By 2027, more than 25 billion stolen credentials will be in circulation on the dark web, fueling breaches that will already be affecting 43% of enterprises.
Most organisations learn about leaks only after it is too late, thereby escalating minor exposures into multi-million-dollar crises and regulatory penalties under the new Digital Personal Data Protection Act (DPDPA).
The following guide explains how dark web monitoring software works, providing you with the insights to detect threats early and proactively protect assets.
Why Businesses Choose Mitigata for Proactive Dark Web Monitoring Services
More than 800 organisations trust Mitigata to monitor threat activity beyond the surface web. With access to 500+ cyber products and deep experience across insurance, security, and compliance, Mitigata helps teams detect exposure early and respond with clarity when cyber incidents surface.
What Do We Track
Hacker Forums – Places where company names, executives, credentials, and weaknesses are discussed (e.g., XSS, BreachForums).
Criminal Marketplaces – Platforms used to sell stolen data, access credentials, and malware
Telegram Channels – Telegram has become a primary hub for ‘hacktivist’ groups targeting Indian infrastructure.
Breach Archives – Repositories where old and new data leaks continue to circulate
Exposed Assets – Publicly accessible GitHub repositories, cloud storage, and misconfigured services
Cybercriminals can’t hide when Mitigata monitors dark web threats
We deliver real-time detection, expert-led response, and market-best pricing.

What Is Dark Web Monitoring?
Dark web monitoring involves exploring hidden areas of the internet to detect and identify data associated with a company that has been compromised or stolen.
Dark web monitoring is your organisation’s early warning system, constantly scanning the internet’s hidden corners for compromised or stolen data linked to your business. To understand where this happens, think of the internet in three layers:
The surface web is everything Google can find – your company website, social media, public-facing content. It’s only about 4% of the entire internet.
The deep web contains password-protected systems: your email inbox, banking portals, and internal databases. Legitimate but private.
The dark web exists in a completely separate realm, accessible only through specialised browsers like Tor or I2P. This is where cybercriminals congregate in encrypted forums and illicit marketplaces to buy, sell, and trade stolen information.
Real-World Context: Consider the recent surge in ransomware attacks on Indian manufacturing firms. In many cases, initial access was purchased on the dark web weeks before the actual attack, using credentials stolen from a third-party vendor. Monitoring these marketplaces allows you to close the door before the thief walks in.
