Access control errors and weak identity solutions have become among the main causes of data breaches in 2025. And 2026 is not going to be different!
The effort to manage digital identities and user permissions provided by enterprise applications becomes more difficult as businesses increase the number of applications their users access.
The best identity and access management software has become important for businesses these days.
This guide highlights the top IAM tool providers that will help you simplify user access, automate account provisioning, and stay compliant.
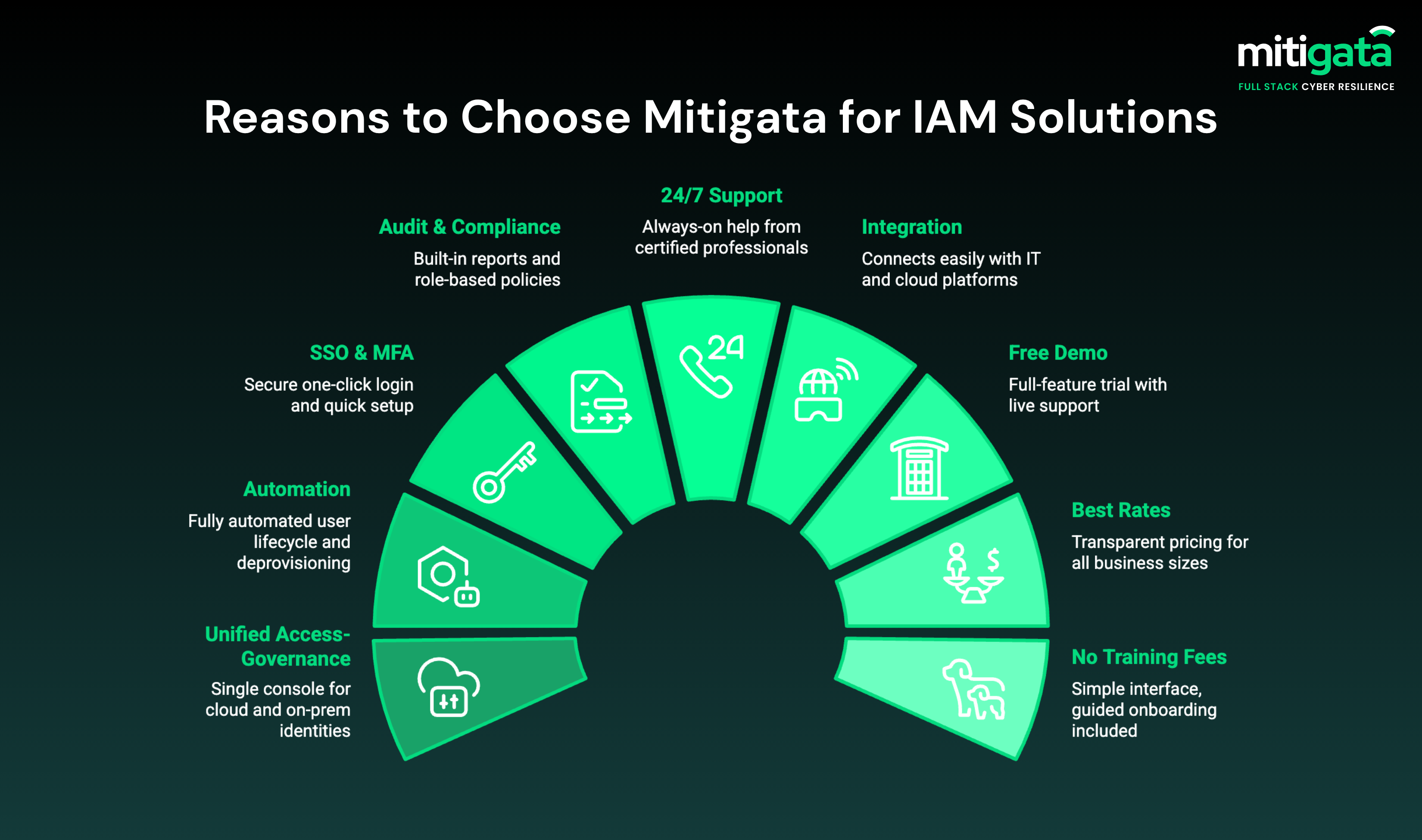
Why Businesses Choose Mitigata for IAM Services
Mitigata is India’s leading cyber resilience company, securing 800+ businesses across 25+ sectors. We are partnered with leading OEMs and offer you the best identity access management solution as per your needs.
What do you get with us:
- Unified access-governance platform
- Automation of user lifecycle & deprovisioning
- Single sign-on (SSO) + strong MFA + smooth onboarding
- Audit-ready reporting + role-based policy templates + compliance tracking
- 24/7 support from experienced professionals
- Smooth integration with existing security systems
- Free demo
- Best market rates
- No extra training fees
What Is IAM (Identity and Access Management)?
IAM, or Identity and Access Management, is a security framework that determines how users identify and access data, systems, and networks in an organisation.
A strong identity management system determines who has permission to log in, what they can access, and when to terminate access.
Don’t fall for email traps. Read our guide on common phishing attacks and how to prevent them.
Top 5 Identity and Access Management Tools
The following are the best IAM tools that are adopted by top teams to manage permissions and keep things in line without slowing down operations.
Microsoft Entra ID (previously Azure AD)
Microsoft Entra ID is among the most well-known identity and access management solutions for organisations around the world. It provides organisations with the ability to manage access, secure user identities and simplify authentication on hybrid and cloud platforms.
Entra was developed with scalability and compliance in mind, making it easy to govern identity while lowering the risk of unauthorised access.
Key Features:
Single Sign-On (SSO): Enables users to access all applications with a single secure login.
Multi-Factor Authentication (MFA): Adds an extra verification step to protect user accounts from unauthorised access.
Conditional Access: Applies access controls based on user risk, location, or device type.
Privileged Identity Management (PIM): Provides temporary and monitored admin access to minimise privilege abuse.
Identity Governance: Streamlines user access reviews and automates onboarding workflows.
Lifecycle Management: Simplifies adding, updating, and removing users as roles change.
External Identity Support: Manages and secures access for external partners and guests.
Hybrid Integration: Connects cloud and on-premises systems for unified identity control.
Choose Microsoft Entra ID with Mitigata and benefit from best-in-class pricing, quick activation, and 24/7 support coverage. Book now
Gain Full Visibility Into Who Has Access to What
Manage identities, permissions, and compliance effortlessly with IAM – fast deployment, minimal maintenance, maximum protection.

