In 2025, over 90% of enterprises rely on cloud and SaaS platforms, while nearly 70% of breaches are linked to unknown, unmanaged, or misconfigured assets.
Taking advantage of this, attackers are now targeting these blind spots, exploiting shadow IT, forgotten domains, and exposed services.
This is where Attack Surface Management (ASM) steps in, it helps reduce breaches by eliminating blind spots and stopping attackers before exploitation begins.
In this blog, we cover the key benefits and best practices of Attack Surface Management to help organisations stay secure in an expanding threat landscape.
Why Choose Mitigata for Attack Surface Monitoring
Trusted by over 800 businesses across 25+ industries, Mitigata helps organisations secure their external digital footprint with confidence. Backed by a 99.7% threat detection rate, our expertise enables companies to identify and reduce exposure early, staying ahead of evolving cyber risks.
Here’s what we continuously monitor for you:
Web Assets (Domains & Subdomains): Spot expired, exposed, or forgotten domains before they can be exploited.
Cloud Infrastructure & IPs: Scan for misconfigurations, open ports, and outdated systems that attackers often target.
Mobile Apps & APIs: Watch for insecure endpoints, hidden flaws, and API abuse that may lead to data exposure.
Email Systems: Review SPF, DKIM, and DMARC settings to reduce the risk of spoofing and phishing.
Social Engineering Threats: Detect impersonation attempts, lookalike domains, and phishing campaigns targeting employees or customers.
Stay ahead of breaches with 99.7% detection accuracy
Our experts provide 24/7 monitoring and rapid response to protect every asset in your digital environment.

What Is Attack Surface Management?
Attack Surface Management (ASM) is the practice of identifying and monitoring all digital assets that attackers could target.
An attack surface comprises everything that is connected to the internet or the internal network.
These include websites, domains, IP addresses, cloud systems, APIs, software-as-a-service (SaaS) tools, endpoints, and third-party services.
Many of these assets are easy targets for cybercriminals.
Attack surface management tools automatically discover these assets, track changes, and report risky exposures so teams can rectify issues before attackers exploit them.
Understand how Attack Surface management helps you find and reduce hidden security risks.
Key Features of Attack Surface Management
These key factors promote proper visibility, monitoring, and management of the entire cybersecurity surface.
Asset Discovery
ASM begins with complete asset identification across all operational environments. Automated scanning reveals both authorised infrastructure and overlooked resources.
| Environment | Discovery Scope | Critical Findings |
|---|---|---|
| Internal | Endpoints, applications, network resources | Unauthorised tools, unmanaged devices |
| External | Domains, IPs, public services, APIs | Exposed test systems, forgotten subdomains |
| Cloud | SaaS applications, containers, storage | Misconfigured permissions, orphaned instances |
Internal Attack Surface Management
Internal management addresses risks from employee endpoints, applications, and access privileges. Security teams gain visibility into how internal systems and permissions contribute to overall exposure.
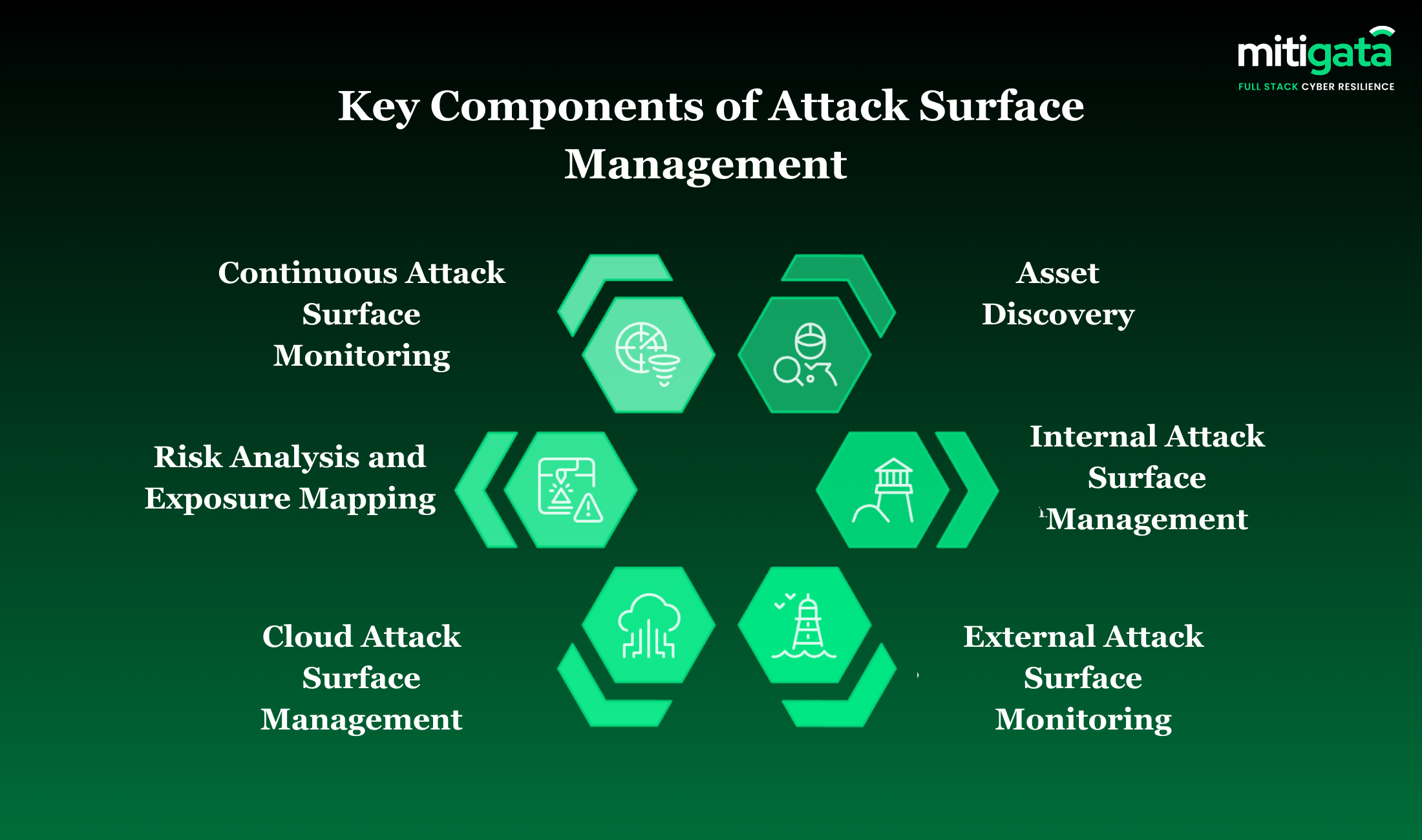
External Attack Surface Monitoring
External monitoring tracks all internet-facing assets, such as the primary targets for adversary reconnaissance. Continuous observation identifies misconfigurations, unintentional exposures, and vulnerable services before they can be exploited.
Looking for an MDR provider? Here’s a closer look at the 5 best MDR companies and what sets each apart.
Cloud Attack Surface Management
Cloud ASM tracks constantly shifting workloads, storage configurations, and SaaS integrations across multi-cloud deployments, addressing the unique security challenges these platforms present.
Take Control of Your Digital Security Today
From continuous asset discovery to actionable insights, we help you minimise risk and strengthen your security posture.