A practical guide on how to choose the best dark web monitoring software based on visibility, accuracy, and response speed.
Core Components of Dark Web Monitoring Tools
These are the core technologies used by dark web monitoring tools to detect data leaks and generate alerts ready for the security team.
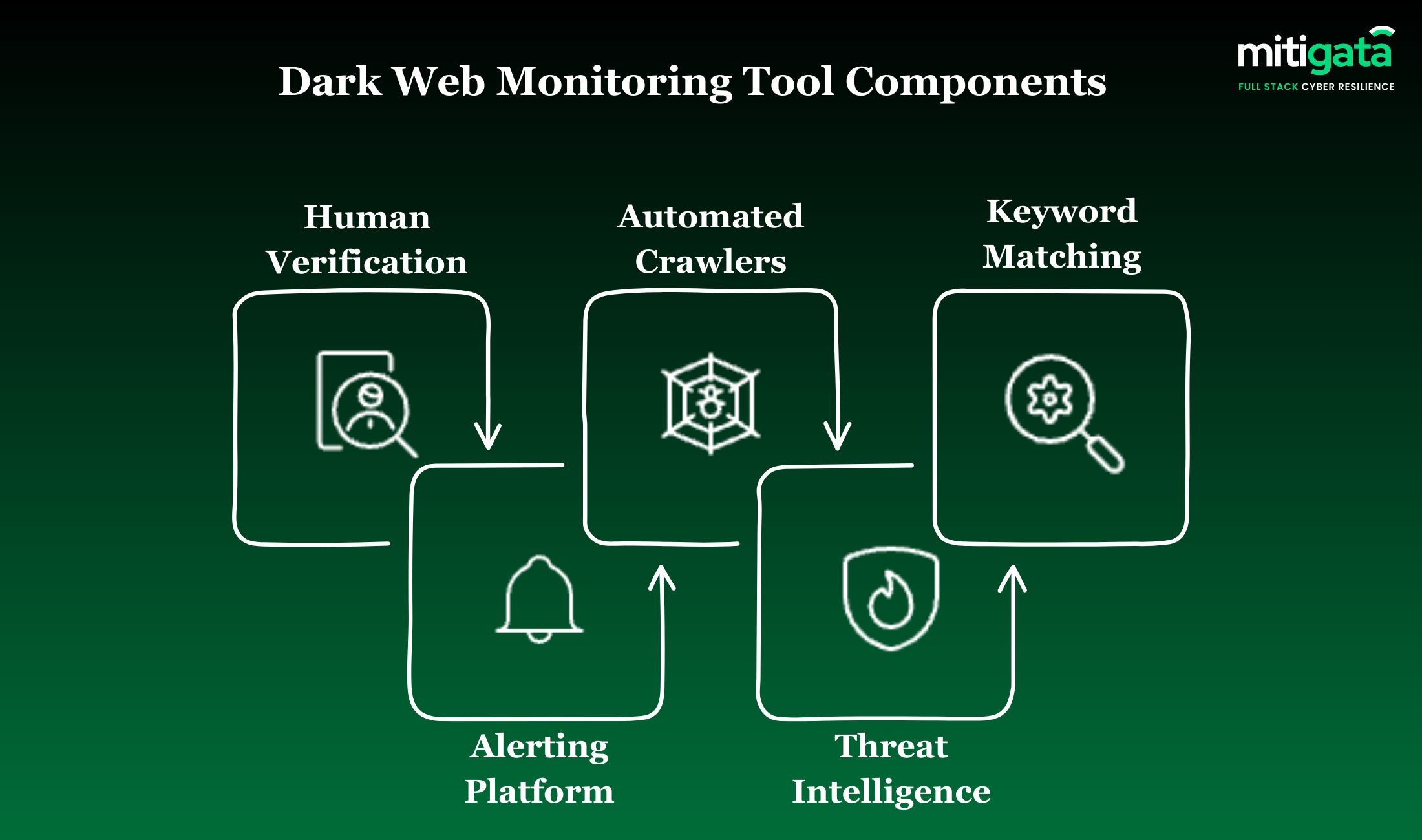
Automated Dark Web Crawlers
Dark web monitoring software relies on automated crawlers that operate through anonymous networks.
These hackers monitor forums, marketplaces, leak sites, and private channels where stolen data is either being traded or shared. Their focus is on live sources rather than leaked or outdated breach dumps that are no longer available.
Advanced crawlers can even penetrate ‘invite-only’ Telegram groups and Discord servers where fresh Indian credit card data (dumps) or KYC documents are often auctioned.
Keyword and Asset Matching Engine
A matching engine verifies the data gathered against the defined assets. This includes the company’s domains, employees’ email formats, brand names, and high-risk words. As a result, only data directly related to the business is retained in this process.
Threat Intelligence and Data Filtering
Data obtained from the dark web is usually raw and often contains duplicates or outdated breach materials.
The layers of threat intelligence that come with it will filter the data, identify the latest exposures, and reduce noise. This task will improve precision and reduce unnecessary alerts.
A practical guide on what to do if your data is exposed in a dark web data leak, from containment to recovery.
Human Verification and Context Analysis
Dark web monitoring services often include an analyst review as part of the process. The analyst’s job is to validate the findings, confirm the data’s relevance, and provide additional context, such as the actor’s intent or resale activity. This results in greater alert reliability and quicker decision-making support.
Alerting and Security Platform Integration
The alerts triggered by the validated findings are integrated with SIEM, SOC, or incident response tools.
The security teams are provided with clear information regarding what has been discovered, the place of its appearance, and how serious the exposure is, and the security operations are ready for immediate action.
Every leaked password or record can shut down your business
Trusted by 800+ businesses, our platform ensures continuous protection with advanced features for you and your data.

Step-by-Step: How Dark Web Monitoring Software Works
This section explains how dark web monitoring software tracks hidden sources through a transparent, sequential process.
