What if one missing security control could cost you your customers and investors?
In 2024–2025, 60% of companies openly stated they favour SOC 2-compliant startups over those without certification. As per recent surveys, 70% of venture capitalists now prioritise SOC 2 compliance when making investment decisions.
SOC 2 compliance requirements have become a trust filter. If you want enterprise deals, you need to prove that your systems are safe before anyone gives you access to their data.
In this blog, you will learn everything you need to understand SOC 2 Compliance requirements, key controls, certification expectations, the audit process, and the tools that help you accelerate your journey.
How Mitigata Helps You Meet SOC 2 Compliance Requirements Faster
More than 500 businesses across 25 sectors trust us. We are certified to ISO 27001, HIPAA, GDPR, and SOC 2 Type II, so we hold ourselves to the same standards we help you meet.
Most platforms focus on automation alone. Automation helps, but SOC 2 compliance requiremnts requires context and judgment. That is where Mitigata stands out:
- Faster implementation with a guided SOC 2 readiness workflow.
- Human support combined with automation so you never feel stuck.
- Clear audit preparation, not scattered spreadsheets and checklists.
- A complete GRC automation tool that reduces documentation work, evidence collection, and control monitoring.
- Better auditor alignment because we work with top CPA firms that understand modern tech stacks.
- Transparent controls mapping so you know precisely what each SOC 2 Compliance Requirements means for your company.
See All Your Risks Clearly on a Single Dashboard

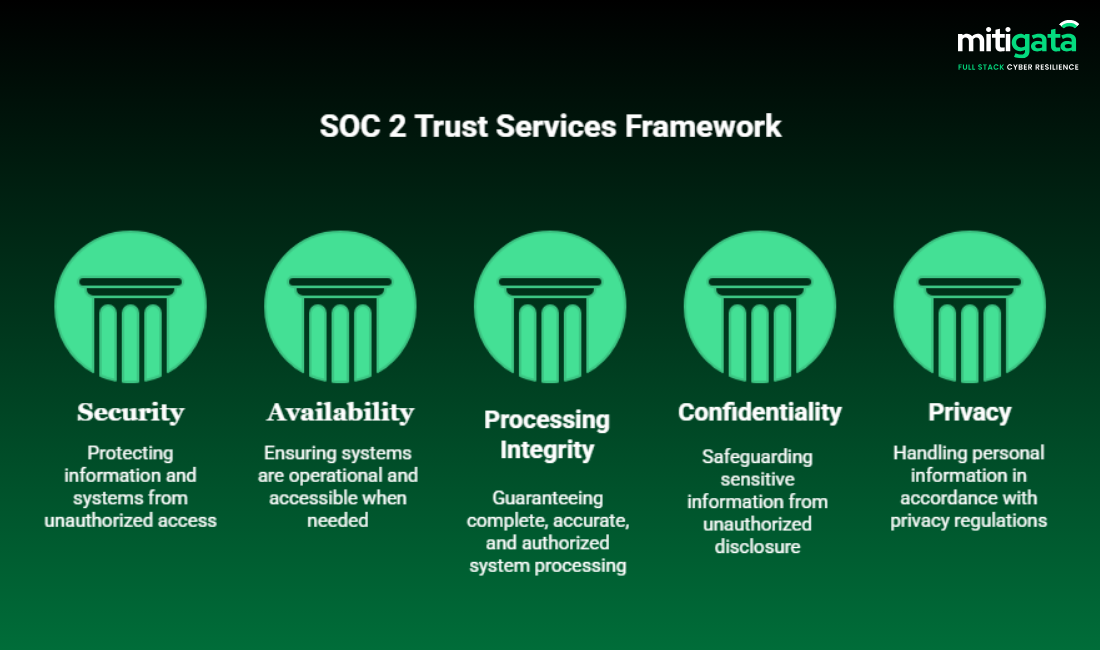
What Is SOC 2 Compliance?
SOC 2 (System and Organisation Controls 2) is an auditing standard developed by the American Institute of Certified Public Accountants (AICPA). It evaluates whether a company’s controls protect customer data based on these 5 Trust Services Criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 proves to customers, investors, and partners that your internal controls and systems work consistently. Think of it as a stamp of trust that shows you take security seriously.
Who Needs SOC 2 Compliance?
- If you handle customer data, you probably need it. This includes:
- SaaS companies storing client information
- Cloud service providers hosting applications or data
- Financial technology platforms processing transactions
- Healthcare technology companies (often alongside HIPAA)
- HR and payroll software providers
- Marketing technology platforms with customer data access
See why healthcare data breaches are exploding and which risks your organisation may be overlooking right now.
SOC 2 Compliance Requirements: What Every Company Must Meet
Below is a streamlined breakdown of the core SOC 2 compliance requirements every company must meet.
