VAPT Explained: Meaning, Tools & Report for Your Business [UPDATED]
Q3 2024 saw a 124% rise in vulnerability-based attacks compared to Q3 2023. But that’s not it! In Q2 2024, cyberattacks increased by 30% compared to the same period last year, with organizations experiencing an average of 1,636 attacks per week.
Such statistics not only alarm us about cyberattacks but also underscore the growing need for cybersecurity.
VAPT (Vulnerability Assessment and Penetration Testing) is a cybersecurity process that proactively identifies and addresses security weaknesses in systems and applications by identifying vulnerabilities and testing their exploitability.
This guide will break down the meaning, types, and methodologies of VAPT and provide a list of the Top VAPT Tools for 2025, making it easier for you to safeguard your business.
Did you Quantify your cyber risk today?
Affordable VAPT Solutions Starting at ₹52,000/per Application*
Mitigata combines automated assessments with manual penetration testing for deeper, proven security.

What is VAPT?
VAPT stands for Vulnerability Assessment and Penetration Testing, a dual process used to identify and mitigate security flaws within an organization’s infrastructure. It includes two key components: Vulnerability Assessment and Penetration Testing.
- A vulnerability assessment identifies potential vulnerabilities that could be exploited by cybercriminals, typically through automated scans.
- Penetration Testing (Pentest) simulates real-world attacks to find exploitable vulnerabilities and assesses their potential impact on the organization.
Together, these processes form a VAPT Audit that produces a VAPT Report, offering an in-depth overview of an organization’s security weaknesses.
What is the typical cost of cyber insurance for startups?
What are the Types of VAPT?
There are 6 Significant Types of VAPT focus on different parts of an organisation’s security landscape:
Network VAPT:
Assess network infrastructure for vulnerabilities.
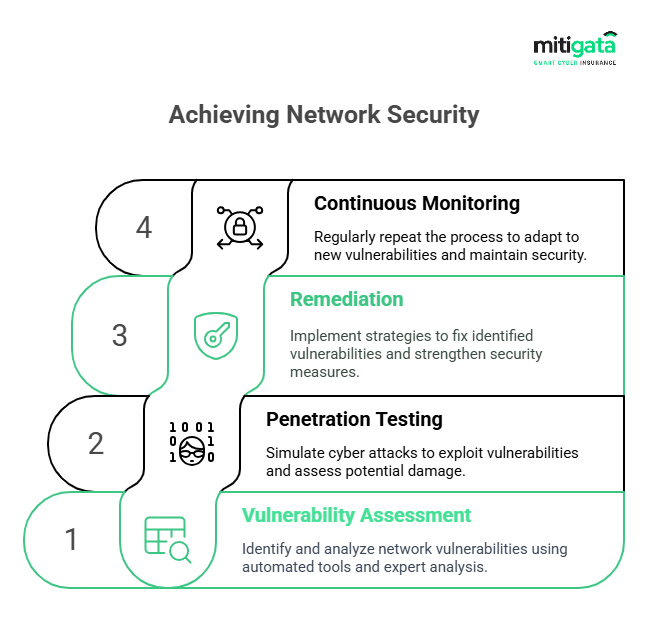
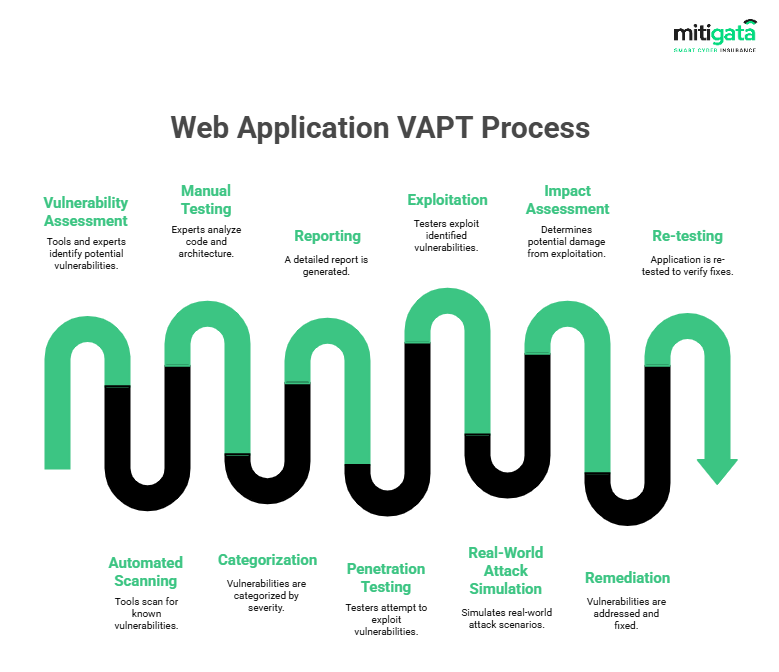
Web Application VAPT:
Focuses on security flaws within web applications.
