Reports show that 3.4 billion phishing emails are sent every day.
With the introduction of AI, it is becoming increasingly more difficult for employees to identify phishing emails. A new survey found that 36% of all data breaches in 2025 happened with phishing emails. Undoubtedly, this is the #1 entry point for cybercriminals to infiltrate a company.
Additionally, 88% of cyberattacks can be traced directly or indirectly to human error.
It just takes one small mistake, such as missing an update, reusing a password, or clicking a link unintentionally, for a company’s private data to reach the dark web.
Your cybersecurity tools can minimise the impact of human mistakes, but to an extent. If you want to truly build a cyber-resilient company, start investing in online security awareness training for employees.
Mitigata: India’s Only Full-Stack Cyber Resilience Company
We are India’s only full-stack cyber resilience company, trusted by over 800 clients, from startups to Fortune 500s. Our strength lies in integrating technology + people through awareness, prevention, and resilience.
What sets us apart?
Complete Learning Framework: We create realistic simulations that mirror actual attacks your team faces daily, from spoofed domains like “gooogle.com” to WhatsApp-based social engineering.
Customisation for Every Role: Our role-specific campaigns ensure your finance team trains against invoice fraud while HR practices spotting resume-based malware.
Cost-Effective: Our training solutions are 30% more affordable than market averages.
Scalability: Our platform scales with you while meeting ISO 27001, GDPR, HIPAA, SOC 2 & other global security standards.
Train Your Workforce With India’s Leading Phishing Simulation
With 500+ businesses secured, Mitigata’s simulations offer experience-based learning, role-specific campaigns, and regular tests

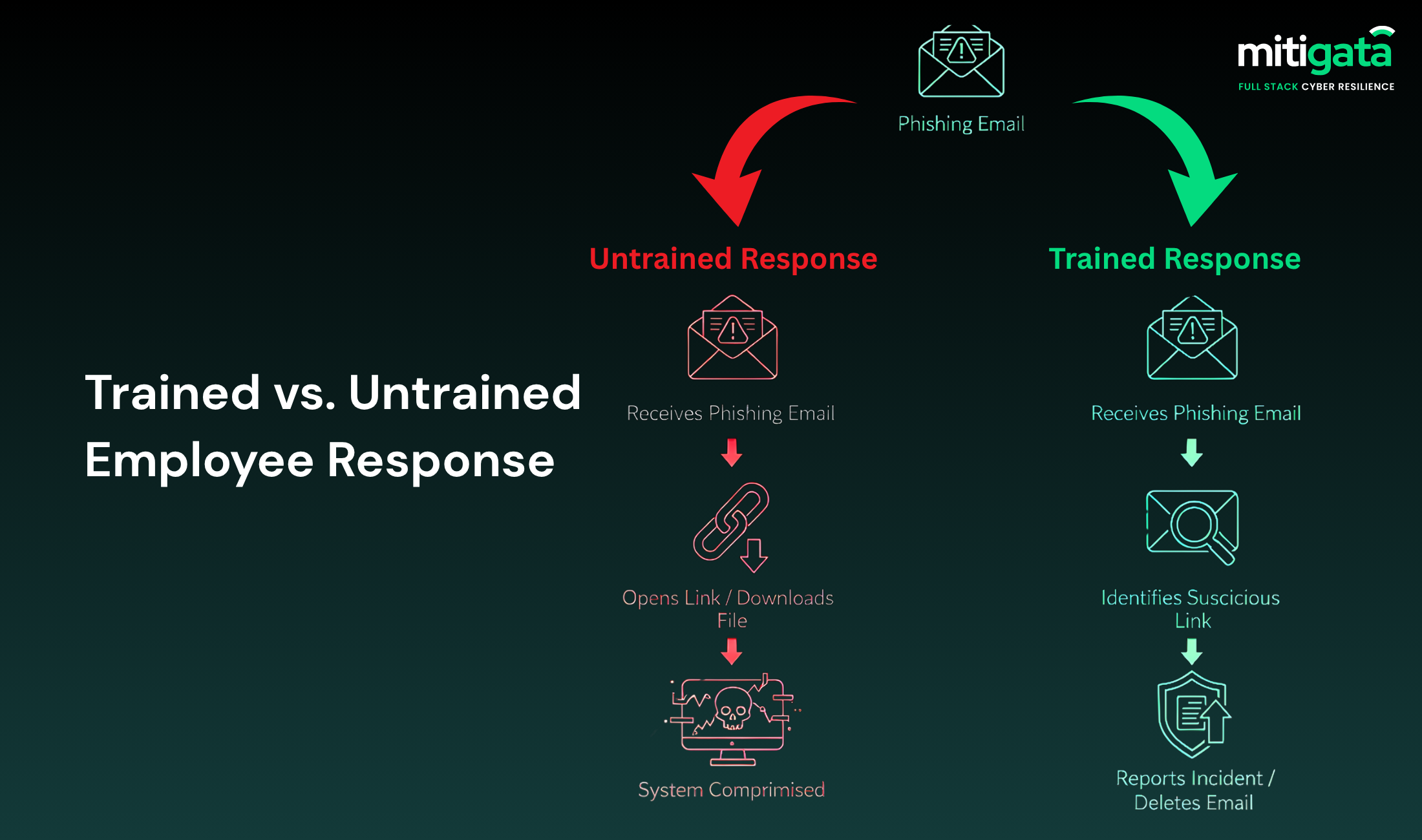
Even if a well-made phishing email, disguised as a high-priority email from the ”CEO” comes, they would’t spend a minute verifying the email address properly.
One click and you are now dealing with ransomware. Your data is lost, and so is your reputation.
Reports show 60% of security incidents occur from human error, either through phishing or social engineering attacks. The technology can only protect you up to a point, but awareness bridges the rest.
Cybersecurity awareness training has proven itself countless times. Companies that consistently train their teams see an 86% drop in phishing susceptibility, dramatically reducing both risk and recovery costs.
Core Topics Every Cybersecurity Awareness Program Should Cover
