Unmasking 2025’s Email Phishing Threats & Protection Strategies
Phishing is the single most common form of cybercrime today, with over 3.4 billion phishing emails sent daily.
That’s more than a trillion scam emails each year. These deceptive emails mimic trusted brands, internal teams, or executives and can result in massive data breaches, fraud, and reputational damage.
At Mitigata, we know that understanding and identifying phishing email types is the first step toward building resilience.
That’s why we offer smart cyber insurance, compliance, and phishing simulation solutions to businesses that want to stay ahead.
Let’s walk through the top phishing scams you need to watch out for in 2025.
Also learn Why Cyber Insurance became a must for Fintech companies? In 2025.
Common Phishing Email Scams of 2025 at One Place!
| Phishing Scam | Overview | How to Spot It |
|---|---|---|
| Fake Invoice Scam | Impersonates a vendor/service provider to request urgent payments. | Unexpected invoices, urgency, and unknown bank accounts. |
| Email Account Upgrade | Fake an IT alert urging the user to upgrade storage or avoid deactivation. | “Dear User,” mismatched URLs, fake login pages. |
| Advance-Fee Scam | Offers large sums in return for upfront fees (inheritance, lottery, etc.). | Big money promises, odd language, and upfront fee requests. |
| Google Docs Scam | Fake sharing notification with a link to a credential-harvesting page. | Strange links, login requests, suspicious sender names. |
| PayPal Scam | Claims account issues and requests urgent login verification. | Brand mimicry, urgent CTA, links not leading to PayPal. |
| Message from HR | Pretends to be internal HR, sharing policy updates or benefits. | Generic greetings, urgent tone, file attachments. |
| Dropbox Scam | Fake shared file notifications mimicking Dropbox. | Suspicious file-sharing invites and login prompts. |
| Aadhaar Phishing (India) | Claims Aadhaar update issues with fake UIDAI branding. | Requests for banking/personal info, urgent language. |
| Unusual Activity Scam | Claims suspicious login activity to provoke user panic. | Fake security alerts, links to spoofed login pages. |
| Fake Job Offer Scam | Offers fake job roles that request resumes, IDs, or bank information. | Unexpected offers, requests for sensitive info, and unverified domains. |
Train Your Workforce With India’s Leading Phishing Simulation
With 500+ businesses secured, Mitigata’s simulations offer experience-based learning, role-specific campaigns, and regular tests

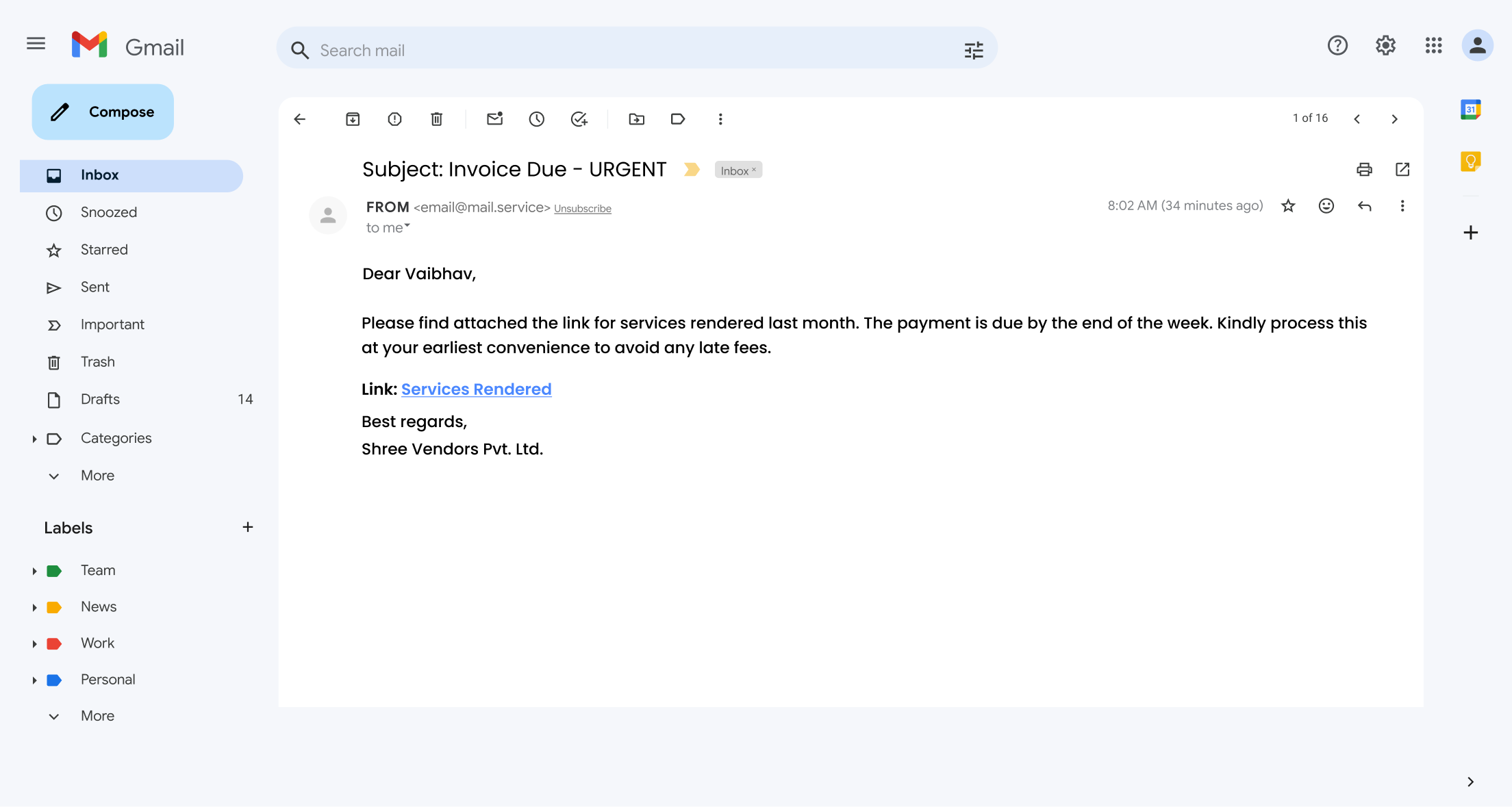
1. Fake Invoice Scam:
This scam specifically targets businesses by disguising itself as a legitimate payment request. Attackers impersonate trusted vendors or service providers, sending fraudulent invoices for services or products never rendered.
