |
| Network DLP | Data moving across the network | Stops sensitive emails from being sent to unauthorized domains |
| Cloud DLP | SaaS apps and cloud storage | Prevents uploading confidential files to a personal Dropbox |
| Email DLP | Incoming and outgoing messages | Flags emails containing credit card numbers |
How Does Data Leak Prevention Work?
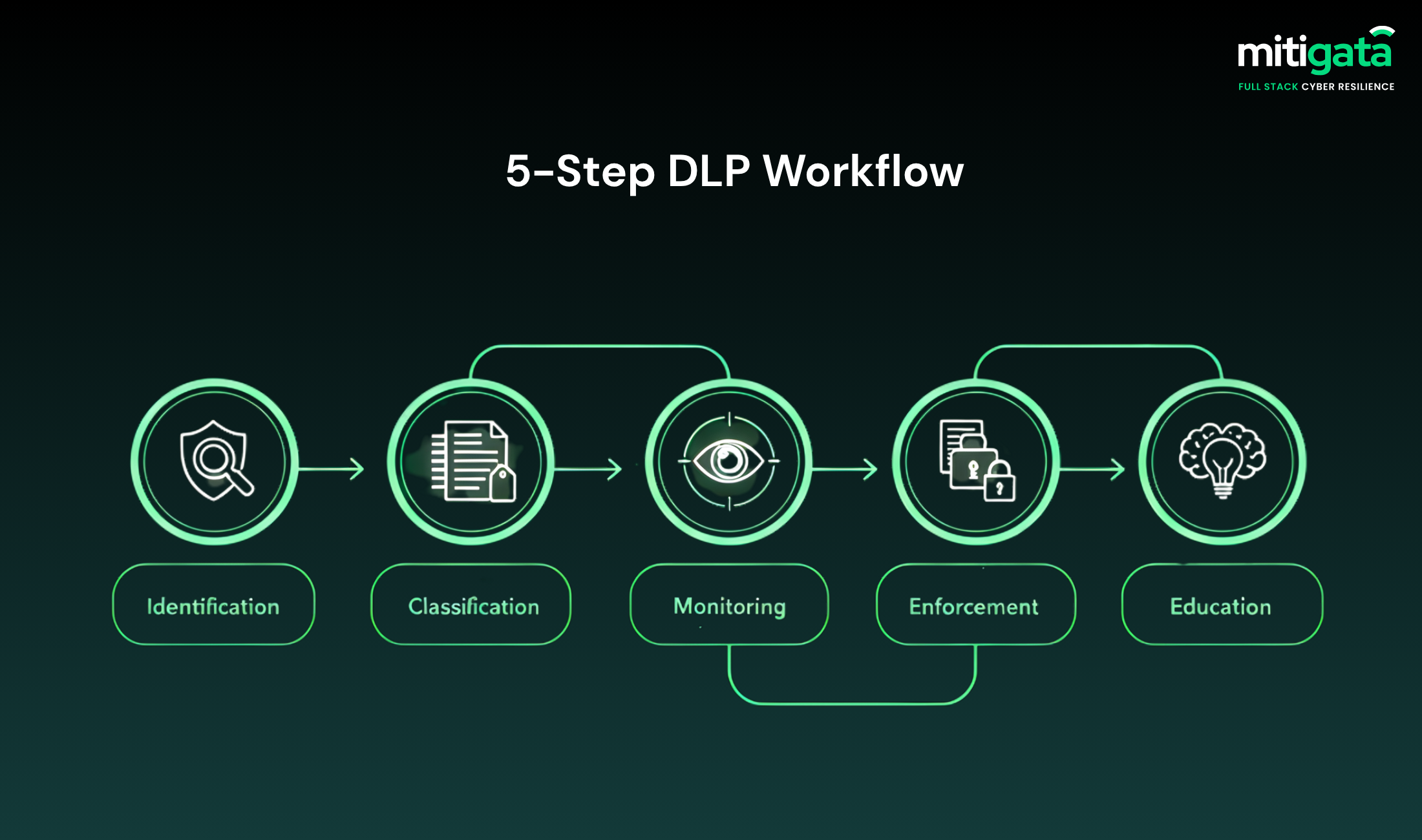
Here are the steps that help you understand better how DLP works through a layered process involving different steps, such as detection, analysis, and enforcement:
Step 1: Data Discovery and Classification
- In the first step, the tool uses predefined policies or AI models to scan all files, emails, and endpoints to identify private data. DLP uses various technologies like
- Pattern matching identifies formats such as credit card numbers (16 digits in a specified pattern), Social Security numbers, or API keys.
