In 2025, more than 15 billion stolen credentials flooded the dark web, a 34% surge compared with prior years. For Indian businesses and individuals, this statistic is alarming, especially considering that India remains one of the top five most targeted nations globally for cyberattacks.
While data breaches spiked by 43%, exposing emails, passwords, and financial information, this surge is directly increasing the risk of identity theft and ransomware attacks.
According to recent industry reports, the average cost of a data breach in India has reached an all-time high of approximately ₹22 Crore, severely affecting many Small and Medium-sized Enterprises (SMEs).
With daily dark web traffic hitting 3 million visitors and 60% of sites trading illegal data, your personal information could already be up for auction, contributing to $12.5 billion in U.S. cybercrime losses.
Mitigata – A Cybersecurity Partner You Can Rely On
Mitigata operates in the digital underground to keep your business protected. With access to 500+ cyber tools and strong expertise across insurance, security, and compliance, we help organisations identify, assess, and stop threats before they escalate into serious incidents.
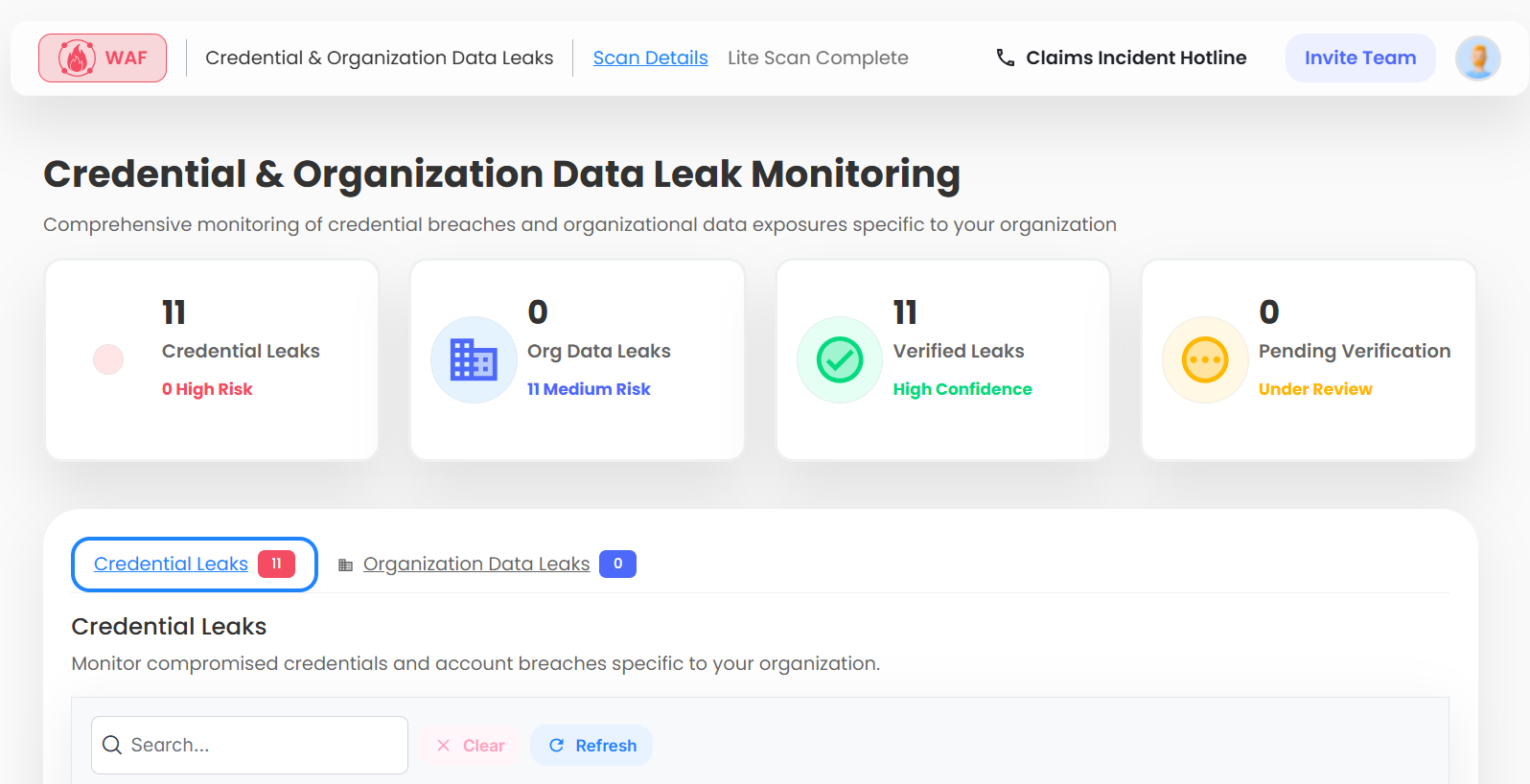
What do we monitor?
