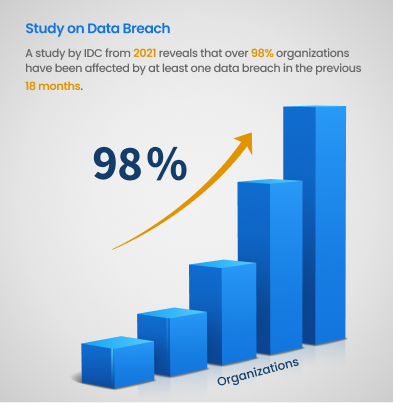
With fast-evolving technology and unending digital transformations, the business landscape is becoming increasingly prone to cyber attacks and other cyber threats. A study by IDC from 2021 reveals that over 98% organizations have been affected by at least one data breach in the previous 18 months.
India itself has witnessed 1787 cyberattacks per week since 2022, surpassing the global average of 983.
Unfortunately, many businesses still consider navigating (and preventing) security breaches to be a Herculean task. On one hand, SaaS business leaders show an increased inclination towards building more digital assets. On the other hand, they feel unable to fund the implementation of best-practice cybersecurity strategies.
This situation creates easy targets for hackers, which naturally results in a fear of financial losses, data losses, and reputational damage. It has resulted in a meteoric rise in the demand for cyber insurance and comprehensive cyber policies.
What if there was a robust solution that combines the best of both worlds?
Imagine a scenario where you automate your cybersecurity measures in real time, and companies that reduce their cyber attack surface benefit from greater access to cyber insurance coverage and, in some cases, lower cyber insurance costs.
Cyber Insurance provides adequate first party coverage in the event of a breach, while security automation proactively shields against potential threats way in advance. In this blog, we aim to highlight how modern businesses can create a foolproof defense system by bringing these two together.
Understanding the Growing Cyber Insurance Market and Its Policies
The idea of cybersecurity insurance policies originated in the late 1990s. With increasing dependence on technology, there was a noticeable surge in persistent threats. Initially, it concentrated around data breaches and computer assaults, but then moved on to ransomware attacks and socially-engineered security breaches.
However, cyber insurance has since evolved to encompass various cybercrimes such as ransomware, cyber extortion, social engineering attacks, loss of intellectual property, system breakdowns, and disruptions to business operations, stemming from cyber incidents.
The Rapid Growth of the Global Cyber Market and Its Impact on Cyber Policies
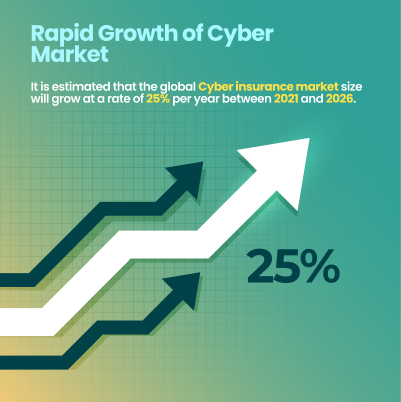
The growing popularity of cyber insurance in the post-pandemic digital world can be easily traced to the unprecedented increase in cybercrimes. In fact, it is estimated that the global cyber insurance market size will grow at a rate of 25% per year between 2021 and 2026.
As cyber threats become more dangerous and unpredictable, the premise of cyber insurance is also evolving fast.
This becomes apparent when you look at how risk assessment for cyber coverage was done in the past compared to now. A traditional cyber insurance policy uses historical data, often unfit and irrelevant, to conduct risk assessments for a business. Insurers would evaluate a company’s exposure to cyber threats based on industry sector, size, and previous claims, among other factors.
While the cyber services and support may identify areas of improvement as part of their forensic analysis, a cyber liability insurance policy will not cover the cost of upgrading, patching, or hardening the security architecture
Finally, many policies secured outside a country may have geographic restrictions, especially for operations based in that region. While once effective, this method used by traditional insurance policies has now become nearly obsolete. Why? Because relying solely on traditional insurance policies just isn’t cutting it anymore. Past data fails to adequately account for the dynamic nature of modern cyber risks and potential vulnerabilities. Be it emerging malware attack strains or advanced hacking techniques on your systems.
The Role of Automation in Enhancing Cyber Insurance Policies and Coverage
This is where security automation can come into the picture. By integrating security automation tools in their offerings, cyber insurance policy providers can gain a deeper understanding of an organization’s security posture and, most importantly, your organization’s propensity to consistent and structured cyber risk assessments and security audits.
This allows the cyber insurance industry to create customized policies that address the specific risks faced by the organization, ensuring maximum cyber insurance coverage while minimizing direct costs. Ultimately, this mutually beneficial relationship between security automation and cyber insurance leads to more effective cyber policies and a secure future for businesses and their customers. It’s a win-win for everyone!
The Synergy of Cyber Insurance and Automated Protection
The convergence between cyber insurance and security automation makes a lot of sense in today’s cyber landscape. With cyber threats becoming more sophisticated, relying solely on traditional security measures just isn’t cutting it anymore.
Security automation with a healthy dollop of artificial intelligence goes one step ahead to offer a proactive defense. Keeping security on autopilot with an AppSec and API security tool can help a software team constantly monitor, detect, and fix security vulnerabilities before they’re exploited.