Since businesses routinely process many invoices, this deceptive tactic often goes unnoticed. It is a highly effective method for tricking organisations into paying for non-existent bills.
2. Email Account Upgrade:
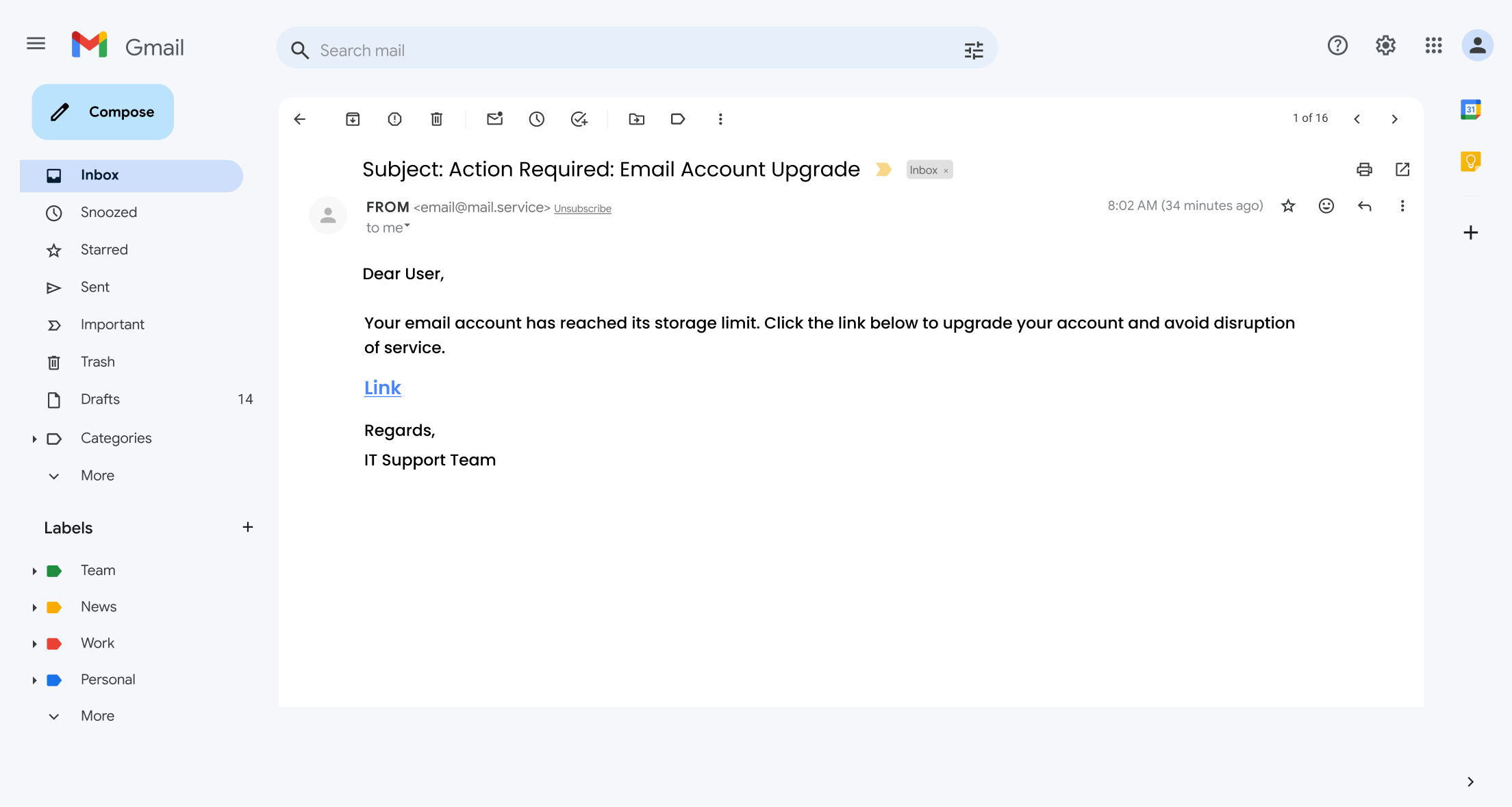
This particular scam cleverly exploits employees’ fear of losing access to vital communication.
The attacker poses as a trusted figure, often from the IT department or a familiar service provider, and then prompts recipients to “upgrade” their email accounts.
This deceptive tactic exploits the critical role email plays in daily operations, making it easy for individuals to compromise their credentials.
