“As of 2024, we are witnessing cyber threats evolving faster than our defenses can adapt.” This statement from a recent CERT-In report captures the urgency of a changing situation. Cyber activities were on the rise, leading to enterprises and individuals needing to outsmart these emerging threats worldwide, including India. The rise in sophistication of cybercrime and the number of financial losses increase the imperative need of every organization to understand the risks and well-equipped superior insurance solutions that mitigate the financial and operational impact.
1. Ransomware 3.0: The Evolution of Extortion
Ransomware is an aggressive threat that has bothered the authorities for years, but 2024 will be the era of what experts have coined “Ransomware 3.0.” Such a new wave of ransomware will be more aggressive as it already targets data encryption and exfiltration with threats to release sensitive information if the ransom is not paid.
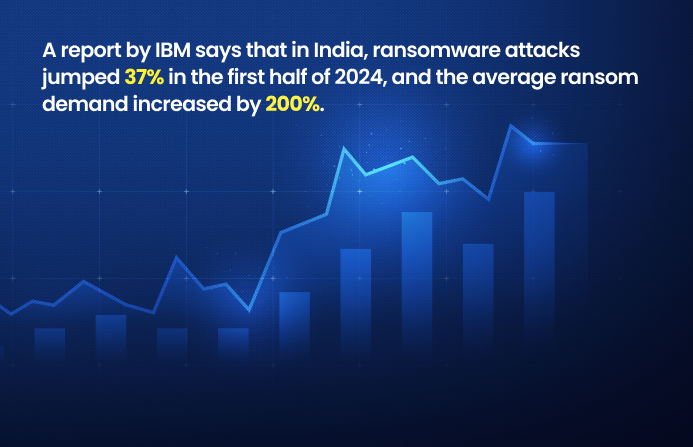
A report by IBM says that in India, ransomware attacks jumped 37% in the first half of 2024, and the average ransom demand increased by 200%.
For example, the most notable was a leading Indian e-commerce site breached via a double extortion attack in March 2024. Some of its critical business data were encrypted, sensitive information regarding its customers was exfiltrated, and a multi-million-dollar ransom was demanded. Even with superior cybersecurity measures, the company failed to defend itself against this breach and eventually paid the ransom to avoid further damage to its reputation.
Insurance Solution: Cyber Extortion Coverage
With increasingly advanced forms of ransomware, cyber insurance companies have evolved to include coverage and remuneration for cyber extortion. This may include the cost of ransom negotiations, payment of the ransom if demanded, and damage mitigation from the resultant data leak fallout. Most recently, several policies have also included crisis management and public relations support to help navigate the commonly encountered reputational damage.
2. Deepfake Scams: The New Face of Fraud
Deepfakes have graduated from becoming a buzzword to assuming an actual threat in the virtual space. In 2024, India saw an alarming rise in fraud cases in which cyber fraudsters created lifelike audio or video replicas of key managers to make the latter authenticate a transaction. These scams are so sophisticated that even the most seasoned professionals become victims of them and thus incur immense financial loss.
Last year, a large multinational company in Hong Kong fell prey to a deepfake scam; it reportedly lost 25 million dollars, around ₹207 crores, in the fraud. During a video conference, the fraudsters used highly developed deep fake technology to impersonate the company’s CFO. Because of this, the employee, believing the instructions came straight from the CFO, gave the go-ahead to 15 large transactions to different bank accounts. This scam remained ignored until the day the employee began to feel suspicious about it, and he reported the case to the headquarters. This case depicts the level of complexity to which deepfake technology is exposed, causing substantial financial losses.
Insurance Solution: Coverage of Social Engineering Fraud
Traditional crime insurance policies have become more advanced today, including losses from social engineering attacks, especially deepfakes. Such cover will be of great significance to businesses since it recovers the lost money through fraudulent transactions that were granted due to deceitful means. In addition to monetary compensation, the packages usually allow the recipient to consult experts on how to rectify their internal control and employee training so that such scenarios do not occur again.