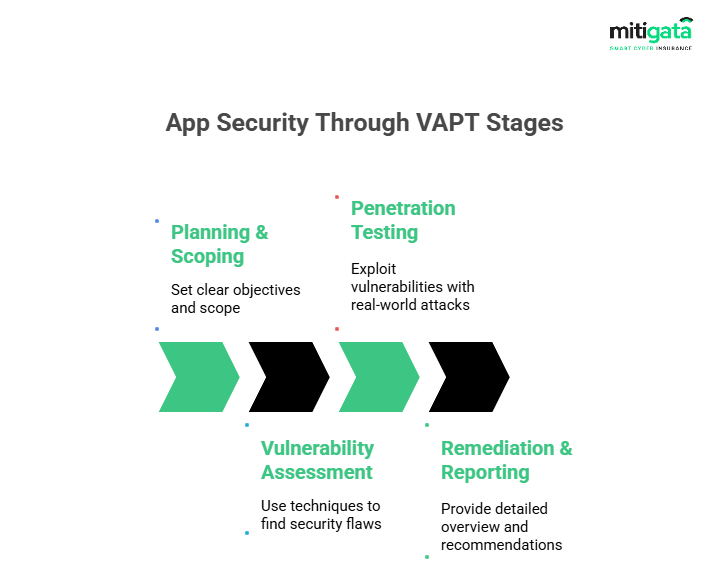
Mobile Application VAPT:
Evaluate security for mobile apps.
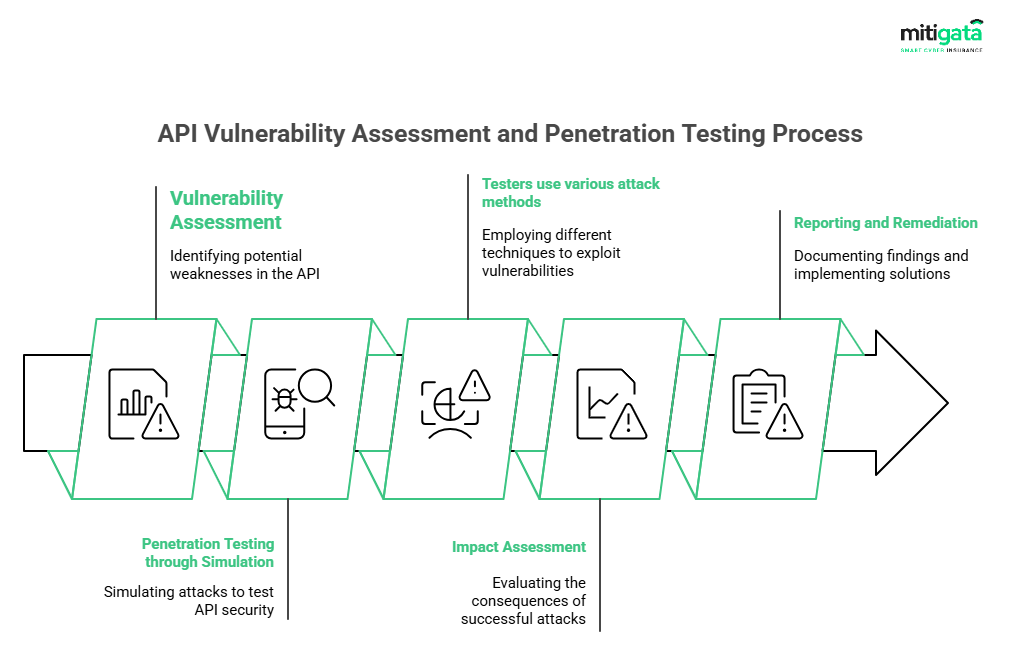
API VAPT:
Tests for security issues in APIs.