3. Advance-Fee Scam:
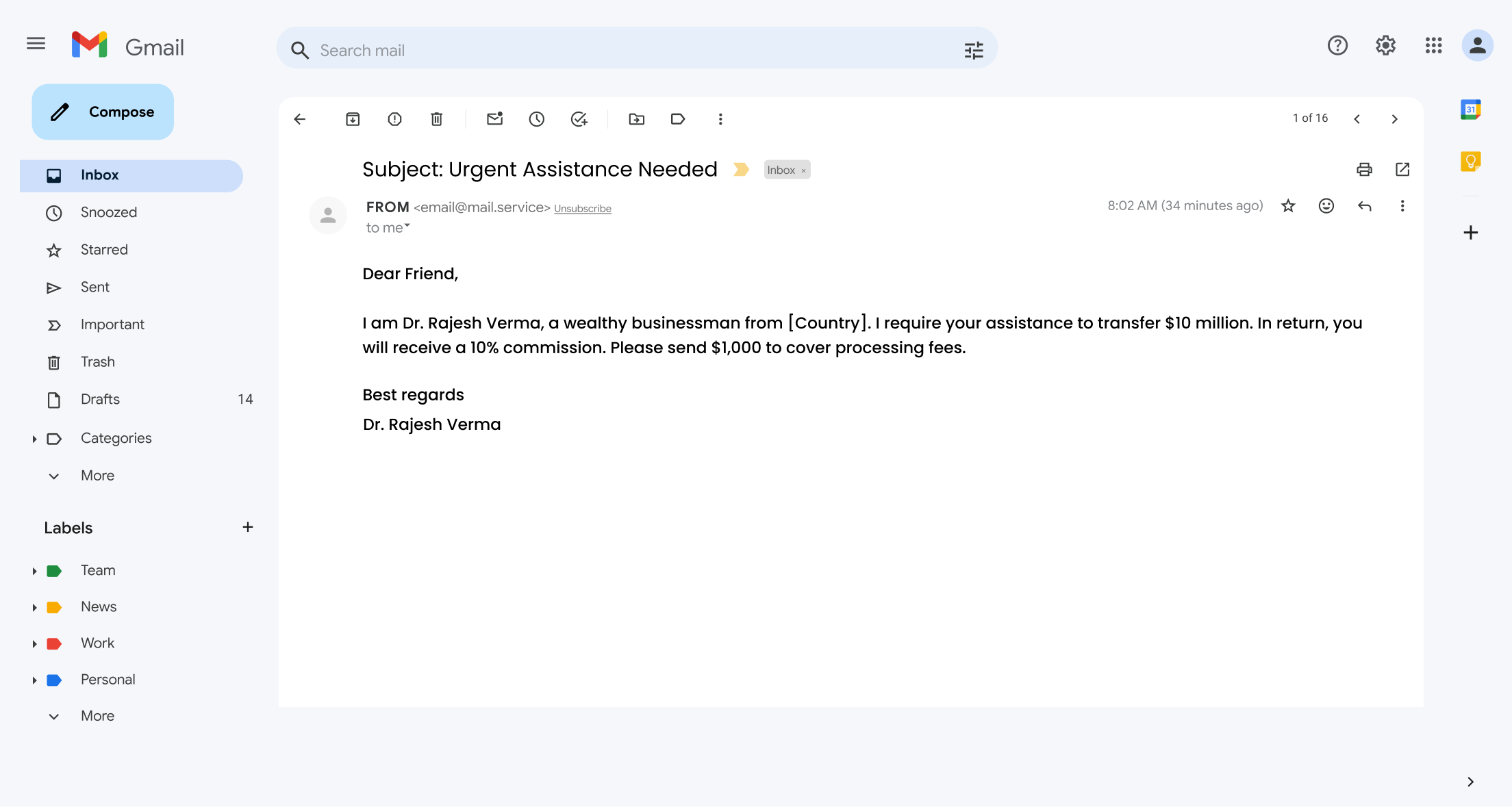
In this scam, the fraudster typically poses as a wealthy individual, a foreign dignitary, or an official who urgently needs assistance in transferring a large sum of money out of a country.
Despite its long and infamous history, this enticing “too good to be true” proposition continues to ensnare victims, primarily by appealing to their hopes of sudden wealth.
4. Google Docs Scam:
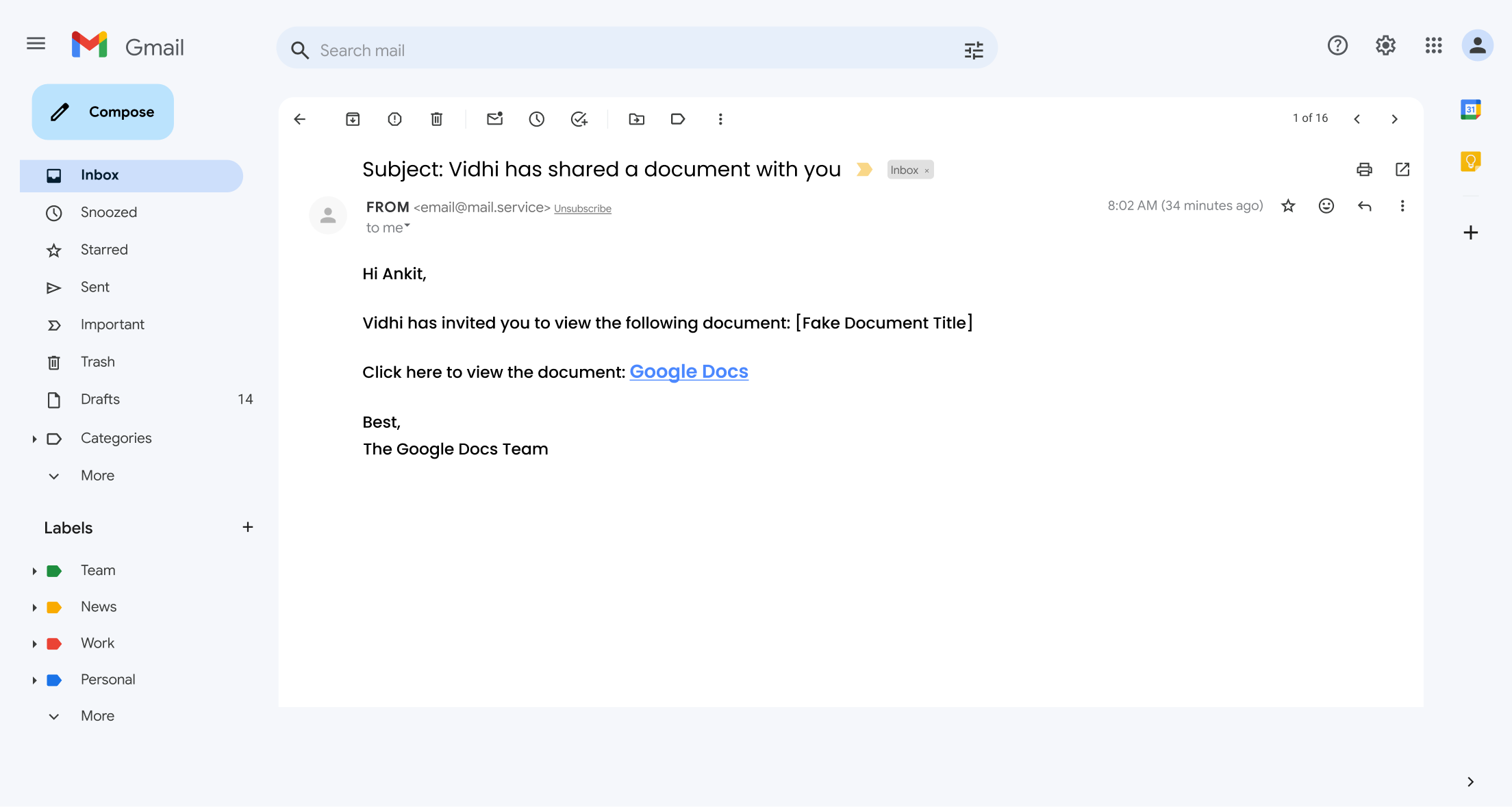
This insidious phishing attempt now targets Google Docs users by sending them a deceptive invitation to view a document, appearing indistinguishable from a legitimate sharing notification.