- Hacker forums
- Criminal marketplaces
- Telegram channels
- Breach databases
- Exposed digital assets
Mitigata goes beyond alerts. We convert raw threat signals into clear, actionable intelligence.
When a risk is identified, we reveal the source, determine what is exposed, and assess the potential business impact, so you can respond with confidence.
Cybercriminals can’t hide when Mitigata monitors dark web threats
Mitigata delivers real-time detection, expert-led response, and market-best pricing.

What Is the Dark Web and Why Does Your Data End Up There
The dark web is a hidden part of the internet accessible only with specialised software such as The Onion Router (Tor). Think of the internet as an iceberg: the ‘Surface Web’ (Google, Amazon) is the visible tip, while the ‘Dark Web’ is the massive, submerged mass beneath, untraceable and anonymous.
It is a cyberspace for criminals who sell data harvested from breaches, phishing attacks, malware infections, and unsecured cloud systems.
After a vendor, app, or service provider’s security is breached, their
- Email addresses
- Login credentials
- Customer databases
- Credit card details
- Employee records
….are posted on dark web forums. For example, in a recent incident involving a major Indian payment gateway, millions of merchant records were allegedly put up for sale for as little as $500 in cryptocurrency.
The data is often resold multiple times once it is placed on the market.
Discover why your leaked data never truly disappears from the dark web and how you can minimise its impact.
Signs Your Information Is on the Dark Web
Unusual account activity is often a sign that your information has been compromised. Be vigilant for the following indicators:
- Password reset emails you didn’t request
- Blocked login attempts from unfamiliar locations (e.g., a login attempt from Russia or China when you are based in Mumbai).
- Unexplained bank transactions or small ‘test’ charges of ₹1 or ₹10.
- Alerts from breach-notification tools
- Sudden increase in phishing emails
- Increase in fake support calls (indicates your contact details are on dark web markets)
7 Proven Steps to Protect Your Data From the Dark Web
Here are a few steps you can follow to protect yourself from a dark web data leak.
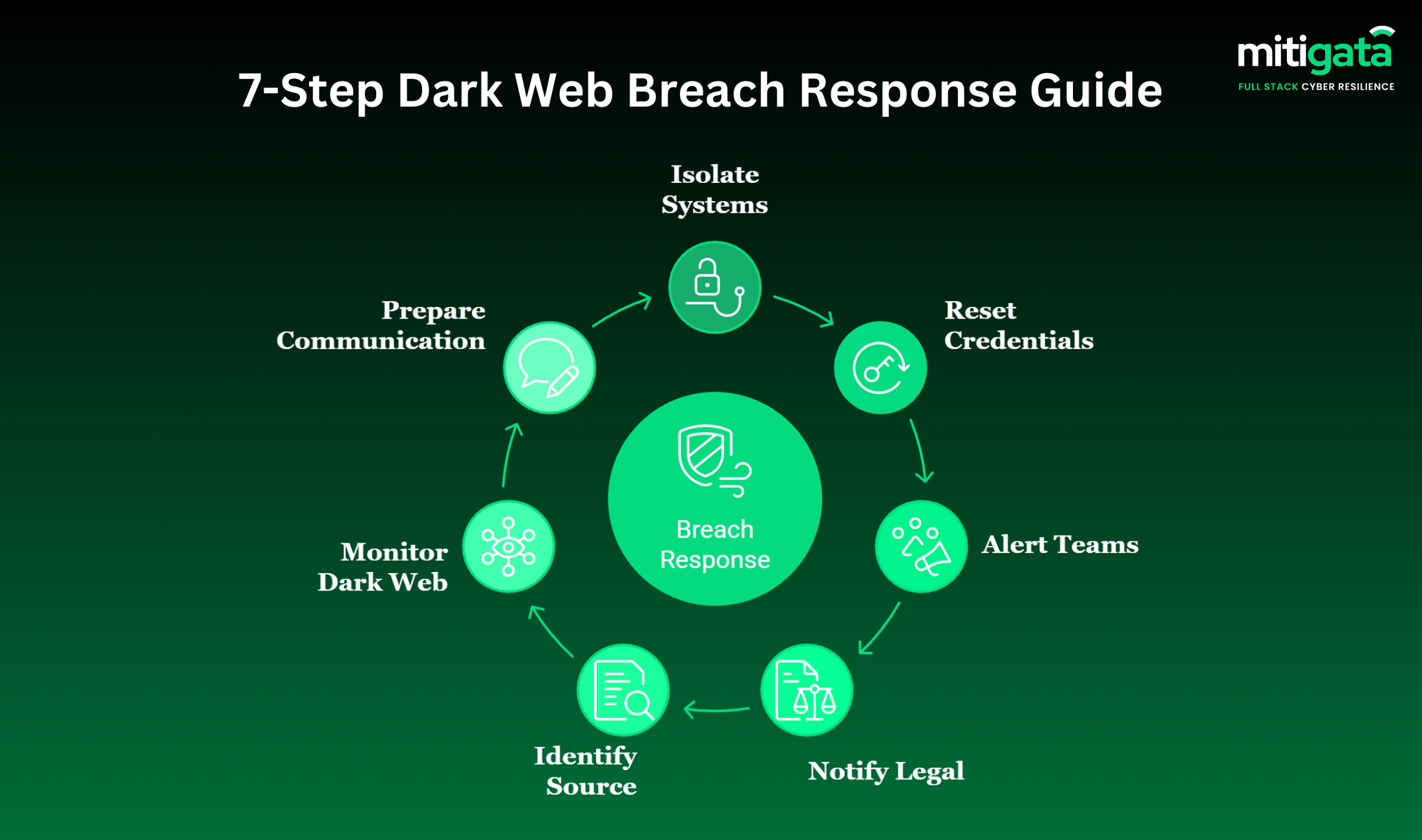
Use Strong, Unique Passwords for Every Account
Using the same password across multiple accounts, a hacker can gain access to all services with a single breach (a technique known as ‘Credential Stuffing’). Long, unique passwords would significantly reduce this risk.
Example: Instead of using ‘Summer2025’ for multiple accounts, use a password manager to generate ‘V7h$9Lp2@qR!’ for your email and a completely different one like ‘Dk8#uF5!xZb’, for your bank.
Every leaked password or record can shut down your business
Trusted by 800+ businesses, our platform ensures continuous protection with advanced features for you and your data.

Activate Multi-Factor Authentication (MFA)
MFA prevents unauthorised access even when login credentials are found on the dark web by requiring an additional verification step.