- Clear Scope and Documented Policies
SOC 2 starts with defining what parts of your environment are included in the audit and documenting the rules your team follows.
This includes:
- Systems, apps, and data flows in scope
- Where customer data is stored and who can access it
- Written policies like access control, incident response, change management, and security guidelines
- Backup, continuity, and recovery documentation
Most companies confuse digital forensics and incident response, but the difference can make or break recovery. Do you know what your business needs first?
- Risk Assessment and Security Training
SOC 2 compliance requirements require proof that you manage risk proactively and train your team to follow secure practices.
You need:
- Regular documented risk assessments
- Identified threats, impact analysis, and mitigation steps
- Onboarding training for new employees
- Annual refresher training for all staff
- Records showing everyone completed the required training
- Vendor and Third-Party Management
If vendors handle customer data, you must show auditors that you evaluate and monitor them.
This includes:
- A vendor inventory
- Due diligence reviews
- Contracts with security requirements
- Periodic reviews or collecting vendor SOC 2 reports
From Policy to Proof, Manage Everything in One Place

- Access Control and Change Management
Access and system changes must be controlled, verified, and logged.
You need:
- Unique user accounts and role-based access
- Multi-factor authentication on critical systems
- Regular access reviews and removals
- Documented change requests with testing and approvals
- Rollback plans for risky deployments
Struggling with access chaos? See the IAM tools security teams are switching to this year.
- Monitoring, Logging, and Incident Response
Auditors expect to see active monitoring and the ability to handle incidents quickly.
You must have:
- Centralised logging for critical systems
- Monitoring tools that alert on suspicious activity
- Regular log reviews
- A documented incident response plan with roles, communication steps, and post-incident reviews
- Business Continuity and Disaster Recovery
SOC 2 auditors want to see that your operations can withstand a failure or incident without chaos.
This requires:
- Backup systems are tested regularly
- Documented recovery steps
- Defined recovery time objectives (RTO) and recovery point objectives (RPO)
- Annual continuity and recovery testing

Understanding SOC 2 Controls and How They Support Compliance
Controls are the actual mechanisms you implement to meet SOC 2 Compliance requirements. Suppose you have a requirement to “ensure only authorised personnel can access production systems.”
| Control Type | Specific Control | How It Works |
|---|---|---|
| Administrative | Access control policy | Defines who can request access, the approval process, review frequency |
| Administrative | Quarterly access reviews | Manager reviews team access every 90 days, removes unnecessary permissions |
| Technical | Single sign-on (SSO) with MFA | Users authenticate through a centralised system with a second factor |
| Technical | Role-based access control | System enforces access based on job function, not individual permissions |
| Technical | Access logging | All access attempts logged and monitored for anomalies |
| Technical | Automatic deprovisioning | Access removed within 24 hours when the employee leaves |
Below is a comprehensive SOC 2 controls list categorised under the respective trust services criteria:
Security (Mandatory):
Access Controls: issuance of unique user IDs, multi-factor authentication, access based on roles, quarterly reviews, immediate termination and removal of access, password requirements, and session timeouts
Network Security: protection through firewalls, segmentation of the network, detection of intrusion, VPN for remote access, vulnerability scans, wireless security
Data Protection: applying encryption while data is at rest and while it is being transferred; secure disposal, monitoring of databases and prevention of data loss
System Operations: malware protection, automatic updates, managing changes, splitting environments, testing backups, and logging at a central point.
Physical Security: restricting access to the building, management of visitors, monitoring through cameras, controls over environmental factors, and securing the computers.
Looking for real automation, not noise? Discover the best GRC tools actually delivering results today.
Availability:
System monitoring: ensuring that the system is operational, tracking performance, planning for capacity, and establishing explicit service level targets.
Incident management: a plan for responding to incidents based on their severity, including an on-call rotation, escalation protocols, and post-incident reviews.
Business continuity: an emergency recovery strategy, periodic backup testing, replacement components, switching procedures, and yearly testing.
Processing Integrity:
Data Processing Controls: the validation of input, logging of processing, reconciliation of accounts, checking of data integrity, and handling of errors.
Quality Assurance: the procedures of testing, the reviewing of code, the testing of users’ acceptance, and the procedures of rollback.
Data classification: classification policy, confidential data inventory, handling requirements, and data labelling.
Information protection: NDAs for employees, transmission controls, secure collaboration tools, retention and disposal procedures.
Privacy:
Privacy management: developing a privacy policy, managing consent, implementing data subject rights procedures, and conducting privacy effect assessments.
Data handling: purpose limitation, data minimisation, retention schedules, third-party sharing limits, and cross-border transfer precautions.
Privacy accountability: a designated data privacy officer, privacy training, breach notification protocols, and regular audits.
Ready to simplify compliance and Cut Manual Work?