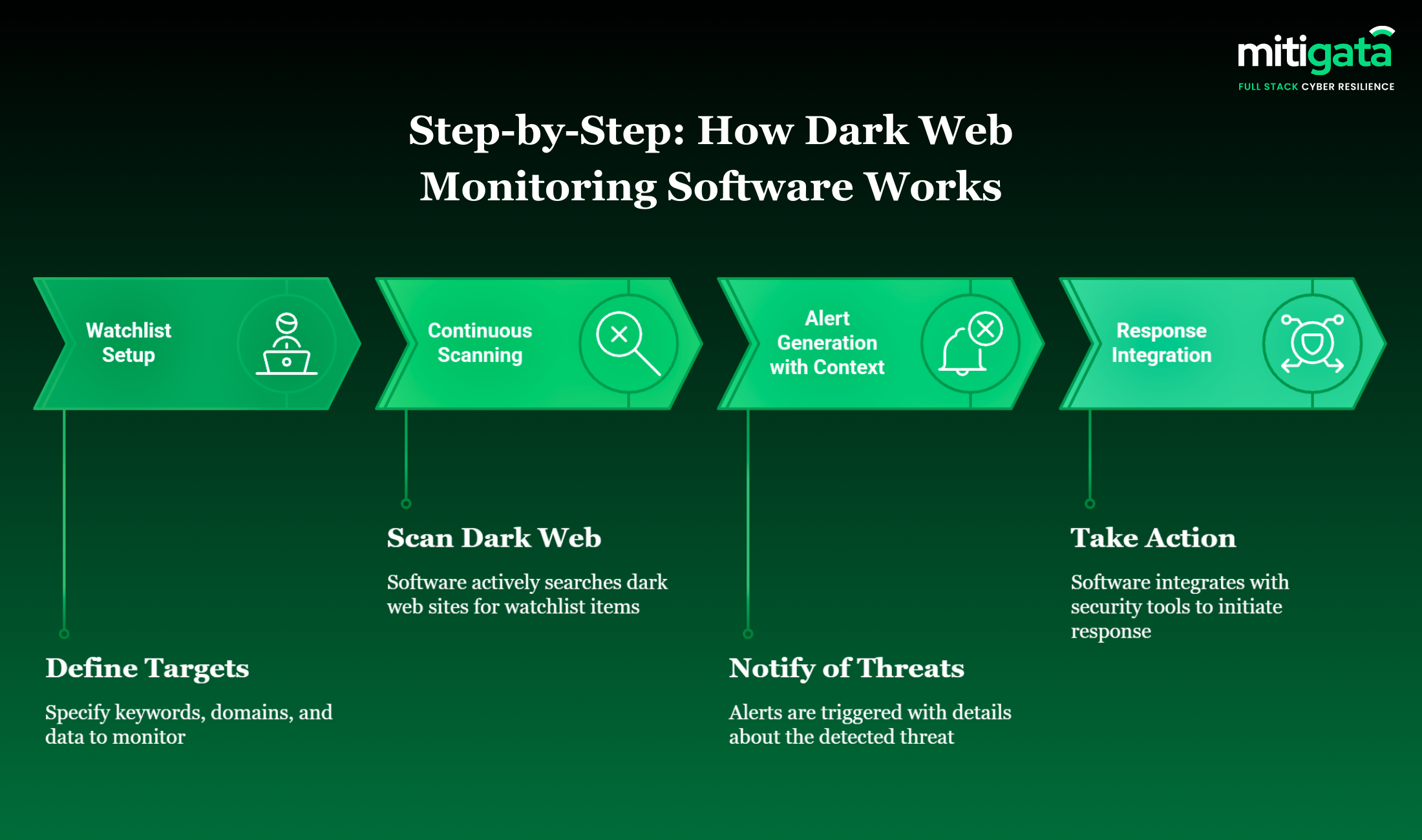
Watchlist Setup
The security teams first identify the critical assets to monitor, such as domains, employee email addresses, executive names, and sensitive keywords. This step is crucial because it helps to align monitoring activity with business risk.
Mitigata recommends including personal email addresses of C-suite executives, as these are frequently targeted for ‘whaling’ or phishing attacks to gain entry into corporate networks.
Continuous Scanning
The platform continuously scans all dark web sources via anonymous access. New posts, listings, and conversations are laundered against the watchlist. Unlike periodic audits, this is a 24/7 operation, ensuring that if your data appears on a marketplace at 3 AM IST, it is flagged immediately.
Learn how dark web data is traded, monitored, and used by attackers to exploit organisations.
Alert Generation with Context
If a match is found, alerts are sent with source details, data type, and risk level. The provided context enables teams to assess the situation’s urgency without conducting a manual investigation.
Response Integration
Alerts are integrated into the SIEM, SOC or incident response workflows. The teams can then reset credentials, inform the stakeholders and record the exposure in the GRC or VAPT processes.
This whole process makes dark web monitoring an active part of the cyber defence strategy rather than a mere reporting tool.
Under the DPDPA 2023, knowing about a breach and failing to act can lead to severe penalties. Automated integration ensures you have an audit trail of detection and response, which is vital for regulatory reporting.
Stay ahead of breaches with 99.7% detection accuracy
Mitigata reduces false positives, saving time and strengthening overall business security posture

Conclusion
Dark web monitoring software turns invisible threats into actionable intelligence. However, monitoring is only half the battle.
To ensure complete resilience, combine this visibility with comprehensive cyber insurance to cover financial liabilities if a breach does occur.
Contact Mitigata for a free demo and proactive monitoring that keeps threats in check.

