SOC compliance may not sound thrilling, but for any organisation that handles sensitive customer data, it’s absolutely essential.
Think of it as a digital trust badge, one that proves your internal systems and controls are built to protect customer information.
As cyber threats grow more sophisticated, regulatory expectations rise, and client demands evolve, SOC compliance has become more than just a checkbox. It’s a competitive advantage.
In this blog, we’ll break down what SOC compliance is, the different types, why it matters, and what’s at stake if you ignore it. If you’re looking to safeguard your business and build trust with stakeholders, read on.
Reasons Why 800+ Companies Prefer Mitigata for SOC Monitoring
As the sole full-stack cyber resilience firm in India, Mitigata merges 24/7 SOC oversight, swift incident reaction, and smart threat identification to ensure your business’s security. Relied upon by over 800 organisations in various sectors, our AI-based solutions provide ongoing protection against changing cyber threats.
What sets us apart:
24/7 Protection: Our team of certified cybersecurity experts continuously oversees your environment day and night.
Enhanced Threat Detection: Leveraging AI and GenAI-powered analytics, we identify suspicious activity, link threat information, and halt attacks before they escalate.
Integrated Security Framework: Our system consolidates logs from various sources (such as firewalls, servers, and endpoints), simplifying the analysis and correlation of potential threat data.
Tailored Security Approach: By utilising SOAR (Security Orchestration, Automation, and Response) and built-in case management.
Cost-Effective Security: Organisations can save up to 50% compared to establishing an internal SOC while benefiting from high-quality tools and continuous professional supervision.
Rapid Incident Response: Utilising AI and machine learning, our technology reduces detection and response times by as much as 90%, enabling the immediate neutralisation of threats.
Your Full Cyber Defence Starting at Just ₹2,00,000/Month

What is SOC Compliance?
SOC stands for System and Organisation Controls. These are auditing frameworks developed by the American Institute of Certified Public Accountants (AICPA) to ensure that a company manages data securely, particularly when working with service providers.
Essentially, SOC compliance involves undergoing audits to validate how well your organisation protects customer data and maintains effective internal controls.
Unlike one-size-fits-all frameworks, SOC compliance includes reports tailored to different audiences and goals. Each one evaluates a unique aspect of your organisation’s risk posture and control environment.
Want to find the right security tool for real-time threat detection? Read our blog on choosing the best SOC monitoring solution for your organisation.
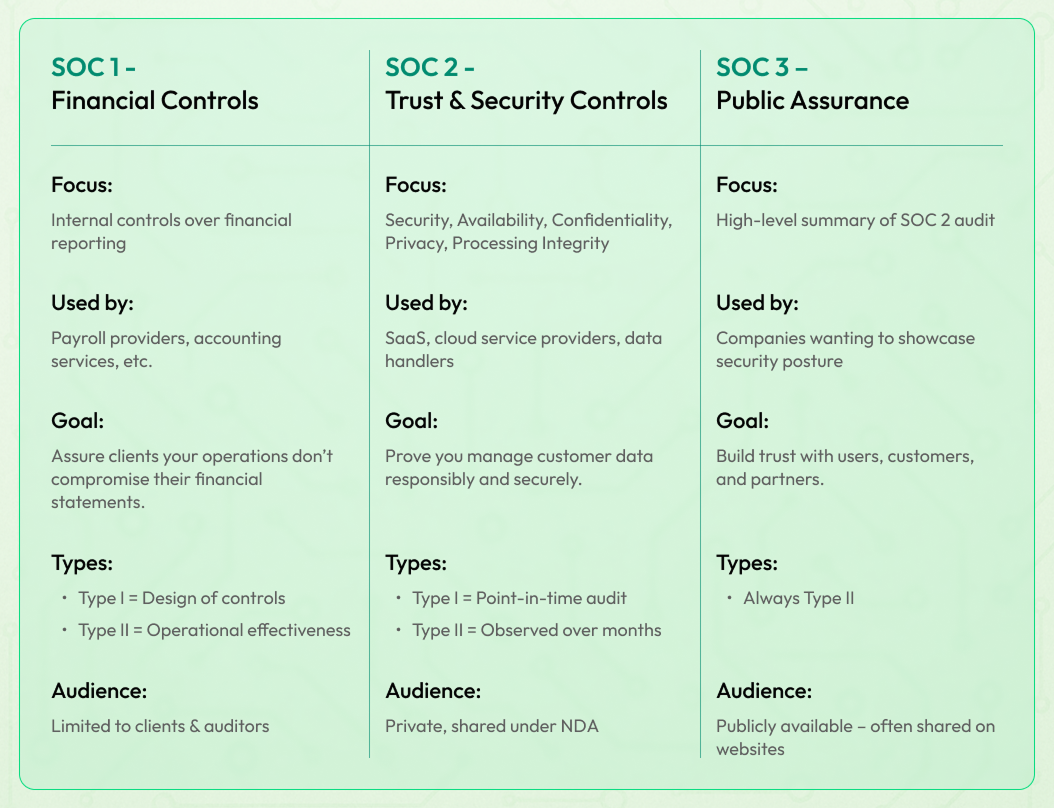
Types of SOC Reports
There are three main types of SOC reports:
SOC 1 is focused on financial reporting. If your services affect your clients’ financial statements, like payroll or transaction processing, this is the one you need. It demonstrates that your financial data controls are sound.
SOC 2 evaluates how a service provider handles data security based on the five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. It’s the most popular framework for SaaS providers, data centres, and cloud-based companies.
SOC 3 is essentially a public-facing version of SOC 2. It provides the same assurances, but in a simplified format that companies can share on their websites or in marketing materials.
Each of these reports comes in two flavours:
Type I evaluates the design of controls at a specific point in time.
Type II assesses how those controls operate over a defined period (typically 6–12 months).
Why SOC Compliance Matters
SOC compliance is not just about ticking boxes. It directly impacts your business credibility, sales pipeline, and resilience. Without it, you risk losing out on large enterprise deals, damaging customer trust, and even facing legal consequences.
Failure to implement and prove proper controls can result in:
Loss of potential partnerships and clients
Regulatory fines in highly regulated industries
Data breaches and associated recovery costs
Long-term reputational damage
Looking to sharpen your security operations? Discover the top SOC monitoring tools tailored for your business in our latest blog.
In contrast, being SOC compliant means you:
Establish trust with current and prospective customers
Strengthen internal controls and security posture
Accelerate deal closures and onboarding processes
Minimise risk exposure through structured audits
SOC That Doesn’t Miss a Breach

