According to the Verizon 2025 Data Breach Investigations Report, over 12000 data breach cases were reported worldwide, and almost 44% of breaches were due to ransomware.
What is more frightening is that the largest part of data leaks was due to insider threats or human errors. Traditional tools like firewalls and antivirus software cannot handle the sensitive information transfer in hybrid and cloud environments. This is where Data Loss Prevention (DLP) comes into play.
Why Businesses Choose Mitigata for DLP Security
Mitigata is India’s leading cyber resilience company, trusted by over 800+ organisations across 25+ industries. We are partnered with top OEMs and offer you the best security solutions at the best market rates.
Reasons why our DLP services are best in the market:
- Data Classification & Discovery – Automatically identifies and classifies sensitive data.
- 24/7 Specialist Support – Our team will be available for you throughout your demo and deployment process.
- OCR on Endpoint – Detects sensitive content in images, screenshots, and PDFs.
- Affordable Solutions – Get the best enterprise-grade solutions at the lowest market prices with no extra training fees.
- Visual Labelling & Manual Classification – Allows user-driven classification with visible sensitivity markers.
- Device Control & External Media Management – Manages USBs and removable media with granular policies.
- Clipboard, AirDrop & Browser Protection – Prevents unauthorised sharing via copy-paste, AirDrop, and web forms.
Premium Coverage Only At ₹4,200/Endpoint

What Is DLP Security and How Does It Protect Your Data?
DLP (Data Loss Prevention) is an approach to cybersecurity that allows organisations to discover, keep an eye on and stop the unauthorised transfer or exposure of sensitive data. It ensures that confidential information like customer records, financial data, intellectual property, and compliance-protected files (such as those under GDPR or India’s DPDP Act) are not leaked.Key factors to consider when choosing DLP
Before evaluating vendors, identify your goals. This step directly influences how successful your DLP implementation will be.- Locate sensitive data wherever it resides: endpoints, servers, email, or the cloud.
- Define your main goal: insider leaks prevention, compliance, or IP protection.
- Take opinions from IT, legal, and compliance teams
- Opt for cloud-based DLP, on-premise, or hybrid deployment.
- Schedule a phased rollout for easier adoption.
If you are working to build a stronger security posture, our article on top data leak prevention strategies offers simple steps you can start using now.
Understand Different Types of DLP Solutions
Familiarity with DLP types simplifies the selection process of the right tool for your environment.
Endpoint DLP: Data activities are monitored on laptops, desktops, and USB drives.
Network DLP: Data transfer is monitored across internal and external networks.
Cloud DLP: SaaS and cloud applications like Google Drive or Microsoft 365 are used for securing files.
Email DLP: Sending sensitive information outside the authorised recipients is prevented.
Under a single dashboard for unified visibility, many of the best business DLP tools feature a combination of these functions.
Your Data’s Bodyguard On Duty 24/7

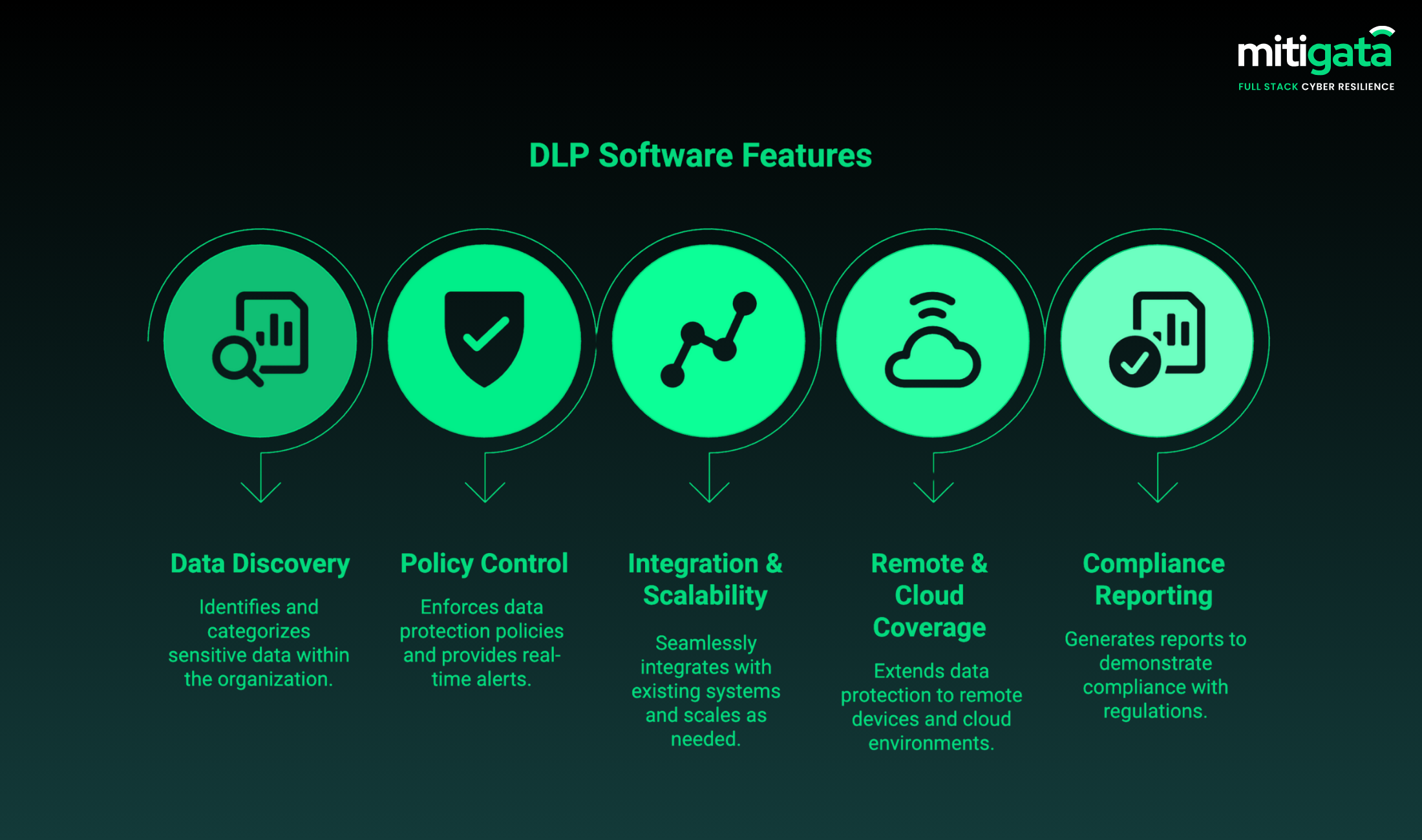
Core Features to Look for in DLP Software
Consider the following key features while selecting the right DLP solution:
Data Discovery and Classification
Your DLP should perform a confidential data detection across devices and storage systems by scanning, tagging, and classifying sensitive data through AI or pattern recognition.
Policy Control and Real-Time Alerts
The team can specify data access and sharing rules using the powerful policy creation tool. Real-time alerts enable prompt actions for violations.
Integration and Scalability
The product should connect easily with SIEM or IAM and grow along with the expansion of your data footprint.
Discover the top DLP providers in 2025 built to handle real-world cyber threats. Compare, test, and choose the right one for your business.