A trusted platform like Google Docs enables attackers to exploit the routine nature of document sharing to trick users into clicking malicious links and compromising their accounts.
5. PayPal Scam:
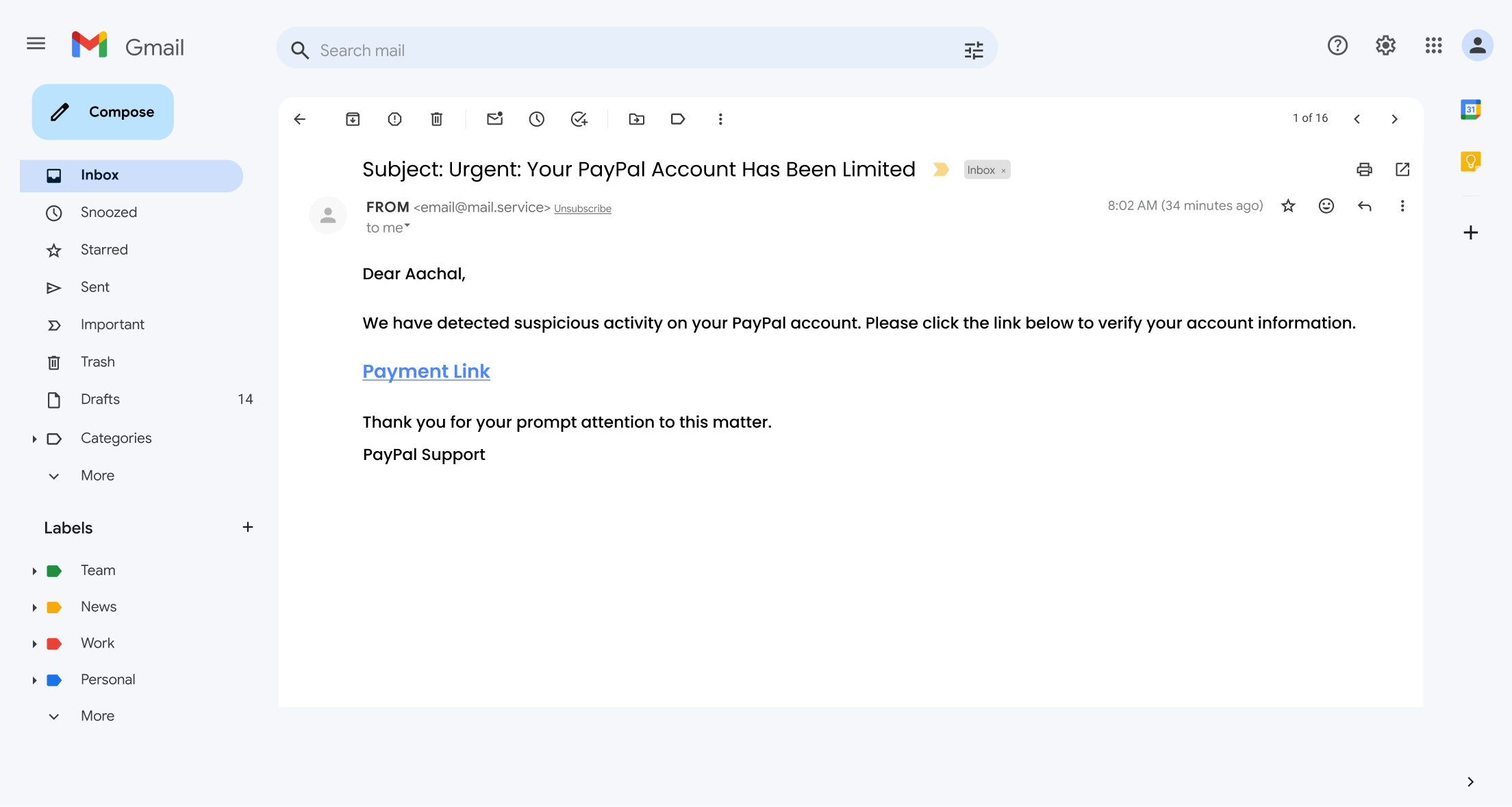
This scam targets PayPal users, capitalising on the high level of trust associated with this popular online payment platform.
Victims receive emails mimicking official PayPal communications, often claiming there are urgent issues with their account or a recent payment has been made.
By exploiting users’ reliance on PayPal for secure transactions, these fraudsters aim to trick individuals into clicking on malicious links and unknowingly revealing their sensitive login credentials.