- Keywords and phrases: identify terms like “confidential,” “internal only,” or “do not distribute”
- AI-powered classification: Uses machine learning to identify context. (A paragraph discussing merger plans is sensitive even without clear keywords).
- Fingerprinting: Generates unique digital signatures for certain documents that can be tracked anywhere.
Step 2: Policy Creation and Enforcement
Once DLP knows what’s sensitive, it applies rules. These policies are the brain of your DLP system:
- Blocking actions: Stop a user from uploading customer data to a public cloud
- Alerting: Notify security teams when someone tries to email source code outside the company
- Encryption: Automatically encrypt sensitive files when moved to USB drives
- User coaching: Pop up a warning when an employee is about to paste PII into a web form
Your Data’s Bodyguard - On Duty 24/7
From policy to protection, our DLP solutions leave no gap unguarded, and our expert team never ghost you.

Step 3: Real-Time Monitoring
DLP monitors every event, such as employees opening any file, copying text and attaching the document to which email. It looks for any malicious activity against policies in real-time. This happens across:
- Email gateways
- Web browsers
- Endpoints
- Cloud applications
- External devices
Step 4: Incident Response and Reporting
In case the tool detects any policy violation, it records the event with full details. This step is important as it helps in refining policies & limiting threats before they escalate.
How DLP Protects Sensitive Information in Organisations
Check out some examples to know how DLP empowers companies:
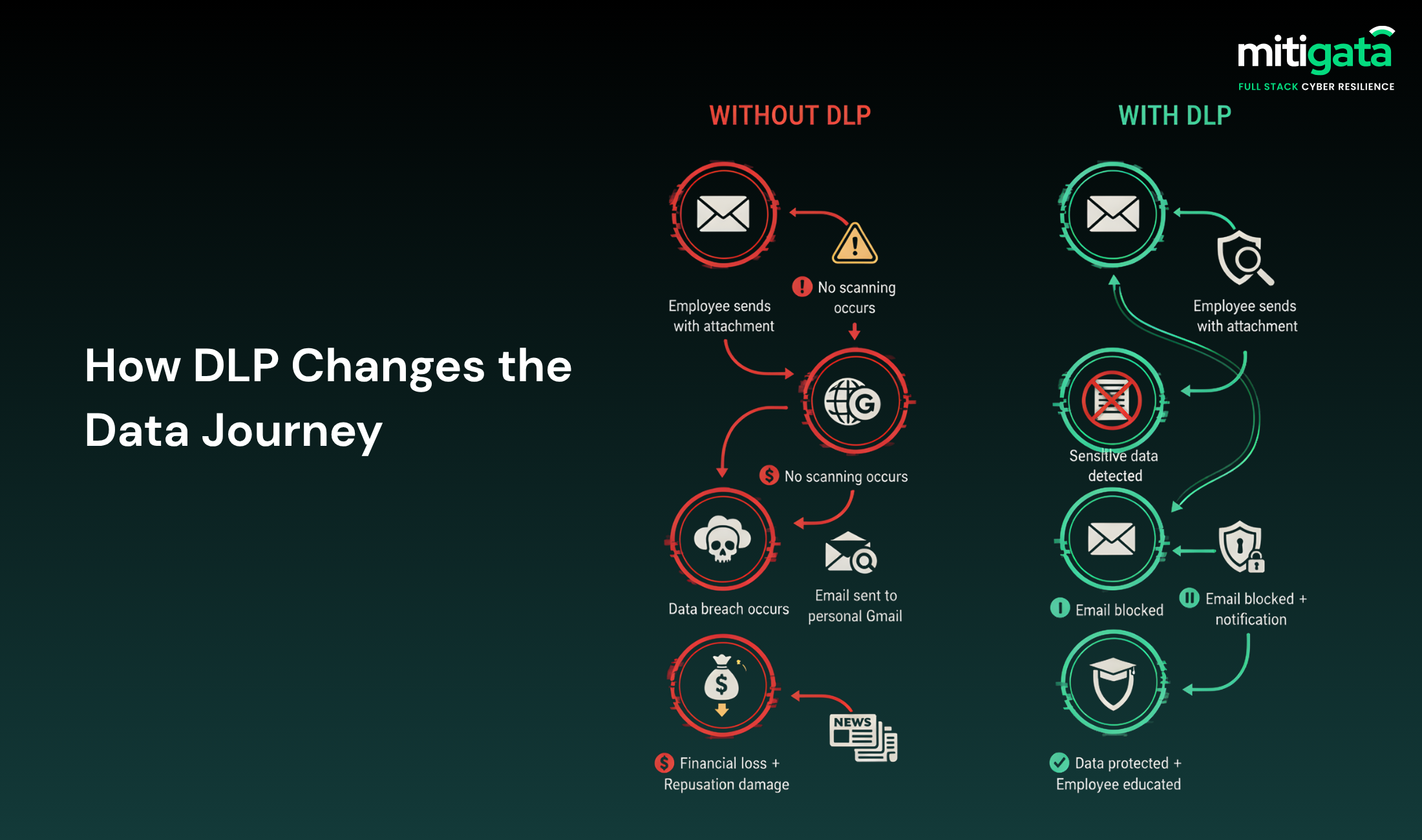
Email Security: DLP can analyse outgoing messages to prevent employees from mistakenly sending private data outside of the company.