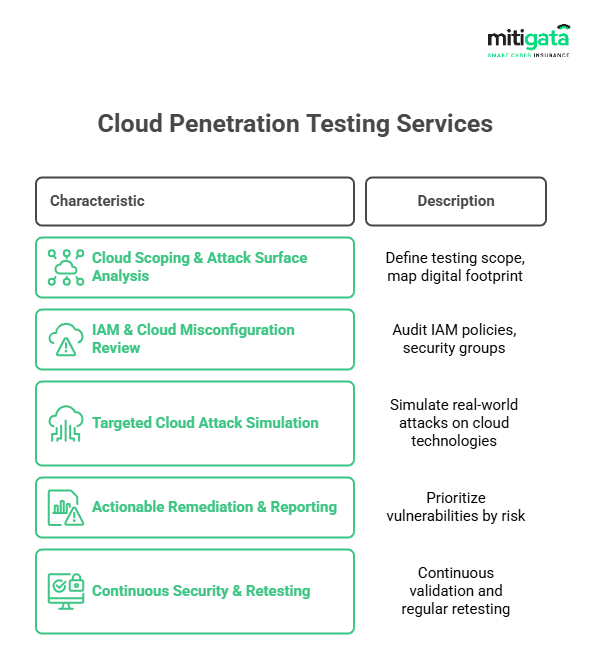
Cloud VAPT:
Ensures cloud environments are secure.
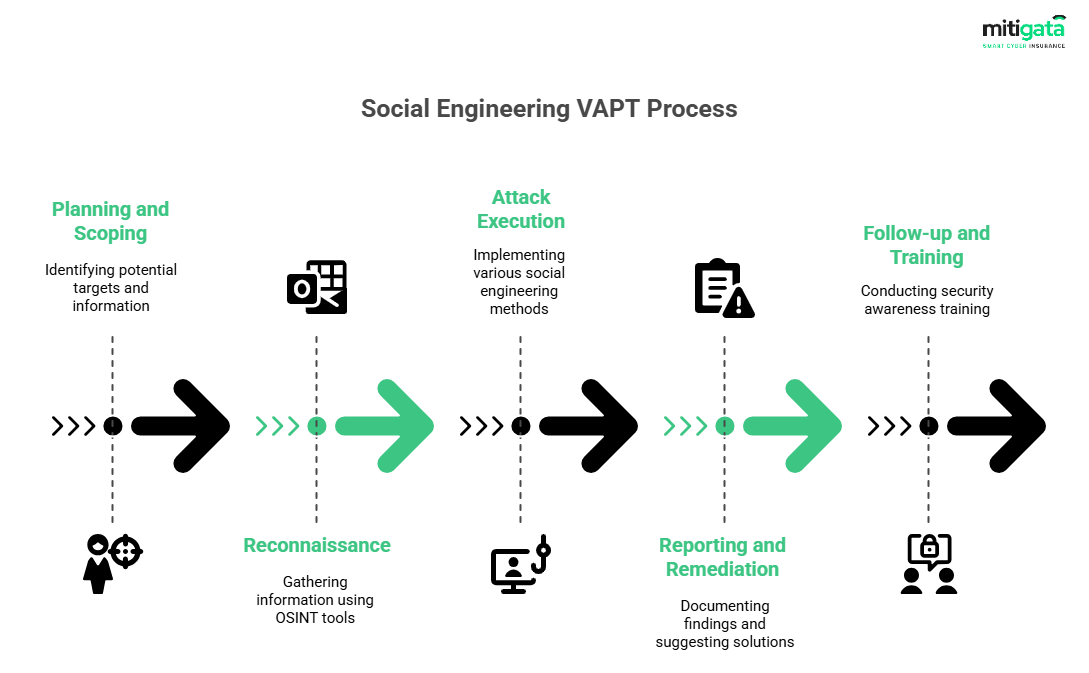
Social Engineering VAPT:
Tests the human element through phishing and other techniques.
Learn to file a cyber insurance claim in minutes!
Know Exactly Where You’re Exposed
Mitigata’s VAPT identifies real-world vulnerabilities before they turn into real-world damage.

Different Methodologies to Conduct VAPT
At Mitigata, we offer various VAPT approaches tailored to the needs of our clients:
- Black Box Testing: In Black Box Testing, the tester has no prior knowledge of the system, simulating a real-world external attacker who tries to break into the system.
- White Box Testing: White Box Testing involves full access to the system’s internal structure, allowing testers to identify vulnerabilities that might not be detected in Black Box Testing, much like an insider attack.
- Gray Box Testing: Combining both black box and white box testing, Gray Box Testing simulates an attack from someone with partial knowledge of the system.
- Red Teaming: Red Teaming extends beyond traditional testing by simulating real-world attacks, including social engineering, to evaluate an organization’s comprehensive security posture.
Discover the crucial role of cybersecurity in education
How Does Vulnerability Assessment Differ From Penetration Testing?
| Aspect | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Objective | Identifies vulnerabilities in the system | Simulates a real attack to exploit vulnerabilities |
| Focus | Detection of known vulnerabilities | Exploitation of weaknesses to determine real-world impact |
| Methodology | Automated scans for existing flaws | Manual testing with controlled exploitation of vulnerabilities |
| Result | A list of vulnerabilities with severity ratings | Detailed exploitation of vulnerabilities and potential impact |
How is the VAPT report formed?
