Would you be more afraid of your competitor or a phishing email you can’t even recognise?
Today, it’s not just your market share that’s under attack. It’s your data, your customers, your money and ultimately, your survival.
The average cost of a data breach has hit $4.88 million, and the people behind these attacks aren’t just lone hackers in basements.
They’re organised criminal groups using advanced tools and AI-generated deepfakes and phishing scams that are nearly impossible to detect.
In 2023, 43% of all cyberattacks targeted small businesses. This year, that number is only growing. And here’s the harsh reality: 60% of small businesses that suffer a cyberattack shut down within six months.
Even the best IT defences can’t stop such attacks. Once a breach happens, your firewall won’t cover your legal fees, customer notifications, or ransom demands. Neither will your general liability insurance.
This is where a strong cyber insurance risk management plan becomes non-negotiable.
Mitigata: Your Trusted Partner for Cyber Risk Insurance

Choosing the right cyber insurance partner is as important as the policy itself. Over 800 companies have trusted Mitigata because we do more than just provide insurance; we actively help prevent incidents before they happen.
Also, we’re proud to have a 100% client retention rate, which speaks volumes in an industry where trust is paramount.
Why Do 800+ Companies Trust Mitigata?
Exclusive Access to Mitigata Console: At the heart of our offering is the Mitigata Console, a powerful tool that provides full visibility into your organisation’s digital risk exposure. With it, you can:
- Identify weaknesses in your systems and networks before attackers can exploit them.
- Train your team with simulated phishing attacks and credential theft to identify the risk of potential attacks.
- Scan the dark web for stolen credentials or sensitive company information.
- Monitor fake domains, phishing pages, and unseen threats targeting your brand in real-time.
Cyber Insurance 1cr Coverage at Just ₹95,000/ Year*
With Mitigata, you get the best market pricing and fast claims—plus proactive defence through our free cyber risk console.

Our clients also value the support and reliability that come with Mitigata:
- 24/7 Expert Guidance: Immediate access to cyber specialists whenever you need them.
- Competitive Pricing: You get the best market rates – what you see is what you pay.
- Complete Coverage: You get full compensation, from investigation and legal defence to business interruption and reputation repair.
- Easy Claim Process: Minimal paperwork, rapid approval, and quick recovery so you can get back to business.
What Is a Cyber Risk Insurance Policy and Why Does It Matter?
Let’s say your business suffers a ransomware attack. Your systems go down. Your operations halt. You’re forced to pay a ransom just to access your own data.
Meanwhile, your customers start calling because their personal information might have been exposed. And suddenly, you are dealing with the costly impact of legal risk, regulatory fines, and reputational damage.
If you look around, businesses across sectors such as manufacturing, fintech, or healthcare deal with such threats daily.
A cyber risk insurance policy covers the specific, high-cost consequences of a cyber incident, including breach response and legal fees, as well as lost income and PR support.
For example:
- If a hacker leaks customer credit card data, cyber insurance can cover the costs of customer notification, credit monitoring, and legal defence.
- If your network is held for ransom, the policy can cover ransom payments and the cost of recovering data.
- If you’re sued for not protecting customer data, you’re covered for legal costs and settlements.
In short, a cyber risk insurance policy turns uncertainty into a manageable risk.
In 2024, 75% of organisations have experienced a SaaS security incident. Read this expertly created guide highlighting the importance of cyber insurance for SAAS companies.