6. Message from HR:
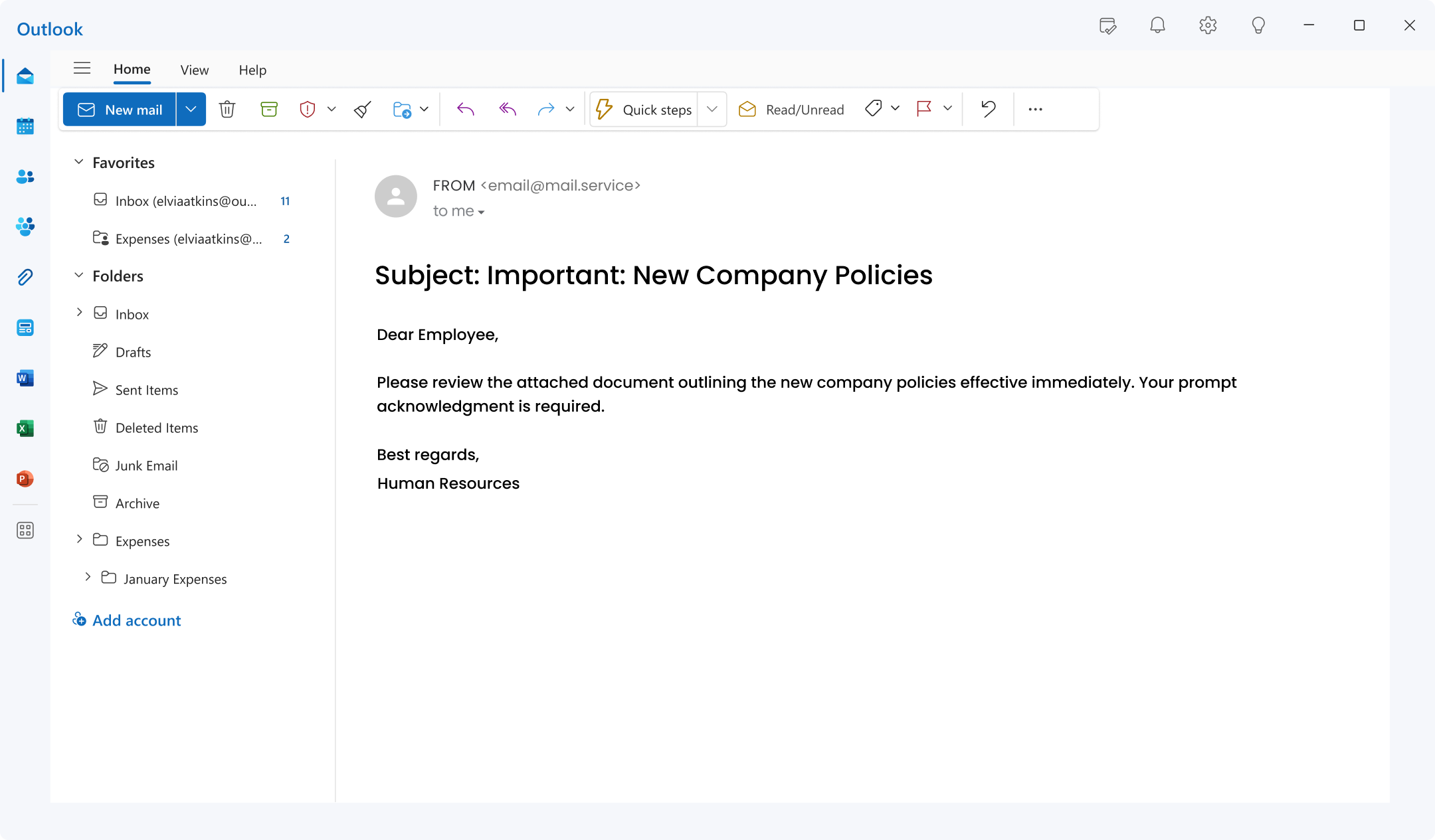
A message from HR is a scam that exploits employees’ inherent trust in internal communications, particularly those related to their benefits and workplace policies.
The attacker carefully impersonates the HR department, sending official-looking emails that announce critical updates, urgent policy changes, or exciting new benefits.
This is also known as a highly effective internal phishing method.
7. Dropbox Scam:
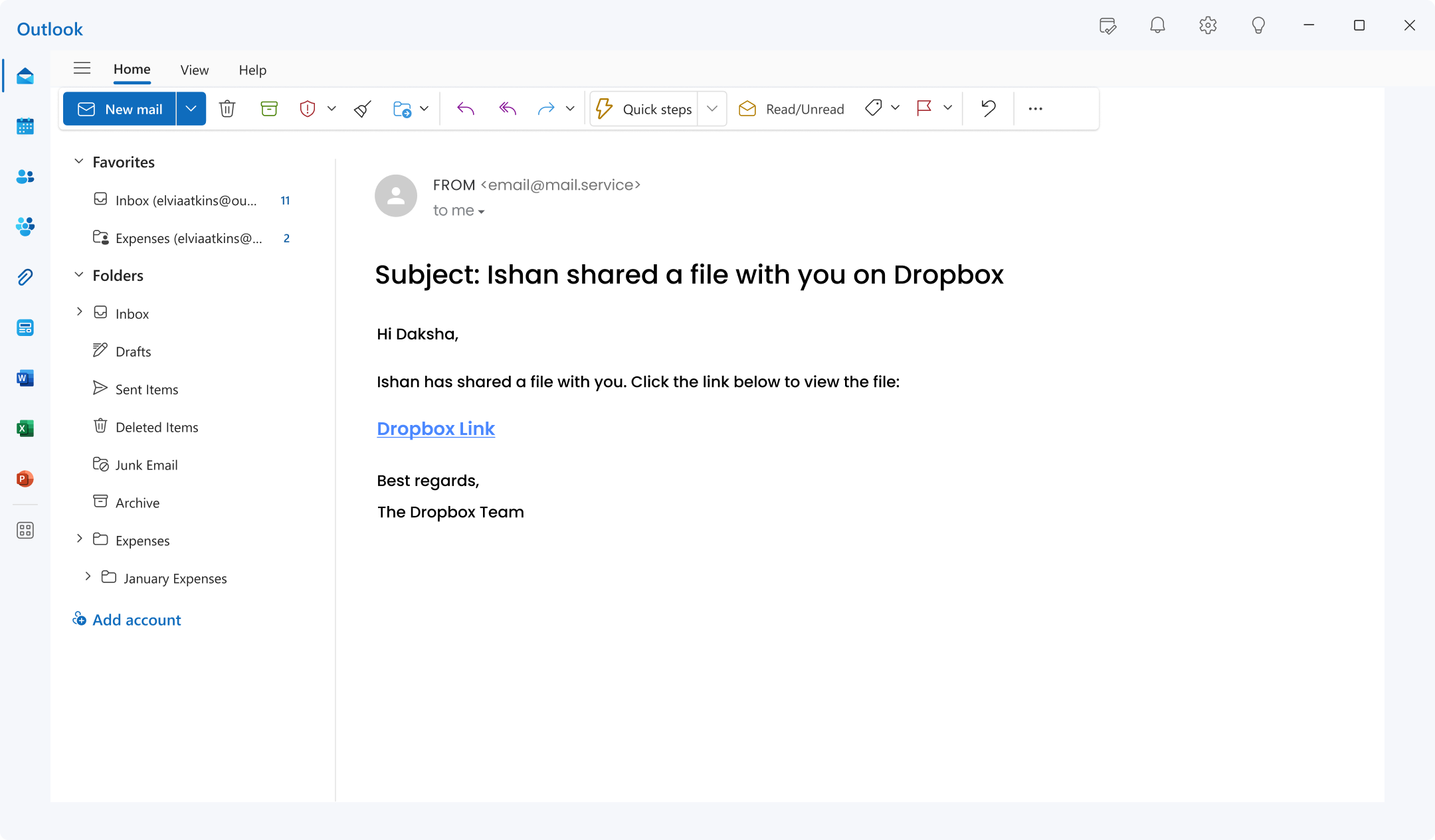
This scam capitalises on the widespread use of Dropbox for file sharing and collaboration. Attackers send fraudulent notifications to users, cleverly mimicking legitimate alerts about shared files or urgent requests for action within the platform.