Example: Enable Google Authenticator or SMS-based codes for your email and banking accounts. Even if a password is leaked, a hacker cannot log in without the second code.
Pro Tip: Avoid SMS 2FA if possible due to ‘SIM Swapping’ fraud; use an authenticator app instead.
Monitor the Dark Web for Exposed Data
Dark web monitoring tools scan hidden sources for leaked emails, credentials, and business domains and alert when a match is found.
Learn what to look for when selecting the right dark web monitoring software to protect your organisation from hidden threats.
Reduce Public Data Exposure
Get rid of personal information on data broker sites and control what gets shared on public profiles, forums, and sign-up forms.
Example: Avoid sharing work emails or personal info on forums and free Wi-Fi registration forms at airports or cafes. Hackers often set up ‘Evil Twin’ Wi-Fi hotspots to harvest this data.
Secure Devices and Networks
The risk of gaining access to credentials via malware is reduced by keeping systems up to date, using trusted security software, and practising safe Wi-Fi practices.
Example: Keep your laptop and phone updated with the latest OS patches. Use VPNs when connecting to public Wi-Fi to prevent credential theft by attackers on the network. Ensure your office firewall is configured to block traffic from known malicious IP addresses.
React Promptly to a Breach Alert
Once an alert regarding exposure has been issued, change the passwords that were affected.
Check the activity on your account and secure the services linked to it without delay.
Example: If you receive a breach notification that your email password was leaked, immediately change your password, enable MFA, and check linked accounts for suspicious activity. Report significant financial breaches to the National Cyber Crime Reporting Portal (cybercrime.gov.in).
Learn how to check whether your email has been exposed on the dark web and what steps to take if it has.
Hire Data Protection Services & Get Cyber Insurance
The professionals come to your rescue with constant supervision, breach handling, and eliminating the information that was leaked from the illegal listings. Furthermore, invest in a comprehensive Cyber Insurance policy, which will serve as your fire brigade against cyber attacks.
Mitigata’s cyber insurance policy can cover financial losses, legal fees, and regulatory fines if your data is compromised.
Stay ahead of breaches with 99.7% detection accuracy
Mitigata reduces false positives, saving time and strengthening overall business security posture

Conclusion
Protecting your data against the dark web requires constant surveillance in an environment where breaches occur daily.
Regularly monitoring the dark web, using multi-factor authentication, and monitoring your credentials are best practices that help protect you from data compromise.
Ready to safeguard your business?
Contact Mitigata today to secure your data from the dark web and explore our tailored cyber insurance plans.