Cyber Liability Insurance Coverage: What’s Typically Included
Understanding what is included in a cyber liability insurance policy can be complicated, but it doesn’t have to be. Generally, policies break out coverage into first-party and third-party coverage:
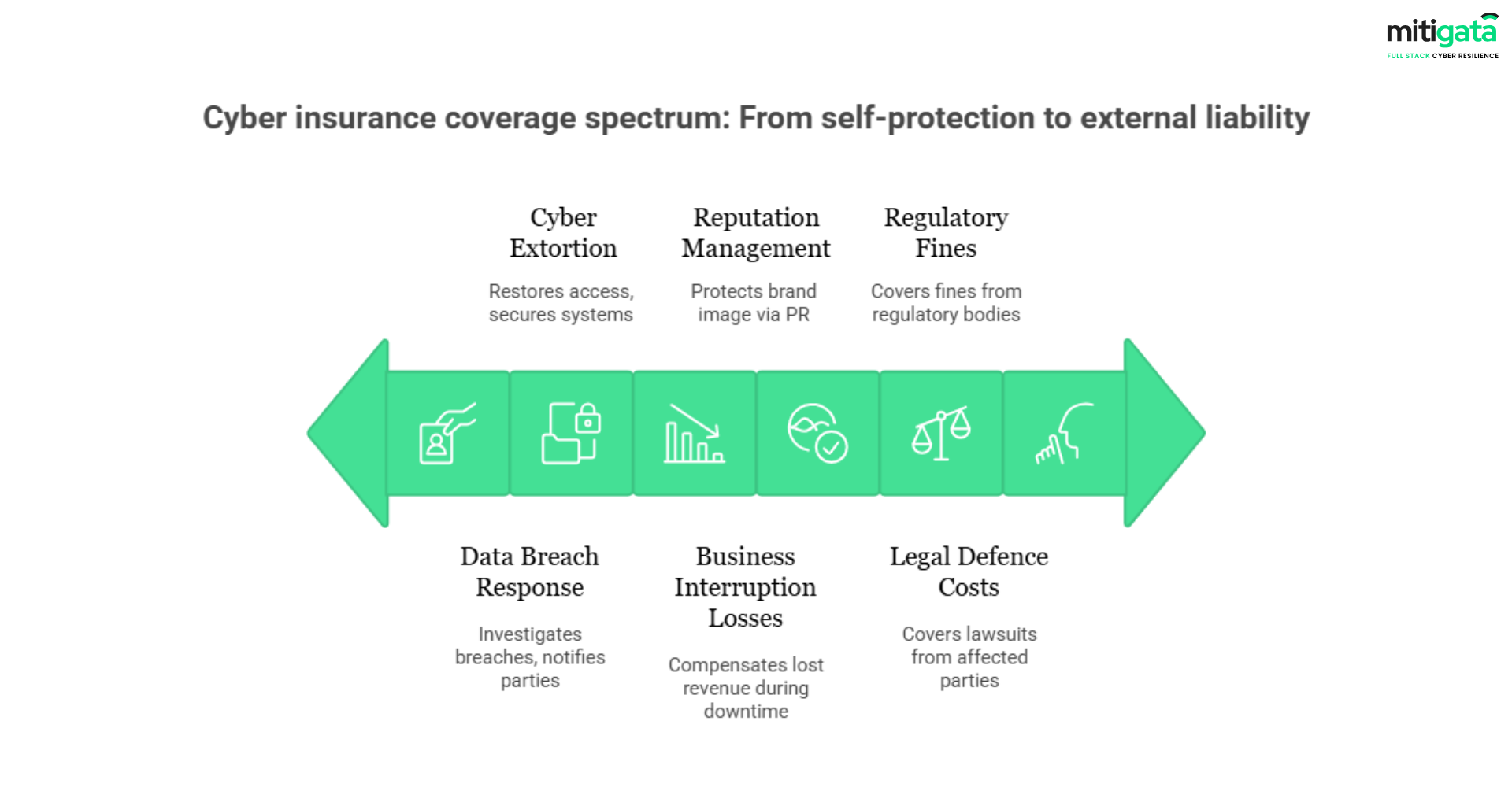
First-Party Coverage (protects your own business):
- Data Breach Response: It includes the costs of investigating breaches and alerting affected parties.
- Ransomware and cyber extortion: Includes payments to restore access and safeguard systems.
- Business Interruption Losses: Compensates for lost revenue during downtime caused by cyber incidents.
- Reputation Management: Covers PR and communication efforts to protect brand image.
Third-Party Coverage (protects your clients or partners impacted by your breach):
- Legal Defence Costs: Provides coverage for lawsuits from clients, partners and/or regulators.
- Regulatory Fines & Penalties: Covers fines imposed by government authorities resulting from a data breach.
- Claims from Customers or Partners: Pays for compensation to clients or partners when their data or systems are breached through your business.
In simple terms, first-party coverage covers your company directly, and third-party coverage protects you against claims from other parties caused by your cyber incident.
Together, the first and third-party policies form a comprehensive cyber risk insurance coverage to help protect your organisation financially.
Don’t let slow claims worsen the damage - Choose Mitigata
Our streamlined claims process ensures fast resolution, supported by experts who understand your business risks and compliance needs.

Common Gaps in Cyber Risk Insurance Coverage You Shouldn’t Ignore
Even the most comprehensive cyber insurance packages may have gaps. Understanding them guarantees that you are not left unprotected. Here are some of the most common gaps to look for:
Social Engineering / Phishing & Business Email Compromise (BEC)
Many standard policies exclude or limit coverage when money or data is lost due to deception (rather than a “traditional” hack). For example, an employee might receive an email impersonating your CFO saying, “Pay vendor X”, and transfer funds. That’s social engineering.