By exploiting the routine nature of Dropbox interactions, these deceptive messages trick users into clicking on malicious links, potentially compromising their credentials or devices.
8. Aadhaar Phishing (India):
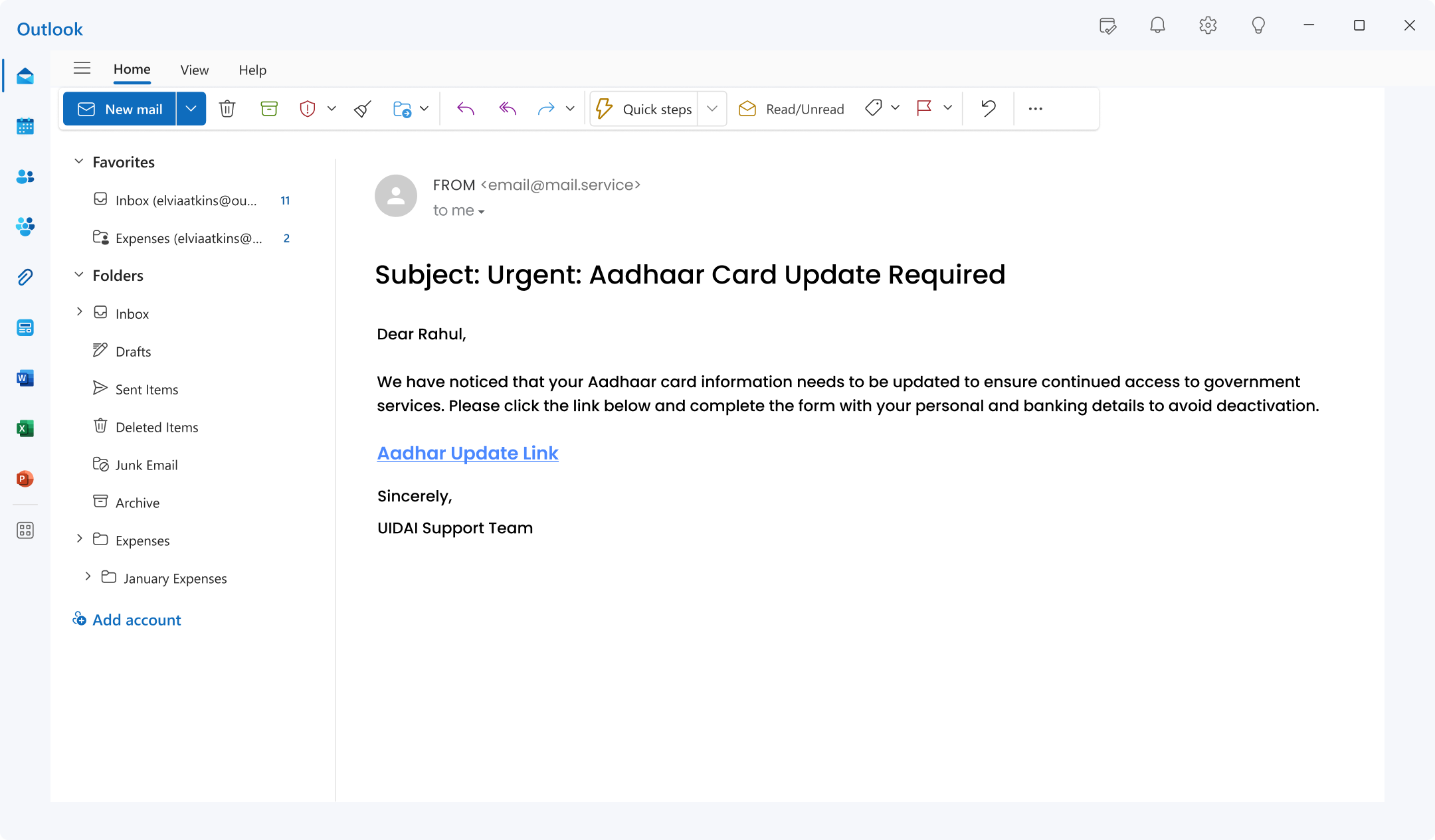
The Aadhaar card is of critical importance in India. Victims receive deceptive emails asserting an urgent issue with their Aadhaar, such as a supposed need for immediate verification or an update.
Recipients’ concern about maintaining their official records, combined with the card’s essential role in various services,
Makes these fraudulent messages particularly effective at tricking individuals into clicking malicious links or disclosing sensitive personal information.