A VAPT Report consolidates findings from both vulnerability assessments and penetration tests. Here’s how the report is structured:
- Executive Summary: A brief overview of key findings and recommendations.
- Methodology: Describes the tools and testing approach used.
- Findings and Vulnerabilities: Detailed listing of vulnerabilities found, categorised by severity.
- Remediation Plan: Provides actionable steps to address the identified vulnerabilities.
- Appendices: Supporting data like scan results and exploit examples.
Key Elements Included:
- Severity Classification: Vulnerabilities are categorized by severity.
- Risk Analysis: Helps prioritise remediation efforts.
- Compliance Assessment: Identifies compliance gaps related to standards like ISO 27001 or SOC 2.
Top Cybersecurity Risks & Solutions for Businesses in 2025!
Why Choose Mitigata for Vulnerability Assessment and Penetration Testing?
Mitigata offers comprehensive VAPT services designed to keep your organisation secure against evolving cyber threats. With Mitigata’s Console, you can access detailed VAPT reports, schedule regular scans, and track vulnerabilities over time.
Understand why Continuous VAPT is necessary-
Mitigata understands the necessity of Continuous VAPT in a rapidly changing cyber landscape. Here’s why continuous testing is crucial:
- Evolving Threat Landscape: New attack methods emerge constantly, requiring ongoing security assessments.
- Timely Detection and Response: Continuous monitoring ensures vulnerabilities are detected before they can be exploited.
- Compliance Requirements: Regular VAPT assessments help meet regulatory standards.
- Third-Party Risks: Ongoing VAPT can identify vulnerabilities introduced by third-party integrations.
VAPT Services at a Affordabled Prices Partner With Mitigata Today!
Our VAPT services and Mitigata Console provide you with the tools to continuously monitor your security.

Below is the list of the Top 10 VAPT Tools that Mitigata uses to provide you with the best VAPT solution.
Which are the Best VAPT Tools in the Market?
Mitigata offers robust protection for your systems and applications, safeguarding them from evolving cyber threats. Our VAPT services, combined with the Mitigata Console, enable you to continuously monitor your security posture and promptly address vulnerabilities, thereby preventing exploitation.
By integrating industry-leading tools with comprehensive vulnerability assessments, Mitigata ensures your business remains secure. Act today to protect your assets with Mitigata VAPT services.
The top VAPT tools that rank in our chart are:
- Tenable Nessus
- HCL AppScan
- Port Swigger Burp Suite Pro
- Nuclei
- Intruder
- Breachlock
- ScoutSuite
- SkylArk
- Checkmarx
- FireTail
Conclusion
As we learnt about cyber threats, VAPT is indispensable for proactive security. This dual process identifies and tests vulnerabilities across your systems, from networks to applications, providing crucial insights.
Given the ever-evolving threat landscape, continuous VAPT is vital for timely detection and robust defense. Don’t wait for a breach; implement a comprehensive VAPT strategy today with Mitigata to secure your digital assets and safeguard your business’s future.
Frequently asked questions (FAQs)
What is VAPT in cybersecurity?
VAPT (Vulnerability Assessment and Penetration Testing) is a cybersecurity practice that combines vulnerability assessment (identifying flaws) and penetration testing (simulating attacks to exploit weaknesses) to identify and remediate security vulnerabilities.
What is the difference between VAPT and penetration testing (pentest)?
Vulnerability assessments pinpoint potential weaknesses that can be proactively addressed. Penetration testing, on the other hand, reveals exploitable vulnerabilities that could lead to unauthorized access.
What is the cost of VAPT certification?
Mitigata provides Vulnerability and Penetration Testing services starting at as low as INR 50,000, depending on the features you choose to opt for.
What are the five stages of Pentesting?
Penetration testing involves five distinct phases: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting.
How to prepare a VAPT report?
Crafting an Effective Penetration Testing Report requires the following practices–
- Tailor to Your Audience: Understand who will be reading the report to convey information effectively.
- Structure for Clarity: Employ a consistent and logical layout to enhance readability and clarity.
- Highlight Key Findings: Prioritize vulnerabilities based on their severity and potential impact.
- Visualize Data: Incorporate visuals, such as charts and graphs, to illustrate your findings effectively.
- Offer Actionable Advice: Provide clear, concise recommendations for remediation.
At Mitigata, we make your work easy and integrate all the tasks to prepare the best VAPT report for your business.

