What if your company is the target of the next cyber attack, but you simply cannot see it?
As per studies, 204 days is what companies take to detect a breach. This long time period allows attackers to steal data, plant backdoors, move across systems, and sometimes stay hidden for months.
Your company can rely on antivirus tools or firewall alerts, but threats often slip through. These tools stop known threats at the gate but do nothing about the attackers already inside your network.
That is where MDR gives your company a competitive edge. In 2025, we saw a 40% increase in MDR adoption compared to last year.
In this blog, we will explore managed detection and response (MDR) benefits, how it works and dive deep into a comparison of MDR with traditional tools.
Mitigata: India’s Only Full Stack Cyber Resilience Company
As India’s first and only full-stack cyber resilience company, we deliver end-to-end protection, detection, and response capabilities that go beyond standard solutions.
Companies choose us because they want reliability, cost efficiency, and 24/7 monitoring support backed by global expertise.
Here is what makes our MDR service stand out:
- Continuous 24/7 monitoring of IT and OT environments
- Advanced threat hunting by expert analysts
- Guided and remote response actions
- Access to experienced SOC analysts
- Seamless compatibility with third-party EPP tools
- Clean and easy-to-use MDR dashboards
- Global experts with a decade of experience
- Built-in endpoint protection
Real-Time Threat Response. Not Just Alerts.
800+ businesses trust Mitigata’s 24/7 MDR solutions for tailored threat detection and rapid incident response.

What Is MDR in Cybersecurity?
Managed Detection and Response (MDR) is an outsourced cybersecurity service that protects your organisation day and night by employing advanced technology and human intelligence together.
MDR keeps a watchful eye on your premises, makes inquiries regarding any questionable activity and takes instant measures to eliminate dangers.
Most teams choose MDR the wrong way, so this MDR selection guide uncovers the overlooked questions that truly shape your security.
What MDR Is NOT
To get a better understanding of Managed Detection and Response (MDR), it is useful to clarify what it is not.
Not Just Antivirus: Antivirus can stop the known malware, while the MDR system can even discover the advanced attacks that have passed through the old protection systems undetected.
Not only SIEM: Security Information and Event Management (SIEM) systems can gather security logs and correlate them, but their interpretation and taking proactive measures require expert analysts.
Not Limited to Vulnerability Scanning: Scanning only highlights the areas where security has to be improved.
How Does MDR Work?
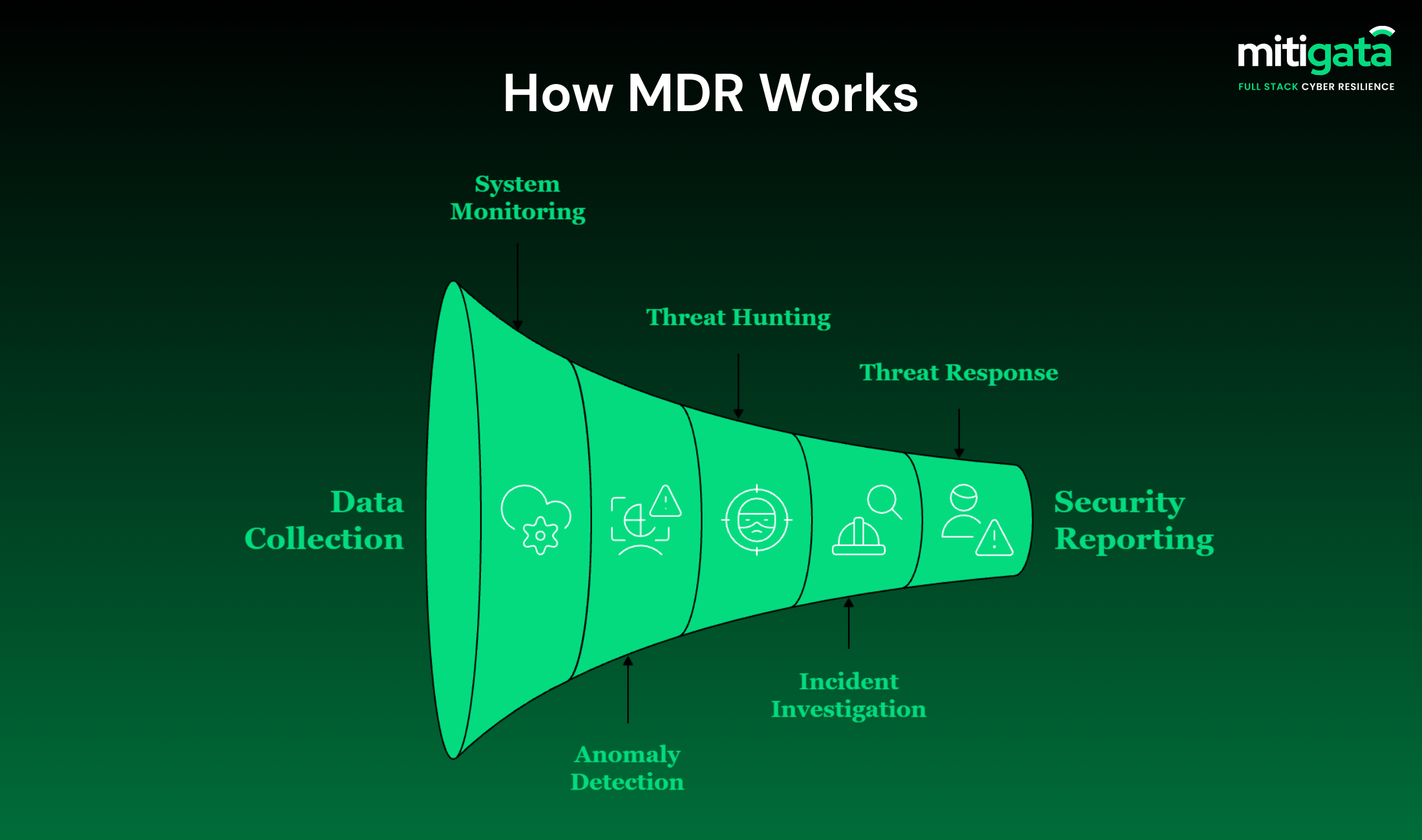
The MDR workflow is as follows:
Step 1: Deployment and Integration
The deployment of lightweight agents or sensors takes place first in various parts of your environment. They are responsible for gathering different types of data, such as user activities, network connections, file changes, process executions, and so on.
Your other security measures, like firewall logs, authentication systems, endpoint protection and cloud infrastructure, are also contributing data to the MDR platform.
Step 2: Continuous Monitoring and Data Collection
As soon as the MDR platform is operational, it commences the monitoring of user logins, file accesses, and network connections. This way, the system creates normal behaviour baselines for each user, device, and application in your environment.
Step 3: Automated Threat Detection
