Every login of your company holds a high risk of threat actors. As businesses scale and as digital tools are adopted, it becomes more challenging to track who has access to what.
Even a single unchecked permission, or something as simple as a credential shared over email, can expose sensitive data.
Identity and Access Management (IAM) tools were developed to solve just this problem – reducing friction and simplifying access to various resources while maintaining accountability across systems.
In this blog, we will guide you through the top features to look for in the best IAM tool and the common mistakes to avoid.
Why Businesses Choose Mitigata for IAM Services
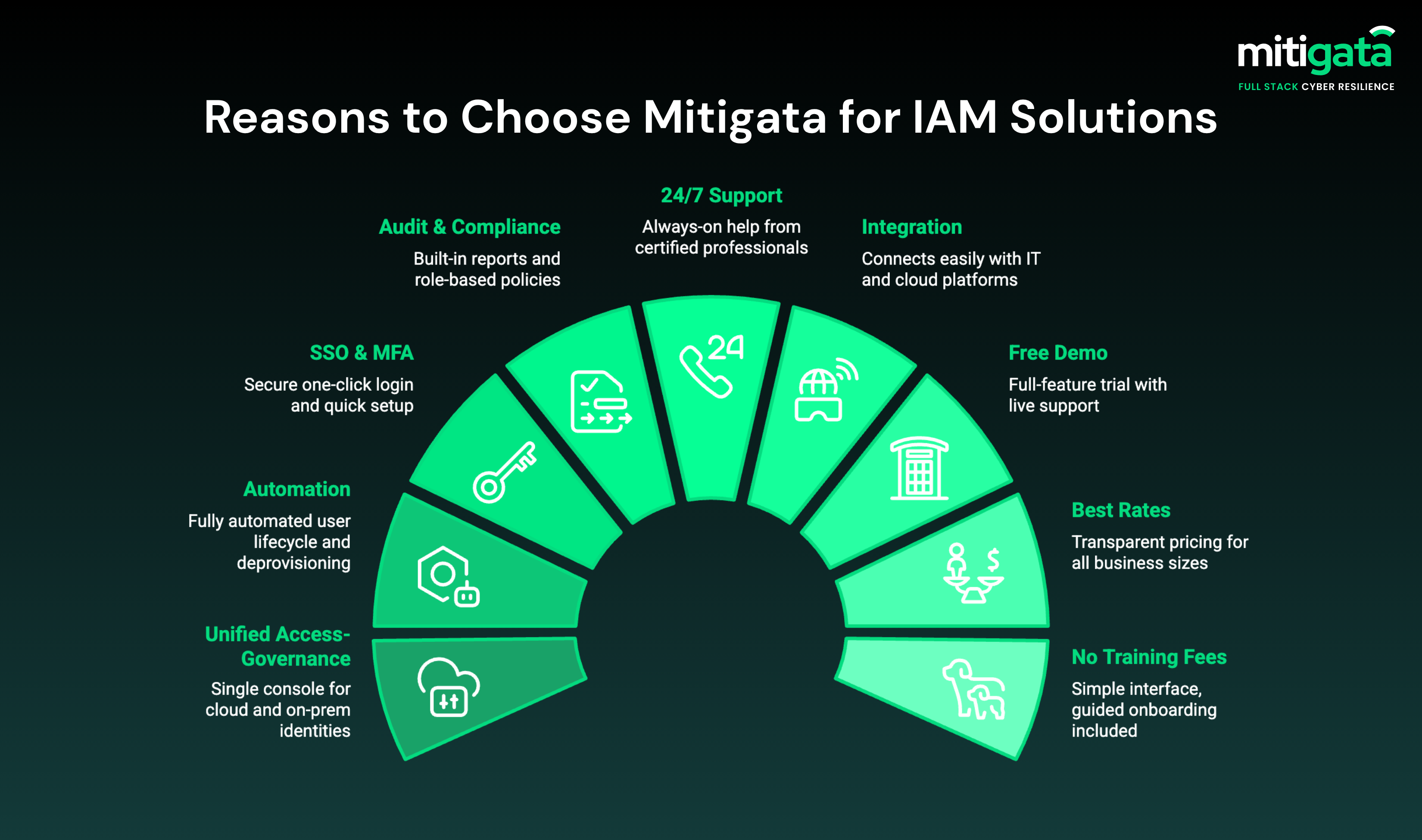
Mitigata is India’s leading cyber resilience industry, supporting more than 800 businesses across 25 sectors. We partner with leading OEMs and offer you the best identity and access management solution at the best rates.
