“Cybersecurity is much more than an IT topic, it’s a boardroom topic, a risk management topic, and a business continuity topic,” said John Chambers, Former CEO of Cisco Systems. The manufacturing industry, with its use of operational technology (OT) and valuable IP, is increasingly a prime target for cyber threats. This blog explores the critical role of cyber insurance in manufacturing in safeguarding these vital assets and ensuring operational continuity.
Understanding the Cyber Threat Landscape in Manufacturing
Rising Cyber Attacks on Manufacturing

The manufacturing sector has seen a significant rise in cyber attacks, with ransomware being the most prominent threat. According to ReliaQuest, ransomware attacks on manufacturing increased by 53% from the second half of 2022 to the first half of 2023. Active ransomware groups like LockBit and ALPHV target industrial goods, aerospace, chemicals, and automotive sectors. (ReliaQuest).
The integration of Industry 4.0 technologies has further complicated the cybersecurity landscape. The proliferation of Internet-connected devices has exposed manufacturing ecosystems to vulnerabilities similar to those faced by traditional IT environments. This interconnectedness, while driving innovation, has also multiplied the potential attack vectors for cybercriminals (Deloitte United States).
Intellectual Property Theft
Intellectual property (IP) is a crucial asset for manufacturing companies, encompassing proprietary designs, processes, and technologies. IP theft remains a significant concern, with an estimated annual loss of $300 to $600 billion due to IP theft in the United States alone (Ekran System).
Common Cyber Attack Tactics
- Phishing: This is a social engineering attack performed through email or another communication channel that lures an organization’s employees to provide sensitive data, such as access credentials. Phishing messages are usually in the guise of emails sent from legitimate users, colleagues, or even C-suite members.
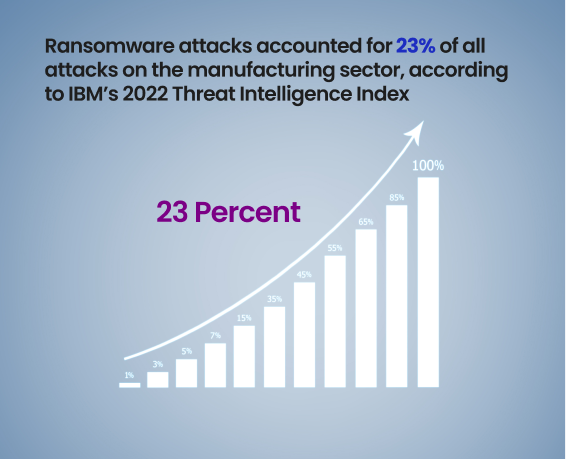
- Ransomware: This type of malware encrypts a computer’s files and demands a ransom for the decryption key. Malicious actors using ransomware can also steal data and threaten to disclose it or sell it to a third party. Ransomware attacks accounted for 23% of all attacks on the manufacturing sector, according to IBM’s 2022 Threat Intelligence Index (Ekran System).
- Brute Force Attacks: These attacks utilize a trial-and-error method to crack login credentials or decryption keys and eventually get access to an organization’s systems and networks. In a brute force attack, hackers repeatedly try username and password combinations until they access your systems with a legitimate account.
- Vulnerability Exploitation: This attack occurs when cybercriminals take advantage of software or network vulnerabilities or security flaws to get access to your data. After a successful attack, cybercriminals can run malicious code in your network and steal your critical data.
- Remote Desktop Protocol (RDP) Attacks: These are cybersecurity attacks executed through RDP connections, aimed at remotely taking full control over a compromised computer or network.
- Insider Attacks: These threats can come from any user inside your network. Insiders can be malicious or negligent, compromising your critical data intentionally or by mistake. Insider threats are more dangerous than external threats since insiders often hold legitimate access to your sensitive data and know your cybersecurity measures well, making it easier for them to bypass those measures and steal or damage your data.
The Financial Impact of Cyber Attacks on Manufacturing
1. Cost of Cyber Incidents
The financial ramifications of cyber incidents in manufacturing are profound. The cost includes ransom payments, fines, business interruption, revenue loss, and reputational damage. A study by Deloitte revealed that 48% of manufacturers identified operational risks, including cybersecurity, as the greatest danger to their smart factory initiatives (Deloitte United States).
2. Business Interruption:
The expense that is associated with cybercrime isn’t just related to responding to and remediating it. It includes the expenses and losses incurred as part of business operations and daily procedures interrupted, which need to be made operational again.
3. Response Costs:
This refers to the increasing amount spent on responding to a cyberattack, which includes incident costs, legal and forensic expertise, ransomware demands, cybersecurity measures, and more. For example, the response costs for a ransomware attack can be substantial, involving forensic investigations, legal fees, public relations efforts, and IT remediation costs.