The system never ceases to apply machine learning algorithms and threat intelligence for the purpose of data analysis and detection of possible compromises.
When a threat is detected, an alert is generated. These alerts are then prioritised based on their severity, the affected assets, and the possible impact on the business.
Upgrade Your Defence With Mitigata’s Trusted MDR
Detect attacks sooner and respond smarter through continuous coverage built to protect your critical systems.

Step 4: Threat Hunting
Security specialists take the initiative to look for hidden threats that have not been identified by automatic detection tools.
This helps in identifying early-stage attacks like:
- Credential stuffing
- Privilege escalation
- Lateral movement
Step 5: Threat Containment and Response
Each second that passes allows the intruders to shift to other systems, gain higher authorities, or steal information. MDR takes prompt control measures like blocking the network, stopping processes, and removing credentials and threats.
Step 6: Remediation and Recovery
The whole process is recorded with a timeline, a list of actions taken, and suggestions for mitigating the impacts. After containing the immediate threat, the priority is to complete remediation and prevent recurrence.
If you’re unsure which security approach fits your stack, this guide explains the differences between EDR, XDR, and MDR.
Benefits of Managed Detection and Response (MDR)
Here are the key MDR benefits you need to know:
Faster Threat Detection and Lower Dwell Time
Attackers rely on long dwell times to stay unnoticed. MDR helps cut this window drastically.
With 24/7 monitoring, behaviour analytics, and threat intelligence, suspicious activity is flagged and analysed instantly.
Active Incident Response
Traditional tools only notify you. MDR goes further by providing guided or remote containment actions.
This includes:
- isolating compromised endpoints
- blocking malicious IP addresses
- Disabling suspicious user accounts
- stopping lateral movement
Access to Expert SOC Analysts
Building an internal team of threat hunters, incident responders, and SOC analysts is costly and time-consuming.
MDR gives you immediate access to specialists who:
- investigate alerts
- validate threats
- perform root cause analysis
- guide you through incident containment
Free Demo. Full Transparency. No Hidden Costs.
We provide personalised MDR solutions at unbeatable rates with zero compromise on coverage.

Proactive Threat Hunting
Proactive threat hunting is one of the top MDR benefits, in which analysts actively search for indicators of compromise using the latest threat intelligence and behavioural analysis.
Let’s say one of the threat hunters sees a user account that is accessing files it has never accessed in its history, during very strange times, but still within the permission limits set for him/her.
Such situations are when a human analyst comes in and helps eliminate the risks of advanced attacks that are not easily fought, like ransomware, insider threats and stealthy APT intrusions.
Scalable Protection for Growing Businesses
MDR scales seamlessly with your organisation. Adding new locations, cloud environments, or acquired companies to monitoring is a configuration change rather than a major project.
Better Visibility Across Your Entire Environment
MDR benefits users by providing centralised visibility across your entire infrastructure. Whether the threat originates in AWS, Azure, your corporate office, a remote worker’s home network, or your manufacturing floor, it’s detected and correlated with activity across your environment.