What do you get with Mitigata?
- Unified access-governance platform
- Automation of user lifecycle & deprovisioning
- Single sign-on (SSO) + strong MFA + smooth onboarding
- Audit-ready reporting + role-based policy templates + compliance tracking
- 24/7 support from experienced professionals
- Smooth integration with existing security systems
- Free demo
- Best rates
- No extra training fees
If you’re looking for India’s most trusted Anti-Virus Software, check out this expertly curated blog.
Insurance That Watches, Warns, and Works When You Need It.
Get the most value for every rupee – comprehensive protection, 24/7 support, and access to your personalised cyber risk dashboard.

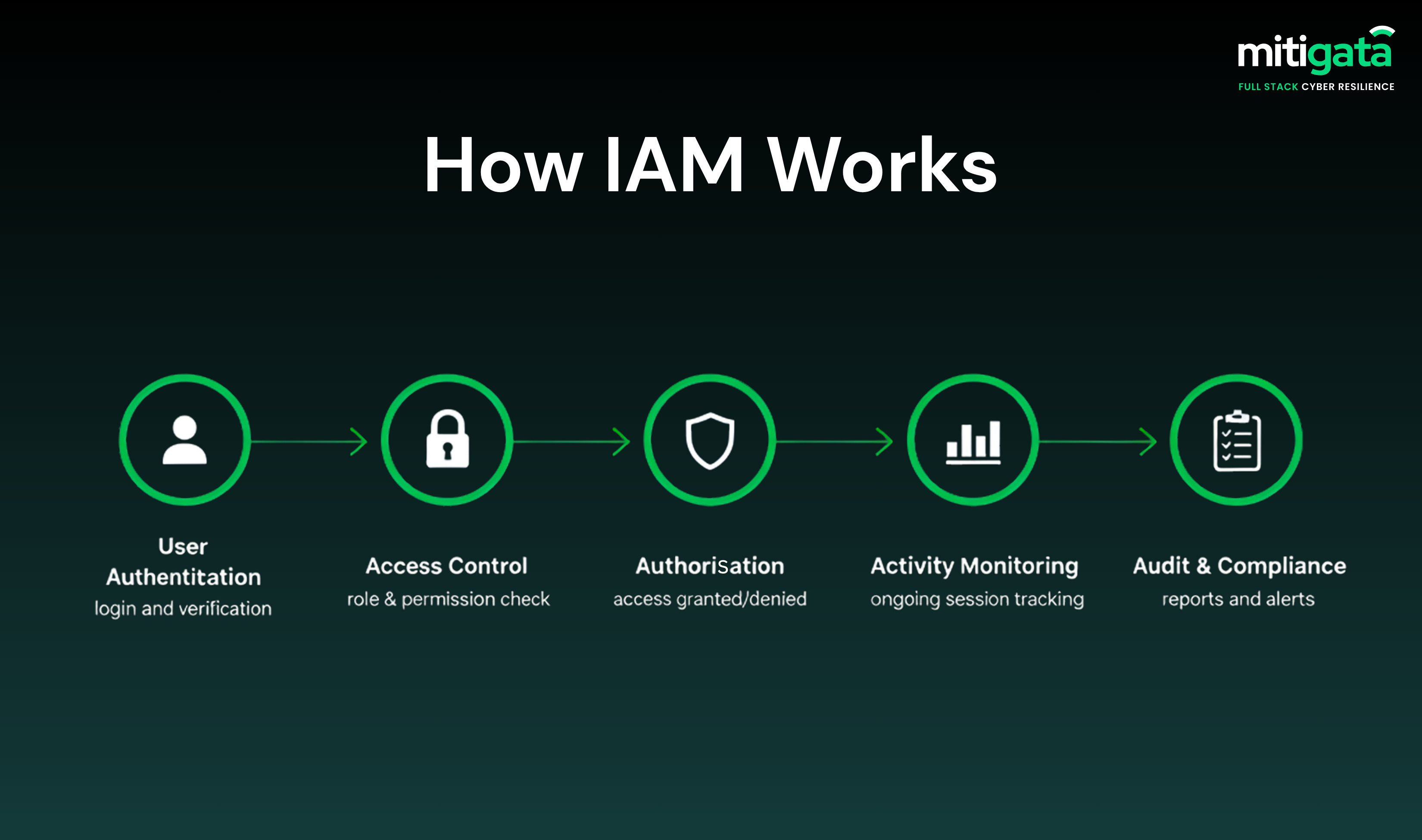
What Is Identity and Access Management (IAM)?
