“Data is a precious thing and will last longer than the systems themselves.” — Tim Berners-Lee Imagine waking up to find that your company’s data has been compromised. Customer information is exposed, and your operations come to a standstill. This nightmare scenario is becoming increasingly common in our hyper-connected world. To safeguard against such threats, integrating cyber insurance with Data Loss Prevention (DLP) tools is essential. This comprehensive guide delves into the depths of how this integration can bolster your cybersecurity strategy.
The Rising Tide of Cyber Threats
Cyber threats are more than just headlines—they are real dangers that have profound impacts on businesses worldwide. Here’s an in-depth look at the various types of cyber threats and their growing prevalence:
Ransomware Attacks
Ransomware attacks have surged in recent years, becoming one of the most lucrative and disruptive forms of cybercrime. In a ransomware attack, cybercriminals infiltrate a network, encrypt valuable data, and demand a ransom for its release. The sophistication of these attacks has increased, with hackers employing advanced encryption methods and even customer service tactics to negotiate ransoms.

Data Breaches
Data breaches involve unauthorized access to confidential information, such as customer data, intellectual property, or financial records. These breaches can result from various sources, including external hackers, insider threats, or inadequate security measures.
Statistics:
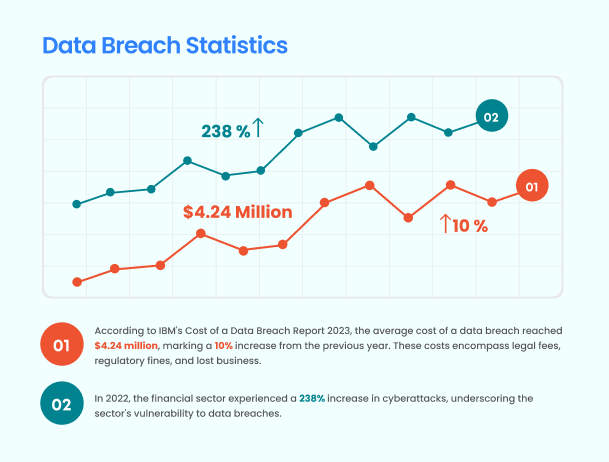
- According to IBM‘s Cost of a Data Breach Report 2023, the average cost of a data breach reached $4.24 million, marking a 10% increase from the previous year. These costs encompass legal fees, regulatory fines, and lost business.
- In 2022, the financial sector experienced a 238% increase in cyberattacks, underscoring the sector’s vulnerability to data breaches (ncbi).
Phishing Scams
Phishing scams trick individuals into providing sensitive information by posing as legitimate entities. These scams are often executed through deceptive emails, messages, or websites.

Survey Findings: Verizon’s 2023 Data Breach Investigations Report found that 36% of all data breaches involved phishing attacks. These attacks exploit human error, making them particularly challenging to prevent through technology alone.
Understanding Cyber Insurance
Cyber insurance is a crucial component of a modern cybersecurity strategy. It provides financial protection and support in the aftermath of a cyber incident, helping businesses recover more quickly and efficiently.
What is Cyber Insurance?
Cyber insurance is a specialized insurance product designed to protect businesses from the financial fallout of cyber incidents. Unlike traditional insurance, which covers physical assets, cyber insurance covers digital assets and the costs associated with cyberattacks.
Key Benefits of Cyber Insurance
1. Financial Protection:
- Coverage for Various Costs: Cyber insurance policies typically cover a wide range of expenses, including forensic investigations to determine the cause and extent of a breach, legal fees for defending against lawsuits, and customer notification costs.
- Business Interruption: Policies often include coverage for business interruption losses, helping companies recover lost income during downtime caused by a cyber incident.
2. Legal Support:
- Regulatory Compliance: Cyber insurance can provide access to legal experts who specialize in data protection regulations, such as GDPR, CCPA, and HIPAA. These experts can guide businesses through the complex regulatory landscape.
- Defense Against Lawsuits: In the event of a data breach, companies may face lawsuits from affected customers or regulatory bodies. Cyber insurance can cover the costs of defending against these lawsuits and any settlements or fines that may result.
3. Crisis Management:
- Public Relations Support: Cyber insurance policies often include access to public relations firms that specialize in managing the fallout from cyber incidents. These firms can help companies communicate effectively with stakeholders, including customers, employees, and the media.
- Reputation Management: Maintaining a positive reputation is crucial for businesses, especially after a cyber incident. Cyber insurance can provide resources to help companies manage their reputations and rebuild trust with their customers.
Types of Cyber Insurance Coverage
Cyber insurance policies can vary widely, but they generally fall into two main categories:
1. First-Party Coverage:
- Direct Losses: Covers direct losses incurred by the policyholder, such as data recovery costs, business interruption losses, and extortion payments.