Okta Identity Cloud
Okta offers a leading identity-and-access management platform that secures user, partner, and AI agent identities across cloud and on-prem applications. It simplifies workforce and customer access while managing multiple identity types and environments.
Key Features:
API Access Management: Controls API security and permissions easily.
Adaptive Multi-Factor Authentication (MFA): Context-based verification for stronger security.
Lifecycle Management: Automates user creation, updates, and removal.
Universal Directory: Centralised profile management for all users.
Single Sign-On (SSO): Secure one-click access to all business apps.
Integration Network: Connects with 7,000+ apps for seamless workflows.
Zero Trust Access: Continuous authentication for users and devices.
Passwordless Authentication: Enables secure and quick login options.
Access Okta Identity Cloud at exclusive Mitigata prices, backed by 24/7 customer assistance and easy onboarding. Book now
RSA ID Plus
RSA ID Plus offers flexible identity and access management for cloud, hybrid and on-premises deployments, helping organisations choose authentication methods, manage governance, and maintain identity reliability across diverse networks.
Key Features:
Risk-Based Access: Adjusts security controls dynamically per user risk.
Multi-Factor Authentication (MFA): Provides strong authentication across all devices.
Identity Governance: Automates compliance and user access certification.
Single Sign-On (SSO): Simplifies access across apps with one credential.
Hybrid Deployment Support: Works across on-prem, private, and public clouds.
Analytics and Reporting: Provides visibility into access patterns and anomalies.
Secure API Access: Protects API calls with identity context.
Integration with SIEM: Enhances monitoring through centralised alerts.
Buy RSA ID Plus via Mitigata to unlock expert-backed support, smooth integration, and the most cost-effective pricing plans. Book now
CyberArk Identity Security
CyberArk’s reputation as a top identity management solution provider has made it one of the most preferred companies in this area.
Characteristically, focusing on the top account protection, their Identity Security Platform secures human, machine, and AI identities through smart privilege controls, strong governance, and threat protection.
Key Features:
Least Privilege Access: Users get only the minimum access needed, with just-in-time elevation and no standing privileges.
Privileged Access Management (PAM): Privileged access is managed across cloud services, developers, and non-human identities.
Behaviour-Based Threat Detection: Sessions are monitored for abnormal behaviour with instant response to threats.
Identity Lifecycle Automation: Onboarding, offboarding, and access reviews are automated through modern governance tools.
Machine Identity and Secrets Security: Service accounts and automation credentials are secured and tightly controlled.
AI-Driven Governance: AI automation streamlines policy management and reduces manual security work.
AI Agent Privilege Controls: Access, session control, and compliance are extended to AI agents using these services.
Get CyberArk Identity Security at the best market rates with Mitigata – plus 24/7 support and seamless deployment assistance. Book now
Secure Every Login, Simplify Every Access
Get an IAM solution built for your workflows – flexible, scalable, and backed by 24/7 assistance without extra setup or training costs.

Ping Identity
Ping Identity is another well-known IAM software. It offers single sign-on, multi-factor authentication and advanced access policies for the workforce, partners and customers.
Key Features:
Single Sign On (SSO): Simple app access using SAML, OAuth, or OpenID Connect.
Adaptive MFA: Adjusts authentication based on device, IP, and user behaviour.
Passwordless Authentication: Uses FIDO2 keys, biometrics, or push notifications for quick login.
Identity Orchestration: Builds authentication flows with an easy no-code interface.
Adaptive Access Policies: Applies access rules based on real-time risk and user context.
Directory and Provisioning Integration: Connects to directories via LDAP and SCIM for smooth provisioning.
Enterprise Workstation MFA: Adds MFA to workstation and VPN access through Enterprise Connect.
Risk Analytics Dashboard: Shows authentication patterns, anomalies, and access risks.
Get enterprise-grade identity access protection with Ping & Mitigata, along with complete implementation guidance for your team. Book now
Top IAM Tools Comparison
This brief comparison of top identity and access management (IAM) tools will help you make the right decision:
| IAM Solution | Best For | Limitations |
|---|---|---|
| Okta | Cloud-first IAM | Pricing increases with scale |
| Microsoft Entra ID | Microsoft-centric environments | Less flexible outside the Microsoft stack |
| CyberArk | Privileged Access Management (PAM) | Complex setup |
| Ping Identity | Hybrid and large enterprise IAM | Technical deployment |
| RSA ID Plus | High-assurance authentication | Slower innovation |
Simplify IAM Integration Across Cloud and On-Prem Systems
From onboarding to offboarding, Mitigata ensure your organisation stays secure with automated controls and continuous threat visibility.

Conclusion
Leaders like Okta, Microsoft Entra ID, CyberArk, Ping Identity and RSA ID Plus continue to set the standard with strong authentication, access governance and threat prevention capabilities. The best IAM tool for your business depends on your environment, user flows and security maturity.
Mitigata can help you access these industry-leading IAM solutions at discounted rates, along with guidance to ensure you pick the right fit.
Contact Mitigata today for your free IAM demo!