9. Unusual Activity Scam:
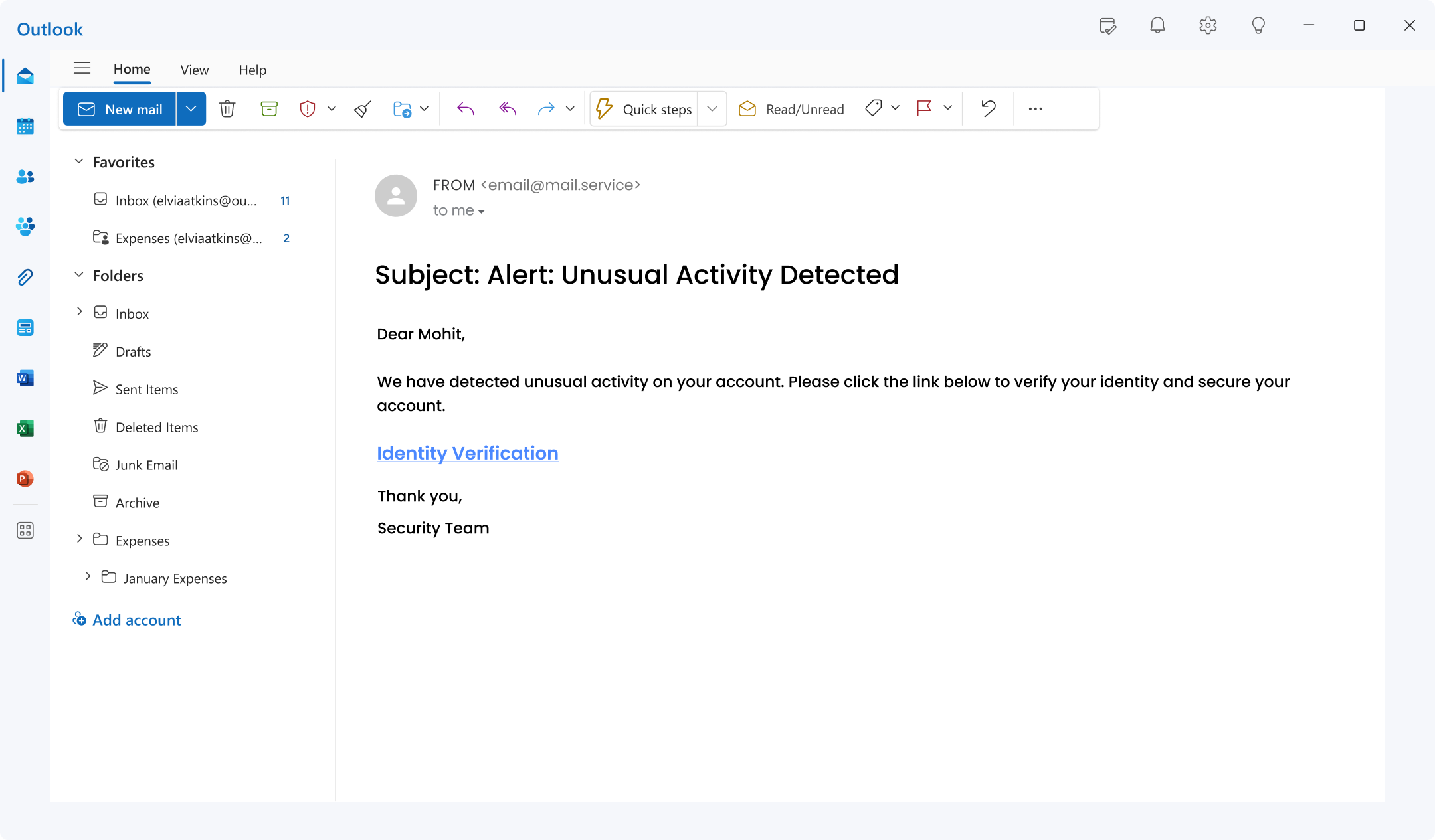
This pervasive phishing tactic preys on fear and urgency, designed to elicit an immediate, unthinking response from recipients.
The email falsely claims to have detected unusual or suspicious activity on the user’s account, often citing unauthorised logins or transactions as evidence.
Therefore, creating panic in recipients to click and fall prey to the scam.
10. Fake Job Offer Scam:
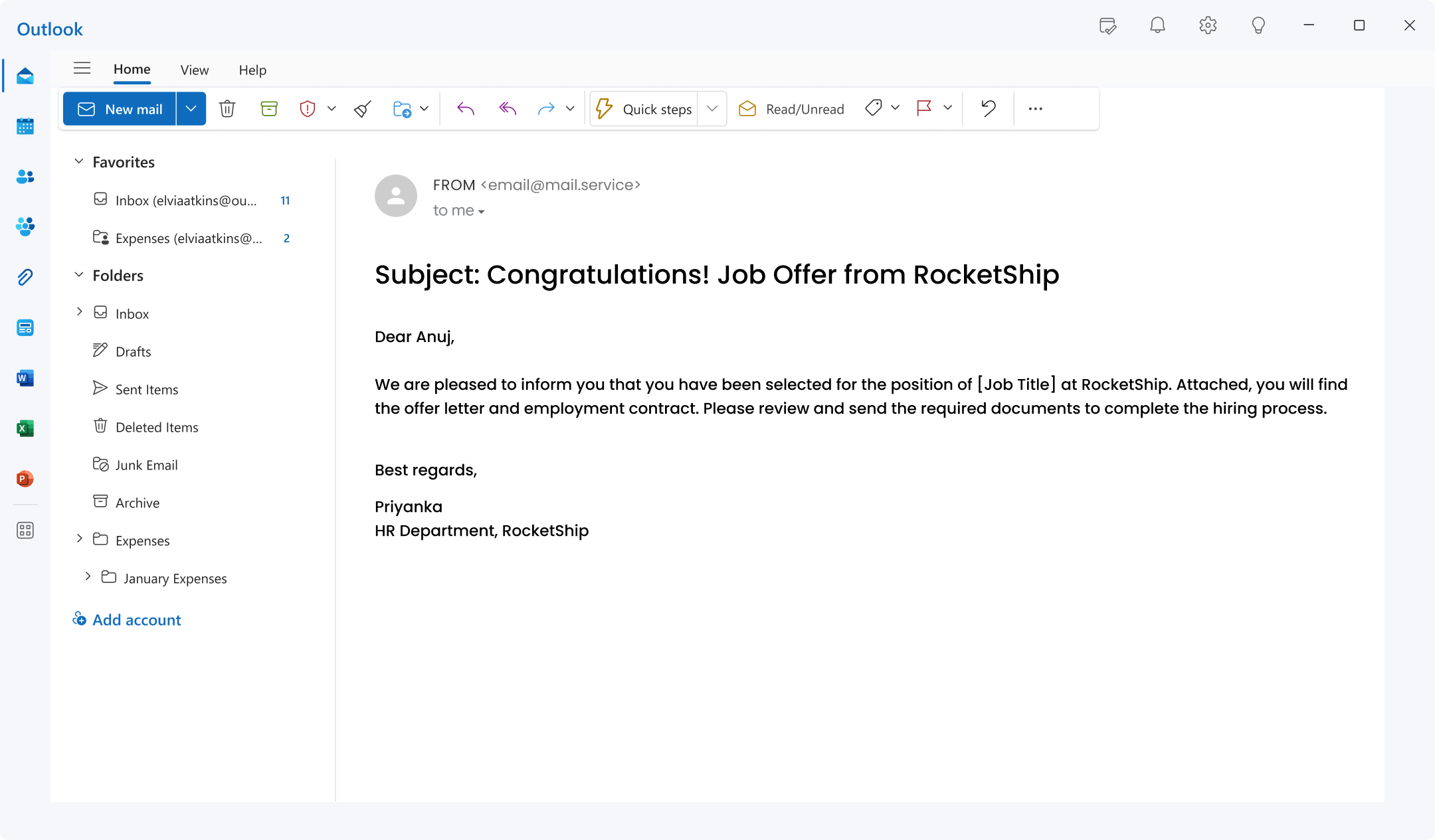
This phishing email specifically targets hopeful job seekers, focusing on their aspirations for new career opportunities.
The attacker meticulously crafts a fraudulent message that impersonates a recruiter or HR representative from a well-known, legitimate company.
By enticing recipients with an incredibly attractive job offer, this scam aims to trick individuals into clicking malicious links, divulging personal information, or making upfront payments for fake “background checks” or “training materials.”
Build a Phishing-Resistant Workforce With Role-Specific Simulations
With Mitigata’s phishing simulation, employees face realistic phishing attacks, get immediate feedback, and improve with follow-up training.

How AI is Reshaping Phishing Attacks in 2025?
While phishing kits and phishing-as-a-service tools are already widely used, attackers in 2025 are now supercharging their campaigns with the aid of AI. Think of:
- Deepfake videos/voice calls impersonating executives.
- AI-generated phishing emails often utilize scraped social media data.
- Multi-channel attacks across Slack, Teams, email, and SMS.
Yet, mass AI phishing hasn’t taken over just yet. A Hoxhunt study showed that only 0.7% to 4.7% of phishing emails analyzed in 2024 were written by AI.
But spear phishing—targeted and convincing—is fast becoming AI-enhanced.
Curious about Cyber Insurance Cost in India: Coverage & Premiums, then explore it.
Phishing by the Numbers: How Bad Is It?
- A 1,000-employee company receives ~2,330 phishing emails/year.
- Phishing is a leading cause of data breaches, accounting for 90% of breaches.
- Human mistake is a major contributor to successful phishing attacks, with 86% of organisations reporting phishing attempts and more than 70% suffering compromises as a result.
Different industries are hit harder:
| Industry | Phish / 1K Org | % Reduction via Hoxhunt |