A strong cybersecurity awareness program should focus on the threats employees face every day. Covering the right core topics ensures your workforce can identify risks early and take the right actions to prevent breaches.

Phishing and Social Engineering
Train your employees all forms of phishing attacks such as email, SMS (smishing), voice calls (vishing), and even social media messages.
What to train:
- Identifying suspicious email addresses (rnicrosoft.com vs. microsoft.com)
- Spotting urgent language designed to bypass rational thinking
- Verifying requests through alternative channels
- Recognising AI-generated content that sounds too perfect
Password Security and Authentication
Weak passwords remain one of the easiest entry points for attackers. You should make sure none of your employees have passwords like “P@ssw0rd123” or “12345”.
What to train:
- Generate strong & unique passwords (use phrases instead of words)
- Using password managers and the consequences of reusing passwords
- Applying multi-factor authentication (MFA) across all accounts
- Knowledge of credential stuffing attacks
🔎 Quick Fact:
123456, password, qwerty, admin, and welcome are some of the most used passwords in 2025.
Remote Work and Device Security
With hybrid work now standard, unsecured Wi-Fi, personal devices, and shared networks are now part of your attack surface.
What to train:
- Securing home Wi-Fi networks (changing default passwords, using WPA3)
- Understanding risks of personal devices for work (BYOD policies)
- Recognising fake mobile apps that mimic legitimate software
- Keeping devices updated with security patches
- Using device encryption and remote wipe capabilities
Safe Email and Browsing Practices
Email accounts as the primary attack vector, but unsafe browsing practices are also proven dangerous.
What to train:
- Double-checking links before clicking on any URLs
- Avoiding public Wi-Fi for critical business work otherwise use VPNs
- Recognising HTTPS vs. HTTP (though attackers now use HTTPS too)
- Understanding that pop-ups asking to “update” software are often malware
- Being cautious with email attachments, especially unexpected ones
Every day, around 3.4 billion phishing emails are sent. Learn about these types of phishing emails and stay ahead of such scams.
Incident Reporting and Response
Even with perfect training, breaches can happen. Your employees need to know what to do when something goes wrong.
What to train:
- Recognising signs of a security incident
- Who to contact immediately (IT security team, manager)
- What you should avoid (like attempting to resolve it themselves)
Data Privacy and Regulatory Compliance
Teach your employees how to protect PII (Personally Identifiable Information) and comply with related regulations, such as GDPR, HIPAA, or India’s DPDP Act.