3. IoT Vulnerabilities: The Weakest Link in Security
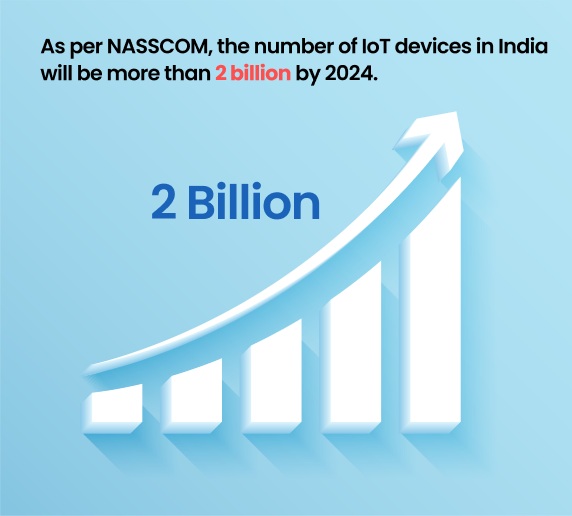
IoT devices have been proliferating across the globe, and as one may logically predict, the risks associated with their proliferation have also increased. As per NASSCOM, the number of IoT devices in India will be more than 2 billion by 2024. However, these devices’ proliferation far outstrips the development of appropriate security mechanisms; hence they are the prime target for cybercriminals.
One scary incident that rattled the world in 2024 was a hacking incident in which hackers exploited vulnerabilities of IoT devices that were compromised in a European country. Hackers exploited weaknesses in smart grid infrastructure. The attack focused on the connected IoT system managing the electricity distribution infrastructure, thereby causing power outages in several cities of the region. Hackers got access through the system by hijacking unsecured IoT devices that controlled the energy grid.
Apart from exposing the electricity supply, the attack affected different services: transportation, healthcare, and emergency response systems that only work through electricity. Thus, the attack showed vulnerabilities in IoT deployments, especially in the world’s critical infrastructure, with the urgent need for more robust security mechanisms and protocols to protect these systems from cyber threats.
Insurance Solution: IoT Liability Insurance
The insurers have developed IoT-specific liability policies because the risks are rising, and they are trying to cope with the unique challenges accompanying those devices. Some of the typical covers accompanying such a policy are security breach cover, data loss, and business interruption consequences due to such a breach. Companies with extensive IoT networks must be insured over the implications of an attack that may hit them successfully.
4. Supply Chain Attacks: The Domino Effect
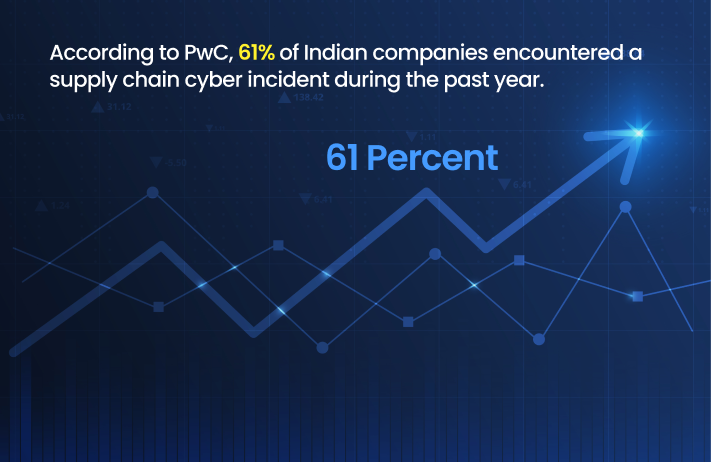
Supply chain attacks have proved to be cybercriminals’ favorite when they target the depth of connectedness in modern business. By 2024, they will become more frequent and sophisticated, targeting individuals and less significant suppliers to reach large organizations. According to PwC, 61% of Indian companies encountered a supply chain cyber incident during the past year.
In March 2022, a supply chain attack forced the world’s largest car manufacturer, Toyota, to stop all operations within its local plants in Japan. The halt adversely affected 14 plants and 28 production lines, with an estimated loss of 13,000 vehicles for one day. This was due to the hacking of one of Toyota’s suppliers, Kojima Industries, which supplies the automaker with plastic parts and electronic components.
The cyber attackers targeted Kojima Industries’ IT system, and this disturbance in their system streamed to Toyota, temporarily halting it. It just goes to show how vulnerable the supply chain in manufacturing can be, for just one point of failure can cause an entire process to go into a cascading effect.
Insurance Solution: Supply Chain Cyber Insurance
Supply chain cyber insurance is designed to cover the loss that emerges due to third-party vendor and partner risks. Such risks describe the loss resulting from business interruption, which probably arises from an attack because it brings one’s supply chain to a standstill. Such policies usually encompass different expenses related to breaches, including charges for notification, legal fees, and fines collected by regulatory bodies. This type of insurance becomes the primary mitigator of a possible cascading effect from a supply chain cyber attack for a company that highly relies on third-party suppliers.