Real-Life Incidents
In May 2023, the China-based advanced persistent threat group Volt Typhoon targeted U.S. critical national infrastructure, including manufacturing. This attack highlighted the persistent threat of nation-state actors aiming to steal IP and disrupt operations. Similarly, the hacktivist group Killnet has been known to target manufacturing entities with distributed denial of service (DDoS) attacks, aiming to cause disruption.
The Role of Cyber Insurance in Manufacturing
What is Cyber Insurance?
Cyber insurance provides financial protection and support in the event of a cyber incident. Policies typically cover costs associated with data breaches, business interruption, ransomware attacks, legal fees, and public relations efforts to mitigate reputational damage (Astra) (Deloitte United States).
Benefits of Cyber Insurance for Manufacturing
- Financial Protection: Cyber insurance helps cover the substantial costs incurred from cyber incidents, including ransom payments, legal fees, and business interruption losses. For example, the average cost of a data breach in 2023 was estimated to be $4.45 million (Deloitte United States).
- Risk Management: Insurers often provide risk management services, helping manufacturers identify vulnerabilities and implement robust security measures. This can include regular risk assessments, employee training, and cybersecurity audits.
- Incident Response: Cyber insurance policies usually include access to incident response teams that assist in quickly addressing and mitigating cyber threats. These teams are critical in minimizing the impact of an attack and ensuring a swift recovery (Deloitte United States).
- Regulatory Compliance: Cyber insurance aids in ensuring compliance with industry regulations and standards, thereby avoiding potential fines and penalties. Compliance with regulations such as GDPR, CCPA, and others is essential for avoiding hefty fines and maintaining business operations.
Key Statistics