By pairing such proactive measures with a cyber insurance policy cover, software companies can not only qualify for cybersecurity insurance but also get a clearer picture of their overall cybersecurity readiness.
It’s just like putting on an extra layer of warm clothes to make sure you don’t catch a cold in winter.
The benefits of such a convergence can be analyzed from three aspects:
1. Better Assessment of Cyber Risks in the Cyber Insurance Industry
By automating security, businesses can conduct penetration testing on a far more regular basis. In fact, with an automated web app vulnerability assessment tool, the security posture can be directly integrated into the CI/CD pipelines. This can be done at probably half the costs, since the dependency on external security vendors will reduce dramatically.
Incorporating automated VAPTs into a security framework will allow businesses to provide their cyber insurance partners with up-to-date information on their recurring vulnerabilities. The insurance company, in turn, can use this data directly to tailor the insurance coverage to the specific needs and risk profile of the company.
2. How Automation Transforms Cyber Insurance Premiums
Continuous monitoring not only involves keeping an eye on cyber risks but also shakes up how insurance premiums are calculated.
With real-time data at their fingertips, insurers can ditch the guesswork and offer more dynamic and accurate cyber insurance premiums, based on your organization’s actual cybersecurity practices.
So, if you’ve got robust cybersecurity measures in place, you might snag lower cyber insurance premiums. Fairer prices for you and a safer cyber world for everyone.
For businesses, the integration of automated security into their cyber insurance strategy is highly cost-efficient. Using tools that conduct pentest as a service helps in mitigating the risks before they manifest into actual damage, but also potentially lowers cyber insurance premiums.
Cyber insurance firms can provide better rates to organizations that demonstrate proactive security measures, as it reduces the likelihood of a claim.
3. Integrating Automated Cybersecurity: 3 Key Steps to Mitigate Cyber Threats
Any organization in the digital space can achieve this by:
1. Adopting Automated VAPT and Making Security a Part of Their SDLC
By using automated security tools as part of their SDLC, organizations can effectively reduce their attack surface, improve network control, and make their risk profiles stronger.
This approach of integrating security testing analysis earlier in the software development life cycle is famously known as “shifting left,” a term coined by Larry Smith in 2001. Shifting left helps to:
- Eliminate the need for manual testing and external consultants.
- Significantly reduce costs associated with manual security testing as they require a lot of man power in the form of pen testers.
- Scale security efforts effectively to ensure continuous protection against emerging threats.
2. Crafting Data Sharing Protocols for Effective Cyber Assessment
After adopting security automation, any business should examine procedures for strategically disclosing vulnerability information for insurance evaluation. Businesses should safeguard sensitive data, such as customer information for a financial institution, while disclosing vulnerability information for insurance evaluation. Read on to find out about this in more detail.
Insurers can aid from this integration by:
3. Collaborative Analysis: Developing Comprehensive Plans to Tackle Attacks
Working together, cybersecurity professionals and insurance analysts can use the findings from penetration tests to develop a comprehensive solution to risk management.
Using detailed insights from pen tests, insurers can create more customized insurance products and packages, based on industry or organization size.
Challenges in Integrating Cybersecurity Insurance and Automated Security
Security automation offers numerous advantages, including faster incident response times, improved threat detection, and reduced manual workloads. However, it also comes with its unique set of challenges, one of which is data privacy.
A critical aspect of integrating security automation is crafting effective data sharing protocols. organizations must strike a delicate balance between providing insurance providers with the information they need to assess risk and protecting sensitive data, such as customer information. Organizations face a complex task, as they must consider a variety of factors, including the type of data they share, the purpose of the sharing, and the potential risks and benefits involved.
If an organization shares too much data, it could increase the risk of a data breach or other security incident. Conversely, if an organization shares too little data, it could prevent insurers from accurately assessing risk, potentially resulting in even a denial of coverage.
To address this challenge, organizations should develop a comprehensive data-sharing policy that outlines the types of data they can share, the purpose of the sharing, and the security measures they will implement to protect the data. The policy should also include a process for reviewing and updating the data sharing agreement on a regular basis.
By following these best practices, organizations can mitigate the risks associated with data sharing and ensure that they are able to take full advantage of the benefits of security automation.
Conclusion
Integrating security automation into cyber insurance is changing how businesses operate today. By incorporating automated VAPT tools into the SDLC and taking a proactive cybersecurity stance, organizations are able to drastically cut down their attack surface, enhance network control, and fortify their risk profiles. In addition to strengthening their overall cybersecurity posture, this partnership compliments other benefits as well. These include lower cyber insurance rates, availability of real-time data availability for trustworthy risk assessments, and the ability to tailor insurance policies as per specific needs.
However, this proactive approach brings its own challenges, especially regarding data privacy. Organizations must delicately balance safeguarding sensitive data with providing insurers the requisite information for a comprehensive risk analysis. The implementation of efficient data-sharing mechanisms is essential to fully capitalize on the potential benefits. As the cyber threat landscape evolves, the combination of security automation and cyber insurance is crucial for safeguarding assets and staying competitive.
This can lead to more favorable insurance terms. Insurers can improve their products and support by analyzing risks collaboratively with clients. As the cyber threat landscape evolves, the combination of security automation and cyber insurance is crucial for safeguarding assets and staying competitive.