Risk Analysis and Exposure Mapping
Risk analysis assesses the asset’s exposure, including accessibility, configuration issues, and security vulnerabilities.
Risk Assessment Framework:
| Assessment Factor | Evaluation Criteria | Impact on Priority |
|---|---|---|
| Accessibility | Internet-facing vs. internal | High exposure increases priority |
| Vulnerabilities | Known CVEs, patch status | Critical vulnerabilities demand immediate attention |
| Configuration | Security controls, hardening | Misconfigurations elevate risk |
| Business Value | System criticality, data sensitivity | High-value targets require enhanced protection |
Continuous Attack Surface Monitoring
Continuous attack-surface monitoring is the process of observing asset evolution over time rather than relying on periodic scans.
What should attack surface monitoring really include? This breakdown highlights the features most teams miss.
Best Practices for Attack Surface Management
The following are the best practices that organisations use to minimise their exposure in a straightforward way.
Maintain Real-Time Asset Inventory
Every new system expands your attack surface. Real-time inventory prevents forgotten assets from becoming entry points.
What to track: Systems, applications, cloud services & web tools
Monitor Internet-Facing Assets Continuously
Anything online can be targeted. Continuous monitoring catches exposures before attackers do.
Continuous monitoring helps detect
- Newly exposed services
- Misconfigurations
- Unused or forgotten domains
Track Environmental Changes
Change tracking allows teams to
- Spot new exposure after updates or deployments
- Compare the current risk against previous scans
- Avoid relying on outdated security data
Include Cloud & SaaS Assets
Cloud platforms change rapidly and often bypass traditional IT controls.
Make sure they:
- Reduce blind spots from shared responsibility models
- Gain visibility into decentralised services
- Ensure consistent security coverage
See Every Vulnerability Before Attackers Do
Mitigata offers a free demo of the ASM platform so that you can discover hidden vulnerabilities before attackers do.

Prioritise Assets Based on Exposure Risk
Certain assets are considered internal and therefore low-risk, while others are exposed or connected to sensitive data.
If teams examine asset access methods and configurations, they can focus remediation efforts on higher-risk areas, preventing uneven attention across all systems.
Use Tools That Match Organisational Scale
Simple discovery and monitoring are sufficient for smaller environments, while larger ones require automation and broader visibility.
Connect Findings With Security Response
The discovery and monitoring processes alone cannot reduce risk unless the implementation follows them.
By connecting attack-surface results with remediation and response workflows, security teams can close exposure more quickly and maintain consistency in daily security operations.
Review Exposure Trends Regularly
Risk changes as your environment evolves. Regular reviews reveal recurring issues, improve configurations, and support long-term security visibility.
With so many PIM tools on the market, knowing what actually works matters. This guide breaks down the best options and why they stand out.
Conclusion
Effective Attack Surface Management enables businesses to reduce their attack surface in an era of constant threats by requiring ongoing attention to everything.
Organisations can enhance resilience and compliance and reduce breach risk in 2026 by implementing these measures.
Contact Mitigata today to explore tailored Attack Surface Management solutions and secure your digital perimeter.