Reduced Alert Fatigue
Instead of drowning internal teams with hundreds of daily alerts, MDR filters, triages, and validates incidents. Teams only get notified when action is actually required.
Stronger Compliance and Reporting
MDR services inherently provide many controls required for compliance. Continuous monitoring, incident logging, response procedures, and comprehensive audit trails are built into the service. Many MDR providers offer compliance reporting specifically tailored to regulatory requirements, making audits significantly easier.
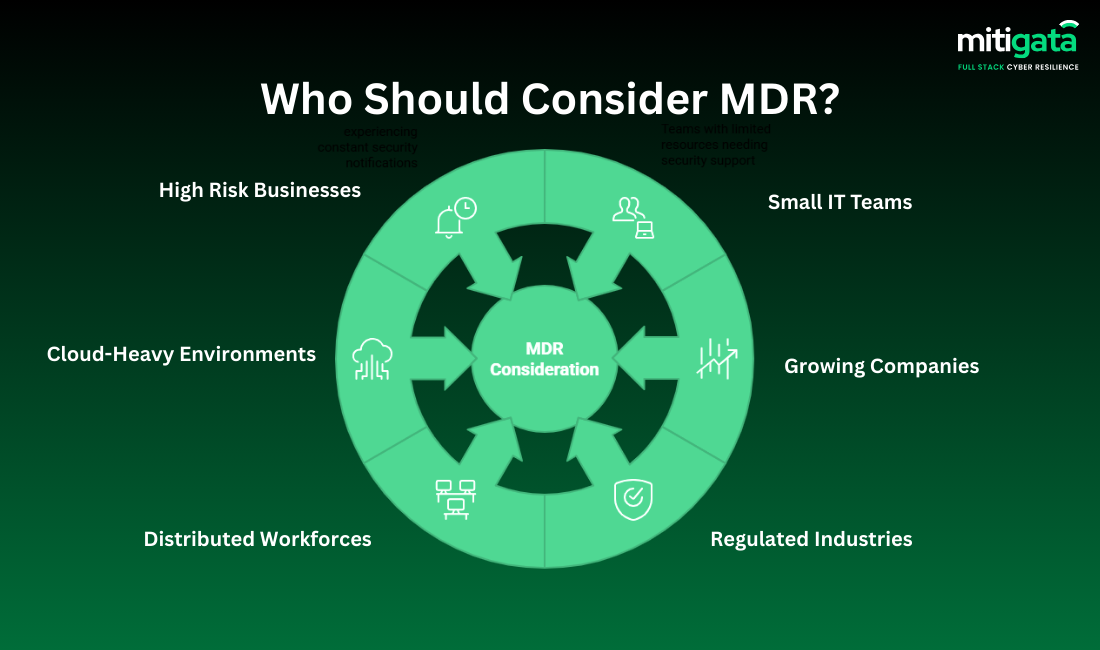
Who Should Consider MDR?
MDR is a smart investment for almost all companies, but certain situations make it particularly compelling:
- Small and Medium Businesses Without Security Teams
- Organisations With Remote or Distributed Workforces
- Businesses Facing Frequent Cybersecurity Alerts
- Companies Using Cloud Services
- Enterprises With OT + IT Infrastructure
- Businesses Preparing for Audits or Compliance Certifications
- Organisations in Highly Regulated Industries
MDR vs Traditional Security Tools: What Makes MDR Different?
Below is a detailed comparison table showing how MDR outperforms traditional tools across detection, visibility, response, and overall protection.
MDR vs Antivirus/Endpoint Protection
| Aspect | Traditional Antivirus | MDR |
|---|---|---|
| Detection Method | Signature-based, known malware | Behavioural analysis, anomaly detection, threat intelligence |
| Coverage | Endpoints only | Endpoints, network, cloud, applications |
| Response | Automated malware removal | Human-guided investigation and response |
| Threat Focus | Known malware | Sophisticated attacks, zero-days, insider threats |
| Human Expertise | None | 24/7 analyst team |
MDR vs SIEM (Security Information and Event Management)
| Aspect | SIEM Alone | MDR |
|---|---|---|
| Primary Function | Log aggregation and correlation | Active threat detection and response |
| Staffing Requirement | Requires dedicated security analysts | Analysts included in the service |
| Alert Management | Generates alerts for investigation | Investigate alerts and filter false positives |
| Actionability | Provides information | Takes action to contain threats |
| Cost Model | Major capital investment + ongoing operational costs | Subscription/operational expense |
Conclusion
By far, you must have a clear idea of MDR benefits. Managed Detection and Response marks the transition of cybersecurity from mere reactive defences to proactive, intelligent security operations.
The radical increase in adoption rate from 30% of companies in the year 2024 to 50-60% in 2025 indicates its significance for the entire industry.
Book your free 15-minute call with our experts today and see how Mitigata can change your security posture!.