For example, it prevents a financial analyst from emailing internal reports to a personal Gmail account.
Endpoint Control: DLP restricts users from transferring data to USB drives or using AirDrop for forbidden transfers.
As an example, a healthcare worker is unable to transfer patient data to an external hard disk.
Cloud Protection: DLP policies verify that files uploaded to cloud platforms such as Google Drive or Dropbox meet organisational standards.
Suppose you have to upload important client data to a drive, then DLP will automatically encrypt it.
Insider Threat Detection: DLP tools are good at detecting any suspicious data access or transfer among employees.
Example: Detecting large data downloads before an employee’s resignation.
Latest Trends in DLP Cybersecurity Technology
Here are the top trends driving DLP innovation in 2025:
Generative AI Integration
71% of security leaders are concerned about data leaks via generative AI applications. Employees are pasting proprietary information into ChatGPT, Claude, Gemini, and dozens of other AI tools, often without realising the security implications.
Modern DLP solutions now analyse behavioural patterns to spot abnormal data movement automatically.
Cloud-Native DLP
Today, 90% of organisations rely on cloud infrastructure. Traditional DLP, built for on-premises networks and local endpoints, struggles in cloud environments.
But modern DLP solutions now integrate directly into services like Microsoft 365, AWS, and Google Workspace for seamless policy enforcement.
Premium Coverage Only At ₹4,200/Endpoint
Advanced DLP solution with full coverage, seamless onboarding, and 24/7 support. Get your free demo NOW.

Zero Trust Integration
DLP is becoming a core component of zero-trust security models. In zero trust, you verify every user, every action, every device before allowing access.
Advanced DLP tools integrate with identity and access management (IAM), SIEM (security information and event management), and endpoint detection and response (EDR) to create a cohesive zero-trust framework.
Automated Response & Remediation
When a potential leak occurs, advanced DLP tools can instantly isolate affected files, revoke permissions, or quarantine suspicious devices.
Companies using security automation have shortened detection-to-containment timelines by months and reduced breach costs by 30%.
Understand the differences between EDR, XDR and MDR and learn which detection approach best strengthens your organisation’s security posture today.
Unified Data Security Platforms
Earlier, businesses used six different DLP tools across endpoints, email, network, and cloud. This creates gaps and inconsistent policies.
Security leaders are now moving toward unified data security platforms that combine:
- DLP (data loss prevention)
- DSPM (data security posture management)
- CASB (cloud access security broker)
- Insider risk management
By 2027, 70% of CISOs in larger enterprises will adopt this consolidated approach to address both insider risk and data exfiltration in a single platform.
Compliance-Driven DLP
Newer regulations (like India’s DPDP Act and updated GDPR frameworks) are pushing companies to adopt DLP solutions that emphasise privacy-first data handling and ethical monitoring.
| DLP Latest Trends | What It Means for Businesses |
|---|---|
| AI powered detection | Fewer false positives and smarter policy decisions |
| GenAI protection | Safe use of AI tools without data leakage |
| Cloud native DLP | Smooth, consistent protection across SaaS apps |
| Unified platforms | One consolidated solution instead of multiple tools |
| Zero trust integration | Policies adapt in real time based on behaviour and risk |
| Automated response | Instant mitigation without manual intervention |
Conclusion
It must be clear by now that data leaks aren’t always the result of hackers. Sometimes, it’s a simple mistake. But with the right Data Leak Prevention strategy, businesses can stay ahead of these risks.
At Mitigata, we provide industry-leading DLP tools that secure your data across every endpoint and network.
Contact Mitigata today to schedule your free DLP consultation and take the first step toward complete data security.