Best Practices for Enhancing Cybersecurity in Manufacturing
1. Aligning IT and OT Security
Manufacturers must ensure that their IT and OT security strategies are aligned. This involves clear documentation of cybersecurity services, assigning roles and responsibilities, and conducting OT-specific training and awareness programs. Regular risk assessments and consistent control frameworks are essential for maintaining robust cybersecurity measures (Deloitte United States).
- Document Cybersecurity Services: Clearly document cybersecurity services, roles, and responsibilities among IT and OT team members down to the site level. Conduct training and awareness programs specific to OT cybersecurity (Deloitte United States).
- Regular Risk Assessments: Perform regular risk assessments to identify and prioritize potential risks to your intellectual property and operational technology. Implement a periodic risk assessment review to keep pace with evolving cybersecurity threats.
- Consistent Control Framework: Develop a consistent control framework with documented policies and standards. Define key risk indicators (KRIs) and key performance indicators (KPIs) to measure the effectiveness of the OT cybersecurity program (Deloitte United States).
2. Improving OT Asset Visibility
Effective maintenance of asset inventories and continuous monitoring are critical for understanding and mitigating cybersecurity risks. Enhanced visibility into technology communications can help in network segmentation efforts and other security projects (Deloitte United States).
- Automated Asset Inventories: Implement automated visibility solutions to maintain consistent and accurate inventories of OT assets. This enables better understanding and focused risk assessments (Deloitte United States).
- Continuous Monitoring: Enable continuous monitoring through logs from visibility solutions to detect potential indicators of compromise and respond promptly to threats.
- Network Segmentation: Securely separate IT from OT networks with physical firewalls and minimize direct internet connectivity to OT systems. Use Windows Active Directory structures for segmentation efforts in OT environments (Deloitte United States).
3. Network Segmentation and Access Management
Manufacturers should securely separate IT and OT networks, minimize OT internet connectivity, and implement stringent access controls. Periodic reviews of access permissions and secure remote access solutions are crucial for protecting sensitive data (Deloitte United States) (Deloitte United States).
- Segmentation Efforts: Limit connectivity by securely separating IT from OT networks using physical firewalls and other security measures. This minimizes potential attack vectors and helps contain breaches if they occur (Deloitte United States).
- Access Controls: Implement stringent access controls to restrict who can access OT systems. Use multi-factor authentication (MFA) and role-based access control (RBAC) to ensure only authorized personnel can make changes (Ekran System).
- Secure Remote Access: Ensure that remote access solutions are secure, especially for employees or third-party vendors who need to access OT systems remotely. This can include using VPNs, encrypted connections, and rigorous authentication methods (Deloitte United States).
- Regular Access Reviews: Conduct periodic reviews of access permissions to ensure that only necessary personnel have access to critical systems. Revoke access for individuals who no longer need it and regularly update access policies to reflect changing roles.
4. Employee Training and Awareness
Human error is a significant factor in many cyber incidents. Manufacturers should invest in comprehensive cybersecurity training to educate employees on the latest threats and best practices for protecting sensitive information.
- Regular Training Sessions: Conduct regular cybersecurity training for employees on phishing recognition, password management, and safe internet practices (Ekran System).
- Phishing Simulations: Implement phishing simulation exercises to test employee awareness and preparedness. Use the results to provide targeted training and improve overall resilience (ReliaQuest).
- Awareness Campaigns: Run ongoing awareness campaigns to keep cybersecurity top of mind for all employees. Use posters, emails, and other communication channels to share tips and updates (Deloitte United States).
5. Incident Response Planning
A well-defined incident response plan is crucial for quickly and effectively addressing cyber incidents. Manufacturers should develop and regularly update their incident response plans to prepare for various scenarios.
- Incident Response Teams: Establish dedicated incident response teams with clear roles and responsibilities. Ensure team members are trained and equipped to handle various types of cyber incidents (Ekran System).
- Regular Drills: Conduct regular incident response drills to test the effectiveness of the response plan and identify areas for improvement. Simulate different types of cyber incidents to ensure comprehensive preparedness (ReliaQuest).
- Communication Plans: Develop communication plans to inform stakeholders, including employees, customers, and regulators, in the event of a cyber incident. Clear and timely communication can help manage the situation and minimize reputational damage.
Conclusion
The manufacturing industry faces unique cybersecurity challenges due to its reliance on operational technology and valuable intellectual property. Cyber insurance is crucial for protecting these assets and ensuring operational continuity amid rising cyber threats.
Understanding cyber threats, assessing financial impacts, and implementing best practices help manufacturers safeguard their operations and intellectual property. Cyber insurance provides an additional layer of protection, helping to mitigate the financial and operational impacts of cyber incidents.
- Investing in comprehensive cybersecurity measures and cyber insurance ensures the resilience and future success of the manufacturing industry.
- Cyber insurance is essential for mitigating the financial and operational impacts of cyber incidents in the manufacturing sector.
- Manufacturers must align IT and OT security strategies, improve asset visibility, and implement robust access controls.
- Employee training and a well-defined incident response plan are critical components of a comprehensive cybersecurity strategy.
Call to Action:

Secure your manufacturing operations and protect your intellectual property with comprehensive cyber insurance from Mitigata. Learn more about our tailored solutions and how we can help you stay ahead of cyber threats. Visit our website or contact us today to get started.



The article on cyber insurance in the manufacturing industry provides valuable insights into how it helps mitigate risks from cyber threats. It’s an excellent read for manufacturers aiming to safeguard operations against cyberattacks!