What would it cost your business if the next cyberattack hit you, not tomorrow, but in the next 39 seconds?
With the average data breach costing companies $4.45 million and cyberattacks occurring every 39 seconds somewhere in the world, organisations can no longer rely on basic security controls alone.
Since criminals rely on stolen passwords, ransomware, and supply-chain vulnerabilities, businesses have moved beyond basic security controls.
They are now implementing red team, blue team, and purple team tactics in cybersecurity to assess strengths and weaknesses and close security gaps.
This blog discusses the definitions of red, blue, and purple teaming, their key benefits, and common challenges.
Why Businesses Choose Mitigata for Cyber Defence
Mitigata is India’s leading cyber resilience company, trusted by 800+ businesses across 25+ industries, offering end-to-end Red, Blue and Purple teaming services that simulate real attacker behaviour across systems, users, and processes.
What our teaming services offers:
- Real-world attack simulations that reveal real risks across systems, users, and processes.
- Practical testing of employee readiness against social engineering attacks.
- Clear, actionable insights with prioritised improvement steps.
- Trusted by companies across BFSI, Aviation, Retail, and Manufacturing
- Red, Blue, and Purple Teaming delivered under one unified framework
- Market-best pricing with enterprise-grade security outcomes
- 24/7 expert support from experienced security professionals
How Strong Is Your Security When No One’s Watching?
Test it with Mitigata’s red, blue, and purple teaming, trusted by 800+ global clients.

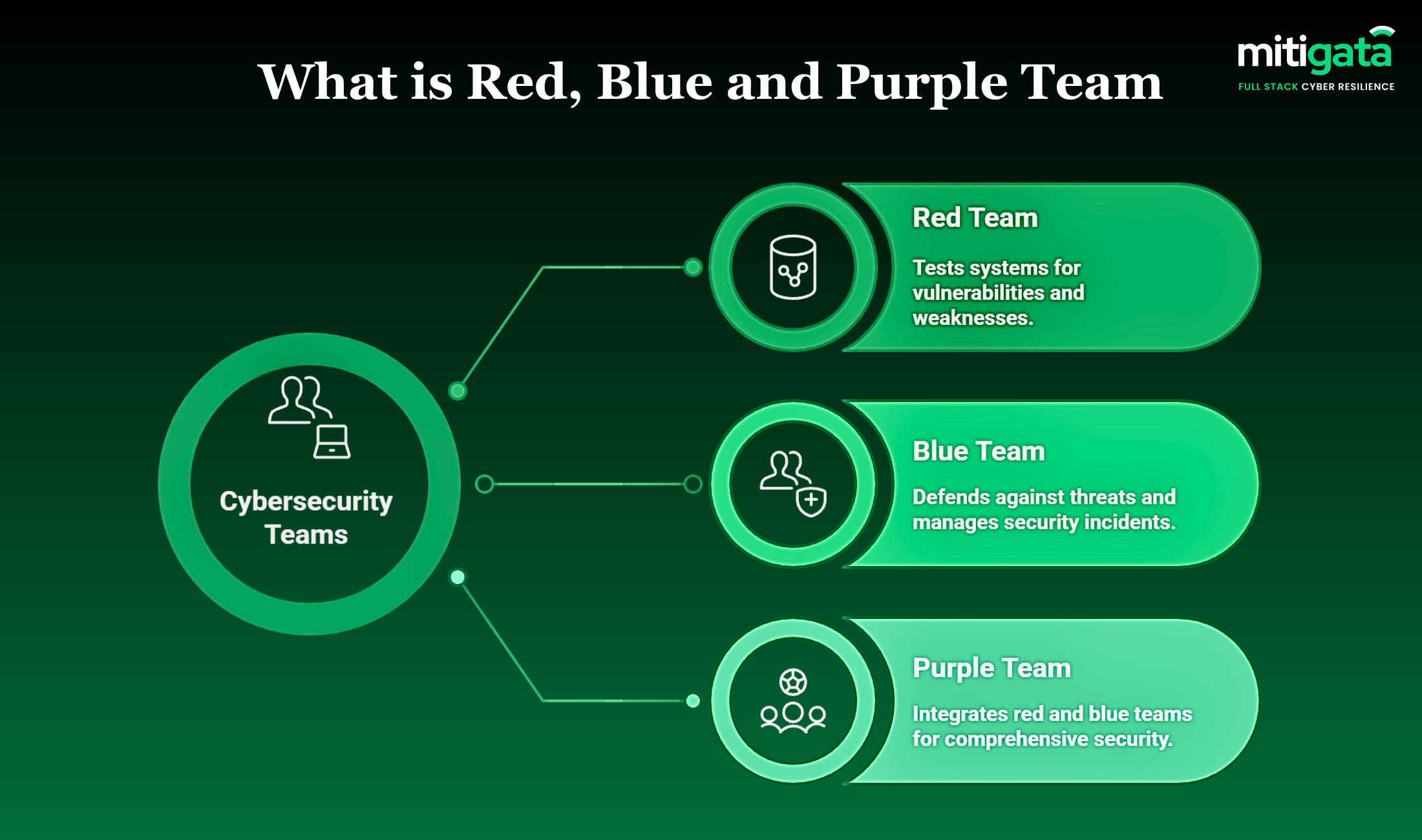
What Is a Red Team in Cybersecurity?