5. AI-Powered Attacks: The Next Frontier of Cybercrime
This is the rise of AI in all aspects of the industry, and cyber criminals are utilizing their other arms. In 2024, AI-driven attacks will be much more common. The enemy will use algorithms derived from machine learning algorithms to deploy targeted, adaptive cyberattacks against targets. These cyberattacks are difficult to detect and nearly impossible to defend against because their assault method changes based on the target’s defensive measures on the fly.

In 2024, it was observed that a very critical cyberattack initiated by AI in India targeted the All India Institute of Medical Sciences, Delhi. This happened after one notable big breach in 2022 and created a more sophisticated use of AI to enhance the effectiveness of an attack. Penetrating the system of AIIMS Hospital with encryption of a huge amount of data demanded a ransom for the release of that encrypted data. The financial loss is also unknown, but the attack’s severity touched not only the operational disruption but also the potential ransom demand.
This is a great example of how cybercriminals manage to utilize AI to accomplish highly sophisticated and impactful attacks, especially on critical infrastructures like healthcare institutions. The attack demonstrated that the dynamically changing threat landscape requires much stronger cybersecurity measures to stay ahead of it.
Insurance Solution: AI-Cyber Defense Insurance
In response, insurers are now offering AI cyber defense policies for losses suffered due to AI attacks. Clients can also access sophisticated threat detection and response services using AI to stay ahead of the ever-evolving cyber threat landscape. These policies help cover expenses for investigating and mitigating damage from such attacks.
Boost Your Cyber Security with Solutions by Mitigata

Even with insurance, actual proactive measures prevent the potential risks that these emergent threats may bring. These are some of the leading solutions that Mitigata has for securing your organization:
1. Bug Bounty Program: Enlisting Ethical Hackers to Identify Vulnerabilities
With increasingly sophisticated cyber threats, it becomes quite valuable to have a team of ethical hackers who can help identify vulnerabilities within your system. In its Bug Bounty Program, Mitigata connects organizations to a community of skilled ethical hackers who constantly monitor and report security flaws. This proactive approach ensures that businesses identify their weaknesses before exploiting them maliciously.
2. Hacker Chatter: Monitoring the Dark Web for Threats
The dark web is the breeding ground for all cybercriminal activities, and your data might already be exposed there. Mitigata’s Hacker Chatter service offers a solution that involves continuous monitoring of the dark web. This service notifies your company if its data is being sold or discussed in a dark web forum. Then, you can take appropriate action, whether it is securing the data or removing it from circulation.
3. ExplainMyPolicy: Explain Your Insurance Coverage
Insurance policies are mainly full of jargon, making it confusing to businesses, thereby knowing what they cover. Mitigata’s product is called ExplainMyPolicy. The tool breaks down your policy in plain, understandable language and compares it to other policies to get the best coverage based on your needs, thus making informed decisions.
4. Phishing Simulation: Get Your Team Ready To Fight The New Threats
Phishing is still the most well-known attack vector, while cybercriminals always invent innovative schemes. Mitigata’s course in Phishing Simulation will better prepare your organization to be one step ahead by offering education on how employees should be attentive and react to phishing attempts. The course contains live scenarios, such as Microsoft’s outage scam, so your team will be ready to handle all of them.
The Need for All-Inclusive Cyber Insurance

With cybercriminals’ sinister machinations, Indian businesses have to be informed and protected against cyber threats. The traditional, old-fashioned mode of cybersecurity, in place of the continuously evolving cyber threats leveraged today by cybercriminals, has become obsolete. And so, with this said, comes all-encompassing cyber insurance with financial protection in the box and expert resources and services to appropriately respond to cyber incidents in organizations.
With all this in mind, Mitigata proudly boasts excellent innovative solutions and profound cyber risk management expertise at the forefront of helping businesses navigate this complex, rapidly changing landscape. Is ransomware threatening to knock out your emails and interrupt critical business operations, or are deepfake scams, vulnerable IoTs, supply chain attacks, and AI-powered cybercrime threats making it difficult for your company to feel safe?
Then, there is Mitigata insurance with tailored protection for the kind of risk you are experiencing.
By partnering with Mitigata, you ensure that your business is prepared to face emerging cyber threats and best prepared for the quickest recovery and least damage to your operations and reputation. Don’t wait until it’s too late—secure your future today through comprehensive cyber insurance solutions at Mitigata.