SOC 2: The Gold Standard for Tech Companies
Among all types, SOC 2 is the benchmark for most modern technology companies. It focuses heavily on system-level controls that directly impact how customer data is processed and protected.
This is especially important for cloud providers, SaaS companies, and managed service providers.
Whether you’re dealing with user logins, customer databases, or email communications, SOC 2 ensures your systems meet the highest standards for data security and operational reliability.
Many businesses won’t even consider a vendor without a SOC 2 Type II report.
The Road to SOC Compliance
Achieving SOC compliance isn’t an overnight process, but it’s well within reach if you follow a clear path. Here’s how organisations typically approach it:
Gap Assessment: Identify where your current controls fall short of SOC requirements.
Remediation: Implement or enhance processes and documentation.
Monitoring: Ensure controls are consistently followed and maintained.
Audit: An independent auditor validates your controls over time.
SOC vs. Other Frameworks
While frameworks like ISO 27001 are widely recognised, SOC compliance, especially SOC 2, is favoured in the United States and increasingly requested globally.
ISO certifications focus on management systems, whereas SOC focuses on operational effectiveness.
In some cases, companies may pursue both for broader appeal and coverage.
Your Security. Our Priority. Every Second

Conclusion:
In a digital-first world, data protection is no longer optional, and neither is SOC compliance. It isn’t just about avoiding fines or checking a compliance box.
It’s about demonstrating to your customers that their data is safe with you.
Organisations that treat SOC as a strategic asset will gain a competitive edge, reduce risk, and foster deeper trust with clients and partners.
Those that don’t may find themselves sidelined by compliance-savvy competitors.
Want to align your cybersecurity and compliance strategy? Mitigata is here to help you secure your systems while staying ahead of regulatory expectations.
Contact Mitigata now to get a Free Demo and start your SOC journey today.