A red team in cybersecurity does not limit itself to finding only technical weaknesses; it also tests the human factor and the processes and controls in place.
For instance, testers may send a phishing email that appears to be a standard HR update during a red team computer security exercise.
The red team cybersecurity exercise proceeds by using an employee’s credentials to gain deeper access to the network if the employee clicks the link. The company then discovers how a single error might result in a complete breach.
This approach helps leadership answer a direct question: If an attacker targeted us today, how far could they go before anyone noticed?
Understand the difference between vulnerability assessment and penetration testing to choose the right security approach for your business.
What Is a Blue Team in Cybersecurity?
A blue team in cybersecurity focuses on defence, detection, and response. This team is responsible for monitoring systems, investigating alerts and incidents, and taking actions to mitigate them.
The blue team’s security tasks occur daily and are primarily managed through a security operations centre.
For example, if unusual login activity is detected from a foreign country.
The blue team’s information security department will analyse the logs, monitor device activity, and decide whether to terminate access. The quicker the response, the lesser the impact.
Why Pay More for Security That’s Never Tested?
Choose red, blue, and purple teaming, designed for results, at affordable prices.

What Is a Purple Team in Cybersecurity?
Purple teaming in cybersecurity is about cooperation. Instead of keeping the red and blue teams apart during testing, a purple team in cybersecurity brings them together.
A red team demonstrates an attack method, such as credential dumping, during purple teaming exercises.
The blue team monitors activities in real time, modifies detection criteria, and verifies that warnings are triggered appropriately.
Defences strengthen more quickly as the lesson becomes instantaneous. The Purple Team in cybersecurity eliminates blame and emphasises progress.
Can your team detect and respond to attacks 24/7? Learn how MDR strengthens security, reduces alert fatigue, and limits breach impact.
Red Team vs Blue Team vs Purple Team Comparison (2026)
The table below highlights the differences between the red team, blue team, and purple team in cybersecurity, using common security goals.
| Focus Area | Red Team | Blue Team | Purple Team |
|---|---|---|---|
| What It Does | Simulates real attacks | Defends and responds | Improves both together |
| Key Question Answered | How could we be breached? | How fast can we respond? | Are we improving security? |
| Risk It Reduces | Unknown exposure | Prolonged incidents | Repeated failures |
| Business Value | Reveals true impact | Limits downtime | Maximises security ROI |
| When to Use | Before major growth, audits, or acquisitions | When operational resilience is critical | When scaling or optimising security |
| Frequency | Periodic or milestone-based | Ongoing | Continuous or program-based |
Discover the key factors to consider when choosing a SOC monitoring tool that fits your security and compliance needs.
Conclusion
The red team, blue team, and purple team cybersecurity models illustrate how these defence systems operate.
Attackers continuously test systems. The same discipline must be used by defenders to test themselves.
In simple terms, red teams demonstrate the effectiveness of attacks. Blue teams minimise damage while purple teams transform every test into progress.
Ready for a real security improvement? Contact Mitigata today to strengthen your cyber resilience where it matters most.