SOC 2 Certification Requirements: What Auditors Expect
Auditors execute a quite formalised outline. Their investigation is focused on finding evidence that your controls are effective and that your policies are, in fact, observed.
The following SOC 2 Compliance Requirements is what they will be looking for:
System Description: Comprehensive description of your system, including infrastructure, software, people, procedures, and data
Control Matrix: A document linking the controls to the SOC 2 criteria
Policy Documentation: All policies up to date and in their complete versions
Organisational Chart: Overview of the reporting structure and the assigned security duties
Vendor List: An exhaustive list of third-party service providers
Pro tip:
Mitigata’s GRC automation tool organises all evidence into auditor-friendly packages. This reduces review time dramatically.
Why are cyber insurance approvals getting tougher? Discover the application pitfalls most businesses never notice.
SOC 2 Audit Process: Step-by-Step From Readiness to Certification
Phase 1: Readiness Assessment – Identify gaps, define scope, create remediation roadmap
Phase 2: Control Implementation – Build and document controls, configure technical solutions, deliver training
Phase 3: Control Operation Period – For Type I, proceed to audit. For Type II, operate controls consistently for 6-12 months while collecting evidence
Phase 4: Pre-Audit Preparation – Organise evidence, update documentation, create control matrix, brief team
Phase 5: Audit Fieldwork – Auditor reviews evidence, conducts interviews, tests controls, and identifies findings
Phase 6: Report Drafting and Review – Auditor drafts report, you review for accuracy, final report issued
Phase 7: Report Distribution and Maintenance – Distribute to clients, continue operating controls, plan next audit cycle
Continuous Compliance Best Practices:
- Maintain a compliance calendar with recurring activities
- Conduct quarterly internal audits
- Keep evidence collection ongoing
- Update policies as your business changes
- Invest in automation to reduce manual work
Before you buy cyber insurance, discover the selection criteria most companies overlook until it’s too late.
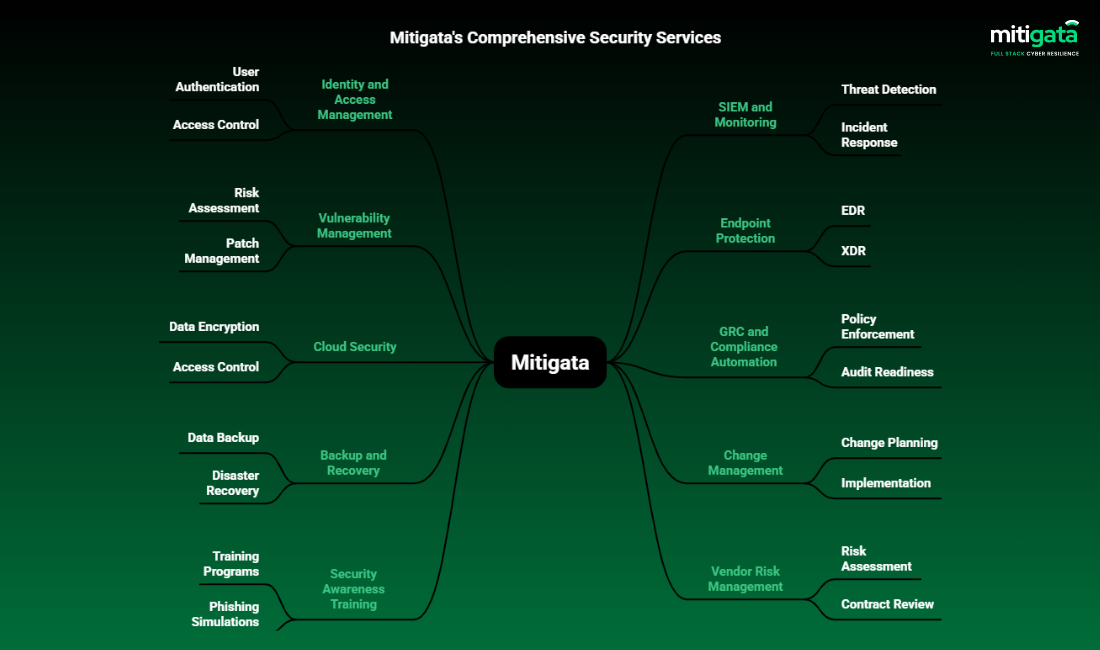
Security Tools That Support SOC 2 Control Requirements
Below are the tools companies use to meet SOC 2 Compliance requirements.
Conclusion
Companies that view SOC 2 as a competitive advantage rather than a compliance burden and people who meet SOC 2 compliance requirements are the ones who win enterprise deals, attract top-tier investors, and build lasting customer trust.
Your customers are waiting for proof that you take security seriously. The time to start your SOC 2 journey is now.
Book a quick call with Mitigata and automate your SOC 2 compliance process now!