|---|---|---|
| Media Production | 4610 | 85% |
| Government | 3010 | 85% |
| Manufacturing & Construction | 2540 | 84% |
| Financial Services | 1990 | 89% |
| Oil & Energy | 1820 | 87% |
Reduce your phishing incident Rates by over 85%
We evaluate, compare, and recommend the best Email Security Tools at the Best Rates

Categories of Phishing Emails (A Quick Breakdown)
Here are some of the main categories phishing emails fall into:
- Credential Phishing: Stealing login details (e.g., Microsoft 365, Google Workspace)
- HTTPS Phishing: Using secure-looking links to seem legitimate (80% phishing sites use HTTPS)
- Voice Phishing (Vishing): Phone calls impersonating HR/officials
- QR Code Phishing (Quishing): QR codes redirecting to malicious sites
- Brand Impersonation: Fake domains mimicking companies like Microsoft, Facebook
- Government Impersonation: Emails faking IRS, tax authorities, or law enforcement
Discover the Cyber Insurance Claims Process, Coverage & Eligibility
What Do All Phishing Emails Have in Common?
- Urgency or Threat Language: “Verify now,” “Your account will be locked.”
- Spoofed Sender Details: Appears to be a known name, but from a random domain.
- Fake Links or Attachments: Clicking either leads to credential theft or malware.
Stay Ahead with Mitigata’s Cyber Solutions
At Mitigata, we help you fight email scams with:
- Phishing Simulation Console: Train your teams with real-life phishing templates.
- Smart Cyber Insurance: Minimise the Financial Impact of a Breach.
- Security & Compliance Services: From ISO, DPDP to RBI & SEBI compliance.
Phishing incidents are inevitable. But breaches don’t have to be. Combine proactive defence and cyber insurance with Mitigata. Book a quick consult and we’ll show you how.
Whether it’s protecting against BEC scams, AI-driven threats, or spear-phishing attacks, our end-to-end approach keeps your business resilient.
Conclusion:
Phishing attacks are constantly changing, morphing from simple fake invoices to sophisticated deepfake executive impersonations. It can feel overwhelming trying to keep up.
But here’s the good news: by understanding these different types of email threats and regularly practising with simulated attacks, your organisation can significantly lower its risk.
Contact Mitigata Today. We’re here to help you navigate this complex landscape.