“Amid the chaos, there is also opportunity.” – Sun Tzu. The shift from traditional office work to remote work—initially driven by the coronavirus (COVID-19) pandemic—has now become a permanent change in how businesses function. This switch, although enabling a wide spread of advantages (e.g., enhanced adaptability and job satisfaction), has also created a new type of challenges, especially in the branch of computer security. As remote work is getting integrated into the everyday life of modern business, security is unavoidable.
The Remote Work Revolution
A Paradigm Shift
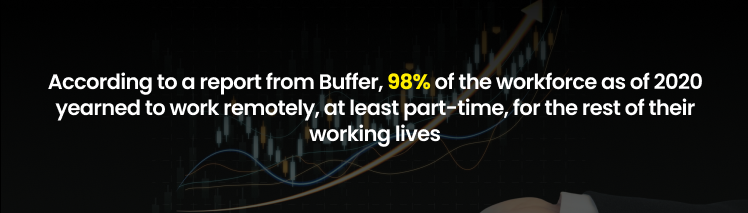
However, remote work is not a novel idea; rather, it burgeoned during the COVID-19 crisis. Adaptional changes were driven globally by a need to sustain business models, leading to an unprecedented amount of dependence on digital technologies. According to a report from Buffer, 98% of the workforce as of 2020 yearned to work remotely, at least part-time, for the rest of their working lives. Evolution has been aided by technological advancement, global connectivity, and a personal need for better work-life balance.
Benefits of Remote Work
Remote work offers numerous benefits:
- Flexibility: Laborers can now work from wherever they are, and so the work-life balance will be much better.
- Increased Productivity: Many employees report higher productivity levels when working remotely.
- Cost Savings: Employers and employees can also reduce commuting, office, and utility costs.
- Talent Pool Expansion: Companies can hire talent from anywhere in the world, not limited by geographical constraints.
Undoubtedly, with those advantages come significant cybersecurity problems that must be addressed.
Remote Work: A Cybersecurity Challenge
The Changing Cybersecurity Landscape
The increase in the attack surface due to the transition to telework has broadened cyber attackers’ scope. Cyber attackers have used this shift to target vulnerabilities in remote work infrastructures.
Device and Network Diversity
In a traditional office telecommuting situation, the employer is responsible for managing and securing the network and devices used by its employees. The remote work environment enhances employees’ risk of cyber attacks due to the vast number of devices and networks that they use. For example, an office worker connected to a coffee shop would likely connect to an insecure public Wi-Fi network, which exposes the user to a cyberattack.
Home Networks
Home networks, in general, lack the strong security paradigms of enterprise networks. Cybercriminals often exploit weak passwords, outdated firmware, and unattended vulnerabilities in home gateways and Internet of Things (IoT) devices. According to McAfee, in this study, 28% of US respondents admitted to default passwords on personal home routers, which cybercriminals can exploit “routinely.
Increased Phishing Attacks
Phishing attacks have become more sophisticated and targeted. Remote workers, who are dependent on email communication, are ideal candidates. Cybercriminals produce convincing content that replicates messages from actual organizations (e.g., human resources office or information technology help desk) to obtain credentials or deliver malware.
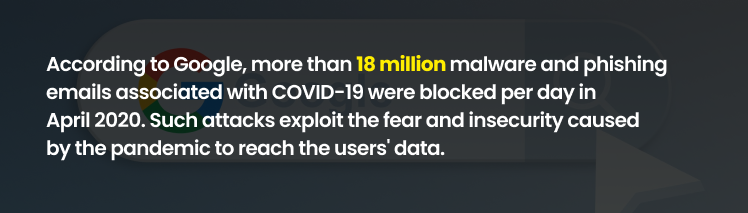
According to Google, more than 18 million malware and phishing emails associated with COVID-19 were blocked per day in April 2020. Such attacks exploit the fear and insecurity caused by the pandemic to reach the users’ data.
Ransomware Attacks
Ransomware attacks have increased exponentially in tandem with the rise of remonetization. Cybercriminals exploit vulnerabilities in remote work setups and carry out ransomware attacks, which hold critical data hostage and demand ransom money to release it. A notable incident involved the attack on the University of California, San Francisco (UCSF) in June 2020, where the institution paid a ransom of $1.14 million to regain access to its data.

Insider Threats
Remote work can also lead to an insider threat vulnerability. Employees who work from home could accidentally or deliberately lose data. Ponemon research found that insider threats increased by 47% from 2018 to 2020, costing businesses $11.45M per year.