- Incident Response: Provides coverage for costs associated with responding to a cyber incident, including forensic investigations and crisis management services.
2. Third-Party Coverage:
- Liability: Covers legal liabilities arising from a data breach, including lawsuits from affected customers, regulatory fines, and settlements.
- Regulatory Penalties: Provides coverage for fines and penalties imposed by regulatory bodies for non-compliance with data protection regulations.
Data Loss Prevention (DLP) Tools
DLP tools are essential for protecting sensitive data from unauthorized access, use, or disclosure. These tools play a critical role in preventing data breaches and ensuring compliance with data protection regulations.
What are DLP Tools?
DLP tools are software solutions designed to monitor and control data flow within an organization. They help identify and protect sensitive data by enforcing security policies and preventing unauthorized data transfers.
Key Features of DLP Tools
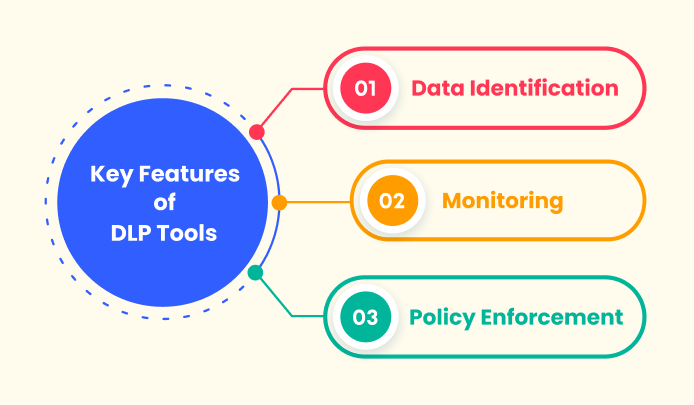
1. Data Identification:
- Classification: DLP tools classify and label sensitive data based on predefined policies, such as personally identifiable information (PII), payment card information (PCI), and intellectual property (IP).
- Discovery: DLP tools can scan and discover sensitive data across various data repositories, including databases, file servers, and cloud storage.
2. Monitoring:
- Data in Motion: Continuous monitoring of data in motion (network traffic) helps detect and prevent unauthorized data transfers. This includes monitoring email communications, web traffic, and file transfers.
- Data at Rest: DLP tools monitor data at rest (stored data) to ensure that sensitive information is adequately protected. This includes monitoring databases, file systems, and cloud storage for unauthorized access.
- Data in Use: Monitoring data in use (endpoint activities) helps detect and prevent unauthorized access to sensitive information on user devices. This includes monitoring clipboard activities, printing, and file downloads.
3. Policy Enforcement:
- Blocking and Alerting: DLP tools enforce security policies by blocking unauthorized data transfers and alerting administrators to suspicious activities. This helps prevent data breaches and ensures that only authorized personnel can access and share sensitive information.
- Granular Controls: DLP tools provide granular controls to enforce specific security policies based on user roles, data types, and contexts. This allows organizations to tailor their data protection measures to their unique needs.
Real-Life Example:
For instance, if a financial services firm implemented DLP tools to safeguard customer information. The system detected and blocked an attempted data exfiltration by a malicious insider, preventing a potential breach that could have cost the company millions in fines and lost customer trust. This proactive measure not only protected the firm’s reputation but also saved it from significant financial losses.
Integrating Cyber Insurance with DLP Tools
Combining cyber insurance with DLP tools creates a comprehensive cybersecurity strategy that addresses both prevention and remediation. This integration helps businesses protect sensitive data and ensures they have the financial and legal support needed to recover from cyber incidents.
Step-by-Step Integration
1. Risk Assessment:
- Identify Critical Assets: Conduct a thorough risk assessment to identify critical assets and potential vulnerabilities. This involves evaluating current security measures, identifying gaps, and prioritizing areas that need improvement.
- Threat Analysis: Assess the types of cyber threats that pose the greatest risk to your organization. This includes evaluating the likelihood and potential impact of various threats, such as ransomware, data breaches, and phishing attacks.
2. Policy Development:
- Develop Data Protection Policies: Develop and implement data protection policies that align with regulatory requirements and industry best practices. These policies should outline the types of data to be protected, how they will be monitored, and the procedures for responding to incidents.
- Regular Reviews: Regularly review and update data protection policies to ensure they remain effective and aligned with evolving threats and regulatory changes.
3. DLP Implementation:
- Deploy DLP Tools: Deploy DLP tools to monitor and protect sensitive data across the organization. This includes configuring the tools to detect and prevent unauthorized data transfers, as well as setting up alerts for suspicious activity.
- Integration with Existing Systems: Ensure that DLP tools are integrated with existing security systems, such as firewalls, intrusion detection systems, and endpoint protection solutions.
4. Cyber Insurance Procurement:
- Obtain Tailored Coverage: Obtain a cyber insurance policy tailored to the specific risks identified in the risk assessment. Work with an insurance provider to customize coverage that addresses the unique needs of your business.