IAM determines who has access to specific data, networks, and tools in an organisation. It specifies digital identities, oversees authentication, and manages access to ensure accountability.
Key IAM Features to Look for
The following are the best features of IAM that ensure businesses have consistent access policies, better accountability, and support for regulatory compliance.
Single Sign-On (SSO): Users only need one sign-on credential to access multiple systems.
Multi-Factor Authentication (MFA): This adds another step of verification using biometrics or a one-time code.
Role-Based Access Control (RBAC): Permissions are given based on specific job roles.
Privileged Access Management (PAM): Protects administrator and super user accounts.
User Lifecycle Management: Automates user addition and removal.
Cloud Integration: Provides secure connectivity across on-premise and SaaS environments.
How to find the right IAM solution for your business
With so many IAM tools available, choosing the right one can be challenging. Follow the following steps to identify an IAM solution that fits your business size, security goals, and compliance needs.
Identify Security and Access Needs
Start by reviewing departments, systems and employee roles from the inside. Understand where sensitive information is stored and who should be allowed to have access.
Small and mid-market companies can aim for simple and easy-to-use solutions, while enterprise companies can focus on scaling and integration with current infrastructure.
Compare Features and Capabilities
Look for IAM tools that offer SSO, MFA, and automated provisioning. Consider how well features integrate with existing applications and cloud platforms.
Important Factors to Consider:
- Compatibility with key cloud providers (e.g., AWS, Azure, Google Cloud)
- Policy management and reporting capabilities
- Support for regulatory compliance (e.g., GDPR, ISO)
- Customised dashboard for users
Stay protected online! Learn how you can protect your online presence with the best VPN solutions.
Gain Full Visibility Into Who Has Access to What
Manage identities, permissions, and compliance effortlessly with IAM – fast deployment, minimal maintenance, maximum protection.

Assess Vendor Reliability and Support
Select providers that provide reliability, regional support, and responsiveness. If local support is offered in India, it can support the implementation process and limit delays.
Evaluate Pricing and Licensing Models
Compare the pricing tiers available in the market, including any hidden costs such as maintenance contracts or additional vendor-provided modules. Some vendors offer pay-as-you-grow options that accommodate a pay-as-you-use system if your organisation scales up.
Test Before Large-Scale Deployment
Conduct an initial pilot deployment with a limited user group so you may monitor ease of access, performance of the system, and reporting.
What really happens inside a Security Operations Center ? The answer might surprise you!
Common Mistakes to Avoid During the IAM Tool Selection Process
Even well-prepared teams can make errors that weaken their IAM implementation. Here are common pitfalls to watch out for before finalising your tool.
- Not researching enough about the selected tool’s availability, reliability, and scalability, and not considering existing systems integration.
- Not researching if an automation opportunity will assist in user provisioning and deprovisioning.
- Overlooking the compliance, certificates, and vouching audit trails.
- Skipping the staff onboarding and awareness training.
- Only considering the costs & outcomes instead of long-term reliability and scalability.
Simplify IAM Integration Across Cloud and On-Prem Systems
Get an IAM solution built for your workflows – flexible, scalable, and backed by 24/7 assistance without extra setup or training costs.

Conclusion
Choosing the best IAM solution requires clarity about business objectives, integration considerations, and future scalability. The right solution can authenticate and deploy policy control and reporting capabilities together in an integrated software suite, all while keeping users and systems secure..
Contact Mitigata today for your free IAM Demo!