VPN Vulnerabilities
Several remote workers utilize Virtual Private Networks (VPNs) to access company networks. However, VPNs can have vulnerabilities that cybercriminals can exploit. In 2019, a severe vulnerability in Pulse Secure VPN, which large organizations widely used, could be exploited by an attacker who could bypass access control to access corporate networks.
Mitigating Cybersecurity Risks in Remote Work
Organizations and remote workers must collaborate and address these issues to safeguard remote work environments. Here’s how:
Education and Training
Organizations should provide cybersecurity training and awareness programs for employees. Workers should be able to recognize phishing attacks and be familiar with best practices for secure remote work. As per Proofpoint’s 2020 State of the Phish report, 88% of organizations experienced phishing attacks, which warrants ongoing training.

Multi-Factor Authentication (MFA)
MFA implements an additional layer of security that demands at least two distinct verification factors to block unauthorized access. A study conducted by Microsoft reported that MFA can intercept more than 99.9% of account compromise attacks.
Endpoint Security
Endpoint security protects devices from malware and data exfiltration. Software should be regularly updated and patched to fix vulnerabilities. With the increasing sophistication of endpoint attacks, Symantec’s Internet Security Threat Report states that endpoint security is of paramount consideration.
Secure VPNs
Verify that the VPNs’ security is sound and current, and restrict access to only trusted personnel. Do not use free public VPNs because they are not safe. The Cybersecurity and Infrastructure Security Agency (CISA) advises using VPNs with strong encryption to protect data.
Data Encryption
Encrypt sensitive data to protect it from interception. Data privacy is also essential to secure cloud storage and sharing software. According to Thales’ report, 50% of businesses globally have suffered data breaches, which raises the importance of data encryption.