Some insurers treat that as fraud (not hacking) and may deny the claim.
Vendor / Third-Party Breach Liability
You use cloud providers, third-party software, or external service vendors. If their systems are breached and your business suffers downstream losses, that may not be covered unless the policy includes downstream and vendor liability coverage.
Regulatory Penalties, Fines, & Compliance Gaps
Many policies may limit or exclude coverage for fines or penalties imposed by regulators as a result of noncompliance with their laws (for example, data protection, privacy) at the time of the breach.
Just having a cyber insurance risk management policy does not protect you from fines.
Other Situations
Some of the policies may exclude certain types of data (e.g., intellectual property, trade secrets, research-related data) or will only provide coverage for specific vectors of the attacks (e.g., hacking but not insider threats).
War / State-sponsored Attacks
Some insurers exclude state-sponsored or warlike acts. If your region or industry has geopolitical exposure, that exclusion is critical.
The silent clause of cyber insurance war exclusion is enough to put your business at risk. Check out this blog to learn how this exclusion can impact you.
Coverage Sub-limits and Exclusions
Even when the right coverage is included, the actual payout may be limited by sub-limits, waiting periods (delay before coverage kicks in), or high deductibles.
Industry-Specific Cyber Risk Insurance Considerations for SMBs and Enterprises
Cyber threats don’t strike all businesses the same way. The risks you face depend heavily on your industry, and so should your insurance coverage. Below is how risk profiles differ across common industries and how cyber insurance tailored by sector can help:
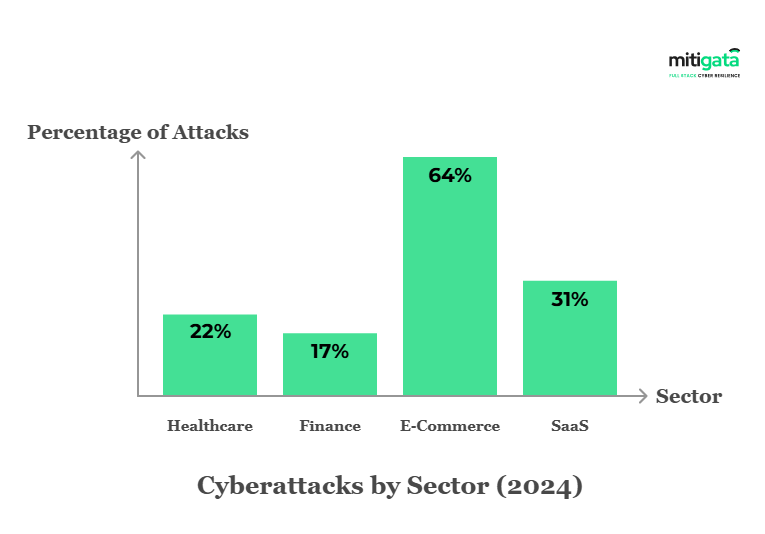
Healthcare
The healthcare industry is one of the most targeted industries in the world. In 2024, cyber attacks healthcare accounted for more than 21% of all cyberattacks in India.
This industry holds significant potential vulnerabilities because of sensitive patient information, medical equipment, and strict adherence to health data privacy laws.
How Insurance Can Help:
- Protects against regulatory fines and penalties for misusing sensitive data.
- Provides breach response for things like notifications to patients and credit monitoring.
- Supports quick recovery of electronic health records (EHRs) to minimise disruption.
Discover key strategies to identify and mitigate cyber risks in healthcare organisations
Finance / Banking / Fintech
The financial sector is one of the most targeted industries. According to statistics, finance and banking had the highest number of victims among other sectors in 2024.
Wire-transfer fraud, embezzlement, and regulatory crackdowns are all potential risks; a single breach can have serious consequences on your finances and reputation.
How Insurance Can Help:
- Prevents fraud and unlawful fund transfers.
- Covers legal defence and regulatory fines.
- Provides vendor liability protection if a third-party API or gateway is compromised.
Discover more on cyber insurance safeguards fintech companies and explore Mitigata’s insights on this.
Technology / Software / SaaS
If you run a SaaS company, then you rely heavily on APIs, cloud-based infrastructure and a software supply chain. Here, even one breach in a part of the supply chain or in your product can potentially cause a domino effect for many clients.