- Regular Policy Reviews: Regularly review and update your cyber insurance policy to ensure it continues to provide adequate coverage as your business evolves and new threats emerge.
5. Incident Response Planning:
- Develop an Incident Response Plan: Develop and regularly update an incident response plan that integrates the capabilities of DLP tools and the coverage provided by cyber insurance. This plan should outline the steps to take in the event of a breach, including how to contain the incident, notify affected parties, and recover from the attack.
- Simulation Exercises: Conduct regular simulation exercises to test the effectiveness of the incident response plan and ensure that all employees are familiar with their roles and responsibilities during a cyber incident.
6. Training and Awareness:
- Employee Training: Conduct regular training sessions for employees to raise awareness about data protection and cyber insurance policies. Employees should understand the importance of safeguarding sensitive information and know how to recognize and respond to potential threats.
- Continuous Education: Implement ongoing education programs to keep employees informed about the latest cybersecurity threats and best practices. This helps create a culture of security within the organization.
Real-Life Example : Integration in Action
For instance, a mid-sized e-commerce company faced increasing cyber threats as it grew. To protect its customer data and business operations, the company integrated DLP tools with a comprehensive cyber insurance policy. When a phishing attack targeted several employees, the DLP system detected the suspicious activity and prevented the exfiltration of sensitive data. At the same time, the company’s cyber insurance policy covered the costs of the forensic investigation and legal fees, thereby allowing the business to quickly recover and maintain customer trust.
Benefits of Integration
1. Enhanced Security:
- Proactive Protection: DLP tools provide real-time protection against data breaches by continuously monitoring and controlling data flow within the organization. This proactive approach helps prevent incidents before they occur.
- Comprehensive Coverage: Cyber insurance offers financial and legal support in case of breaches, ensuring that businesses have the resources needed to recover from cyber incidents.
2. Regulatory Compliance:
- Data Protection Regulations: Both DLP tools and cyber insurance help organizations comply with data protection regulations such as GDPR, CCPA, and HIPAA. By implementing these solutions, businesses can demonstrate their commitment to data security and regulatory compliance.
- Audit and Reporting: DLP tools provide detailed audit trails and reporting capabilities, helping organizations maintain compliance with regulatory requirements and respond to audits more efficiently.
3. Cost Efficiency:
- Reduced Risk of Breaches: By preventing data breaches, DLP tools reduce the likelihood of insurance claims, potentially lowering insurance premiums. This cost-saving benefit can be significant over time.
- Financial Support: The financial support provided by cyber insurance can offset the costs of a breach, reducing the overall financial impact on the business. This includes covering expenses related to legal fees, customer notifications, and business interruption losses.
4. Business Continuity:
- Minimal Disruption: A comprehensive approach ensures minimal disruption to business operations during and after a cyber incident. With both prevention and remediation measures in place, businesses can quickly recover from attacks and continue serving their customers without significant downtime.
- Customer Trust: Maintaining customer trust is crucial for business success. By demonstrating a strong commitment to data protection and having a robust incident response plan in place, businesses can reassure customers that their data is safe.
Challenges and Solutions

Challenge 1: Integration Complexity
Integrating DLP tools and cyber insurance can be complex, especially for businesses with limited cybersecurity expertise.
Solution: Partner with experienced cybersecurity firms like Mitigata and SECUREU to streamline the integration process. These firms offer expertise in deploying DLP solutions and navigating the complexities of cyber insurance. They can provide customized recommendations and support to ensure a seamless integration.
Challenge 2: Continuous Monitoring and Updates
Cyber threats are constantly evolving, requiring continuous monitoring and updates to security measures.
Solution: Regularly update DLP policies and conduct periodic reviews of cyber insurance coverage to ensure alignment with evolving threats and regulatory changes. Stay informed about the latest cybersecurity trends and best practices, and adjust your strategies accordingly.
Challenge 3: Employee Awareness
Employees play a critical role in data protection, but they may not always be aware of best practices or the importance of cybersecurity.
Solution: Implement ongoing training programs and simulations to reinforce the importance of data protection and the role of cyber insurance. Use real-life scenarios and hands-on exercises to help employees understand how to identify and respond to potential threats.
Conclusion:

Integrating cyber insurance with Data Loss Prevention tools is a comprehensive approach to modern cybersecurity challenges. By doing so, businesses combine proactive data protection measures with the financial and legal support of cyber insurance. As a result, they can significantly enhance their resilience against cyber threats.
we are leader in providing cyber insurance for businesses, offers expert guidance and comprehensive coverage to protect businesses from the financial impacts of cyber incidents. In collaboration with Secure U, which specializes in data loss prevention, we also offers a holistic approach to safeguarding valuable data and ensuring business continuity.