What you should educate employees on:
- Understanding India’s DPDP Act, 2025 and how it governs their day-to-day actions
- Adhering to data retention and data deletion policies
- Getting appropriate consent to collect customer information
- Understanding limitations to transferring data across borders
Discover what the DPDP Act 2025 means for your organisation and how it changes the way businesses manage personal data responsibly today.
Deepfakes, AI Manipulation, and Voice Spoofing
We all know how attackers today leverage AI to clone voices, create fake video calls, and create believable impersonations of executives.
What to train:
- Recognising signs of deepfake videos (unnatural blinking, lip-sync issues, lighting inconsistencies)
- Verifying unusual requests through secondary channels, even if they seem to come from leadership
- Being sceptical of urgent financial requests via video or voice call
- Establishing verification protocols for high-stakes decisions
Cloud and Collaboration Tool Security
Cloud-based apps like Google Workspace, Slack, or Teams are prime targets. Give examples of real incidents where sensitive files shared via open links were indexed publicly by search engines.
What to train:
- Setting appropriate sharing permissions
- Securing video conference meetings with passwords and waiting rooms
- Reviewing and revoking unused third-party app integrations
Ransomware and Malware Defence
Ransomware attacks have become a business model for cybercriminals. Training should teach how malware spreads, through malicious attachments, downloads, and even USB drives.
What to train:
- Understanding why regular backups matter (and testing if they actually work)
- Avoiding pirated software and unofficial app stores
- Recognising signs of infection (slow system, files renamed with odd extensions, pop-up warnings)
Insider Threats and Data Handling
Many times, the risk comes from a frustrated employee, a reckless contractor, or a well-meaning team member who doesn’t follow protocols.
What to train:
- Following the principle of least privilege
- Proper offboarding procedures (returning devices, revoking access)
Build a Phishing-Resistant Workforce With Role-Specific Simulations
With Mitigata’s phishing simulation, employees face realistic phishing attacks, get immediate feedback, and improve with follow-up training.

Best Practices for Delivering Effective Cybersecurity Training
Effective cybersecurity training goes beyond one-time sessions, it requires consistency, relevance, and real-world scenarios. These best practices help ensure your employees stay alert, informed, and ready to respond to threats.
| Training Topic | Key Learning Outcome |
|---|---|
| Phishing & Social Engineering | Spot manipulation cues & verify sender authenticity. |
| Password Security & MFA | Create strong passwords & enable MFA. |
| Safe Internet & Email Use | Identify malicious attachments/URLs. |
| Remote Work Security | Secure connections & endpoint hygiene. |
| Insider Threats & Data Handling | Handle data per classification & least privilege. |
| Ransomware & Malware Awareness | Recognise early signs of compromise. |
| Cloud & Collaboration Tools | Secure file sharing & access controls. |
| Incident Reporting & Response | Know when & how to escalate incidents. |
| AI Threats & Deepfakes | Verify voice/video authenticity. |
| Data Privacy & Compliance | Identify & protect PII correctly. |
Avg. Cost of Business Email Compromise (BEC)
Scam is $4.89 million
From HR to finance, Mitigata’s tailored phishing campaigns make your teams smarter and ensure that they never miss the red flag.

Best Practices for Delivering Effective Cybersecurity Training Courses for Employees
Here are proven strategies to maximise engagement and retention:
- Personalise by role and risk level
- Use real-world scenarios from your industry
- Keep It Continuous
- Foster a security-first culture
- Track Metrics & Improve
- Update Training with Emerging Threats
- Gamify the experience
Looking to buy cyber insurance? Read this ultimate guide to cyber insurance cost and premiums
Conclusion:
From phishing awareness to incident response, all the topics are equally important to build a security-aware workforce. However, remember that information alone does not influence behaviour. Your training should be constant.
Today, where AI can create millions of phishing emails and billions of malicious emails are sent daily, the only defence that will always be successful is human intelligence.
Partner with Mitigata and allow us to support you in building resilient teams capable of recognising, resisting, and reporting cyber threats before they develop into a significant problem.
Contact Mitigata today!