Regular Audits and Monitoring
Continuously monitor networks and devices for suspicious activities. Conduct regular security audits to identify and rectify vulnerabilities. Verizon Data Breach Investigations Report 2020 showed that 86% of incidents were financially motivated, and as such, an anticipatory mechanism against monitoring emerged.
Policy Development
Establish clear and comprehensive remote work security policies. Describe a set of considerations for secure telecommuting, password, and data security. Therefore, the National Institute of Standards and Technology (NIST) offers guidelines for establishing effective security policies.
Collaboration Tools
Create secure and collaborative communication devices and services that allow safe communication and exchange of information between dispersed groups. According to a TechRepublic survey, 91% of organizations use at least two collaborative tools, and the security of that collaboration is paramount.
Access Control
Control data and system access under the principle of minimal privilege. Grant access only to the data needed by employees to perform their work. According to Gartner, 70% of organizations use privileged access management tools, implicitly confirming the importance of access control.
Cyber Insurance
Invest in cyber insurance to cover potential financial damages resulting from cyber incidents. According to Allianz Risk Barometer 2020, cyber incidents represent the most critical business risk in the world, and thus, they should be addressed, especially in the context of cyber insurance.
Quick Read: Ensuring Cyber Security: Insurance for Remote Employees.
Cybersecurity Best Practices for Remote Workers
Working from home offers flexibility and convenience, but it also comes with unique security challenges. Implement these basic cybersecurity recommendations for secure work from home: vampires and others).
1. Secure Your Home Network
1.1. Change Default Credentials
Change your home router’s default admin username and password to stop someone from hacking into the device.
1.2. Use Strong Encryption
Turn on Wi-Fi WPA3 protection to achieve suitable protection.
1.3. Set a Strong Password
Create a complex, unique password for your Wi-Fi network.
1.4. Update Firmware
Regularly update your router’s firmware to patch security vulnerabilities.
2. Employ Strong Authentication
2.1. Multi-Factor Authentication (MFA)
For further protection, whenever it is feasible to implement MFA as a security measure, please do so (and add a security measure on that single layer).
2.2. Use Strong Passwords
Come up with your own complicated passwords for your accounts, and definitely use a trusted password keeper (i.e., a password manager).
3. Secure Your Devices
3.1. Antivirus and Antimalware
Install a trusted antivirus and antimalware program to protect against malware on devices.
3.2. Keep Software Updated
Periodically scan and update your operating system and software to patch security holes.
3.3. Firewall
Activate your device’s built-in firewall to block unauthorized access.
4. Be Cautious with Emails
4.1. Beware of Phishing
Be skeptical of email links and attachments. Verify the sender’s authenticity before clicking.
4.2. Check Email Headers
Verifies that the sender of an email is authentic to that domain and not a spoofed address.
4.3. Report Suspicious Emails
If you receive a phishing email, report it to your IT department.
5. Use Secure Connection Methods
5.1. VPN
Use a VPN to encrypt the internet connection and to secure info while data is transmitted.
5.2. Secure Wi-Fi
Avoid using public Wi-Fi networks. Use a VPN if necessary for a secure connection.
6. Protect Physical Security
6.1. Lock Devices
If idle, please lock up your computer(s) or other device(s).
6.2. Secure Paper Documents
Store sensitive documents in a locked drawer or safe.
7. Educate Yourself
7.1. Training
Stay informed about the latest cybersecurity threats and solutions. Consider taking cybersecurity training courses.
7.2. Security Policies
Adhere to your organization’s remote work security policies.
8. Secure Video Conferencing
8.1. Use Passwords
Password-protect video conferencing meetings to prevent unauthorized access
8.2. Control Access
Restrict host site screen-sharing users and use waiting rooms for attendees.
9. Backup Data
9.1. Regular Backups
Establish periodic cyclic data backups to an external storage device or a cloud storage service.
9.2. Ransomware Protection
Protect against ransomware by having secure backups in place.
10. Physical Privacy
10.1. Avoid Shoulder Surfing
Ensure your screen is not visible to unauthorized individuals.
10.2. Lock Office Door
Perform in a room with a lockable door to prevent intrusion.
11. Remote IT Support
11.1. Contact IT Support
If any security problems are identified, please notify your organization’s IT department. Adhering to these practices allows one to sustain a safe working environment from afar and safeguard confidential information and data. Vigilance and an active approach are essential in the ever-evolving world of cyberspace security.
The Role of Cyber Insurance in Remote Work
Understanding Cyber Insurance
Cyber insurance reimburses financial risk for internet attacks. Policies typically cover costs related to data breaches, ransomware attacks, business interruption, and legal expenses. According to Allianz’s Risk Barometer 2020, cyber incidents are the top business risk globally, making cyber insurance an essential component of a comprehensive cybersecurity strategy.
Benefits of Cyber Insurance
1. Financial Protection
Cyber insurance may cover incidental costs associated with a cyber incident, such as forensic investigations, legal costs, and notification costs. This financial backstop can be of great significance to a small—or medium-sized enterprise (SME) that is hit hard by a shocking cyber attack and cannot bounce back from it.
2. Risk Management Support
Support: Most cyber insurers started providing risk management services to protect organizations against cyberattacks. These services may consist of security testing, personnel training, and incident response planning.
3. Compliance and Regulatory Support
Cyber insurance could allow organizations to satisfy data protection regulation requirements (e.g., GDPR and HIPAA). Policies may include sanctions and penalties for non-compliant behavior and support in managing compliance.
Choosing the Right Cyber Insurance Policy
To select a cyber insurance product, the following should be considered:
Coverage Limits
The policy adequately covers potential liabilities, including an analysis of the cost of data breaches, business disruption, and litigation.
Policy Exclusions
Understand the exclusions and limitations of the policy. There may also be policies that do not extend to certain types of events, e.g., insider attacks or residual weaknesses.
Incident Response Services
Identify policies that contain incident response services, such as providing access to cybersecurity professionals and legal counsel. These services are highly valuable in the aftermath of a cyber incident.
Reputation of the Insurer
Choose an insurer with a strong reputation and experience in providing cyber insurance. Check trusted reviewers’ feedback and market rankings to see if the insurer holds up to the claims made about it.
Building a Cyber-Resilient Remote Work Culture
Fostering a Security-First Mindset
In the cyber-resilient, remote work society, all members must adopt a security-first perspective to adopt a security-by-design paradigm. This includes recurrent training and education sessions to effectively inform the employees of the importance of cybersecurity and their engagement in maintaining it. According to a report from CybSafe, 90% of successful cyberattacks are due to human error, which reveals the empirical necessity for continuing training.
Encouraging Collaboration Between IT and Employees
Security groups should collaborate with employees to mitigate their security risks and provide support. Advice on how to securely set up home networks, how to work securely using collaborative tools, and how to recognize phishing attacks should be among the topics discussed.
A Cisco study determined that organizations with robust collaboration between IT and end users had almost 20% fewer cybersecurity incidents.
Recognizing and Rewarding Secure Behavior
Identifying and incentivizing personnel who adhere to security best practices can foster a cybersecurity culture. This may be achieved by means of incentives, such as bonuses or praise, for staff members who exhibit a commitment to securing the integrity of the security system.
Implementing a Feedback Loop
By creating a feedback loop whereby employees can flag security blemishes and indicate their enhancements, organizations can be equipped to keep pace with new threats. This requires making a channel available for employees to contact the IT department and for their concerns to be acknowledged.
Case Studies of Cybersecurity Breaches in Remote Work



Conclusion: Trust Mitigata for Your Cyber Insurance Needs

Remote work is here to stay, and its relationship with cybersecurity is top of every organization’s mind. As remote work environments evolve, so must the strategies and tools to protect sensitive data and systems.
A proactive approach to cybersecurity that involves training, policy development, and robust security measures can help organizations navigate the remote work landscape securely and confidently.
Cybersecurity is no longer confined to the office; it’s now a vital aspect of every employee’s work environment, wherever that may be.
Mitigata offers comprehensive cyber insurance solutions designed to protect businesses from financial and operational impacts of cyber incidents.
Using Mitigata, you can work confidently through the challenges of telework, supported by best-in-class industry experience and expertise.
Safeguard your business, ensure your future, and entrust Mitigata as your cybersecurity partner.