How insurance helps:
- Liability coverage if clients’ data is exposed due to your software.
- Post-breach services and costs for system restoration.
- Intellectual property protection to safeguard against theft or misuse.
Explore more the need of cyber insurance for SaaS businesses to protect against data breaches and service disruptions
Retail / E-Commerce
Retailers handle large volumes of personal data (billing, PII) and payment card information, making retail and e-commerce prime hunting grounds for attackers. Breaches here don’t just cost money – they cost customer trust.
How insurance helps:
- PCI compliance support to avoid fines and penalties.
- Breach response services, including customer communication and PR management.
- Coverage for reputation repair and credit monitoring costs.
Learn more about how eCommerce platforms can safeguard customer data and financial transactions with the right cyber insurance coverage.
What to Look for in a Cyber Insurance Policy and Provider
Choosing cyber insurance isn’t just about price. The right provider gives real protection, not just paperwork. Here’s what to check before you buy:
Coverage Scope
- Must cover both first-party (your losses) and third-party (claims against you).
- Look for inclusion of social engineering, ransomware, vendor breaches, and regulatory fines.
- Watch for hidden sublimits on business interruption or legal defence.
Provider’s Credibility
- Strong financial rating (A or higher) and proven experience in cyber claims.
- High client retention and positive case studies show trustworthiness.
Claims Process
- Fast, simple claims with minimal paperwork.
- 24/7 response teams to support you during incidents.
Learn how to smoothly handle a cyber insurance claim with Mitigata’s step-by-step guide
Pricing Transparency
- Clear, predictable premiums without hidden fees.
- Ability to compare cyber insurance policies with quotes upfront.
Risk Management
- Proactive tools like training, monitoring, phishing simulations, and risk assessments.
- A provider who helps prevent incidents, not just pay after.
Flexibility & Growth
- Tailored to your industry risks (healthcare, finance, SaaS, retail, etc.).
- Scalable coverage and optional add-ons (extortion, reputational harm, forensics).
Common Misconceptions About Cyber Insurance
Many business leaders hesitate or delay buying cyber insurance because of misconceptions. Let’s debunk five common ones and show how Mitigata addresses them.
Misconception 1: “Cyber insurance is too expensive”
Reality: Costs depend on risk profile and cyber risk insurance coverage. Mitigata offers transparent, fair pricing with no hidden fees – tailored to your actual risk.
Misconception 2: “I already have general liability insurance, so I don’t need cyber insurance”
Reality: General liability or property policies typically exclude cyber events like data breaches, ransomware, or regulatory fines. Only a cyber-specific policy covers those unique costs.
Misconception 3: “We have strong security, so we don’t need insurance”
Reality: Even with security in place, no system is perfect. Attackers evolve. Cyber insurance covers losses when security fails.
Misconception 4: “One policy fits all businesses”
Reality: Cyber risks differ by industry, scale, and architecture. Mitigata provides personalised cyber insurance based on your unique business and risk profile.
Misconception 5: “Claim processes are long and painful”
Reality: Many providers make claims cumbersome. But with Mitigata’s streamlined claims and 24/7 expert support, you’ll have a fast, hassle-free experience when it matters most.
End-to-end cyber risk coverage backed by Experts
With best-in-market pricing and partnerships with top insurers, we deliver enterprise-grade protection at SMB-friendly costs.

Cyber Risk Insurance Quote & Cost Breakdown
Getting a quote helps you see what coverage actually costs. Here’s a sample cyber insurance cost table based on coverage limits for reference:
| Coverage Limit (AOY) | Estimated Annual Premium Range |
|---|---|
| ₹1 Crore | ₹1 lakh – ₹1.25 lakh |
| ₹5 Crore | ₹1.7 lakh – ₹2 lakh |
| ₹10 Crore | ₹3.5 lakh – ₹4 lakh |
Note: These are illustrative ranges. The actual premium depends on factors like your business size, industry, risk profile, history of security incidents, and chosen sublimits.
Confused between so many insurance providers? Check out these top cyber insurance companies and their comparison in this guide.
Conclusion
A policy with specialised coverage, tailored to your business and risk profile, protects you against potential financial loss from cyber dangers.
We have earned our clients’ trust for a reason: we safeguard over 800 organisations, offer more than 500 cyber products across insurance, security, and compliance, and have a 100% retention rate.
Are you ready to get started? Contact us for a personalised quote today.

