According to industry surveys, more than 63% of companies fail their first SOC 2 readiness assessment because they don’t fully understand the SOC 2 requirements or underestimate the work needed for audit preparation.
The numbers paint a clear picture of why getting SOC 2 requirements right matters. A 2025 benchmark of compliance programs found that 92% of organisations now undergo at least two formal audits per year, including SOC 2, ISO, PCI, and other frameworks.
In this blog, we will explore the SOC 2 audit requirements in simple terms, break down the certification process, highlight common mistakes, and show how you can move faster with less stress.
How Mitigata Helps You Meet SOC 2 Compliance Requirements Faster
We’re certified for ISO 27001, HIPAA, GDPR, and SOC 2 Type II ourselves. We don’t just teach compliance. We live it. Every requirement we help you implement is one we’ve successfully implemented in our own operations.
Here is how we help you meet SOC 2 compliance faster:
- A guided SOC 2 readiness workflow
- Human support plus automation
- Clear audit preparation
- A complete GRC automation tool
- Best Market Pricing
- Top-tier auditor partnerships
- 500+ Security tools
See All Your Risks Clearly on a Single Dashboard
Track open risks, control status, vendor assessments, and audits instantly with Mitigata’s cost-effective and scalable GRC platform.

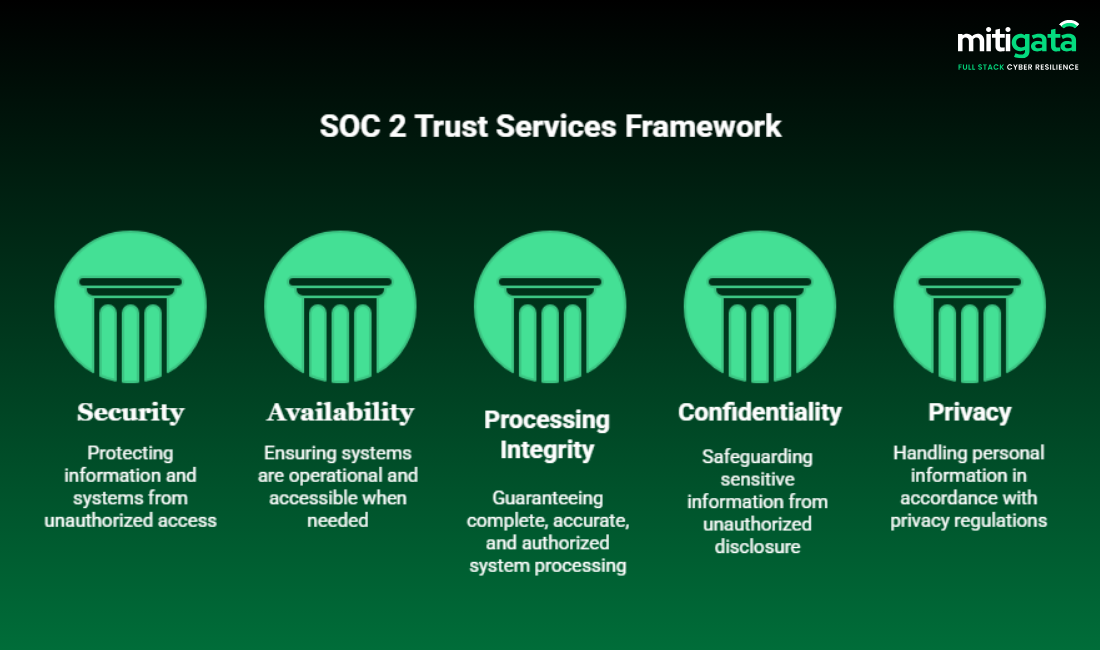
What is SOC 2 Compliance?
SOC 2 is a security and compliance framework that evaluates how well an organisation protects customer data based on the Trust Services Criteria (TSC):
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Every SOC 2 audit checks whether your controls are designed and implemented effectively to meet these criteria. SOC 2 applies to any company that handles customer data, especially in SaaS, finance, healthcare, and cloud services.
SOC 2 Type 1 vs Type 2 Requirements
Type 1 and Type 2 are fundamentally different approaches with distinct timelines, costs, and business impacts.
SOC 2 Type 1: The Snapshot Audit
What it evaluates: Your security controls at a specific point in time
What auditors check:
- Are your controls properly designed?
- Are they suitable to meet the Trust Services Criteria?
- Do your policies and procedures make sense?
Timeline: 2 to 4 months from start to finish
Best for:
- Companies new to SOC 2 compliance
- Validating your approach before committing to Type 2
- Quick proof of concept for initial customer conversations
Are you counted among those 60% of GRC users who manage compliance manually? It’s high time to check these popular automated GRC tools in India
SOC 2 Type 2: The Gold Standard
What it evaluates: Your security controls over a period of time (typically 3-12 months)
What auditors check:
- Everything from Type 1, PLUS…
- Did your controls operate effectively throughout the observation period?
- Do you have continuous evidence proving consistent implementation?
- Were there any gaps or failures during the observation period?
Timeline: 6 to 12 months for first-time audits (including gap remediation + observation period)
Best for:
- Enterprise sales where customers require Type 2
- Demonstrating sustained security commitment
- Companies with mature security practices
| Requirement Category | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Control design | Yes | Yes |
| Control operation over time | No | Yes |
| Evidence required | Light | Heavy |
| Audit duration | Short | Longer |
| Market value | Moderate | High |
Most companies confuse digital forensics and incident response, but the difference can make or break recovery. Do you know what your business needs first?
SOC 2 Certification Requirements: What Auditors Look For
In order to pass the SOC 2 audit, it is necessary to satisfy certain controls as described in the Trust Services Criteria. Even if the scope varies from one company to another, the auditors generally pay attention to the following:
Security Controls at Core (Required for all SOC 2 audits)
Security stands alone as the only required category in SOC 2, hence the auditors commence their examination from this point. They determine whether your systems are able to protect customer data from unauthorised individuals accessing the data. This includes:
Key items auditors review:
- MFA enforced across critical systems
- User onboarding and offboarding logs
- Role-based access controls
- Endpoint protection
- Encryption settings
- Network security configurations
- Log collection and monitoring activities
Organisational Controls Requirements
Technical controls alone aren’t enough. Auditors evaluate organisational practices, including background checks for employees in sensitive roles, security awareness training, and separation of duties to prevent excessive control by any single person.
From Policy to Proof Manage Everything in One Place
Mitigata GRC streamlines compliance tasks so you save time, reduce errors, and focus on what really matters.

Change Management Controls
Your engineering workflow is a big part of SOC 2 readiness.
Auditors try to confirm that code moves through a predictable, controlled process.
They typically ask questions like:
- Who approves changes?
- Is the code reviewed before deployment?
- What happens when a release fails?
- Are deployment logs complete and consistent?
A simple GitHub history with pull requests, approvals, and CI/CD pipeline artefacts often answers many of these questions quickly.
Risk Management and Governance
SOC 2 requires you to demonstrate that your company identifies risks proactively, not only when something breaks. Auditors look for:
- a risk assessment document
- a maintained risk register
- mitigation plans
- annual policy reviews
- employee security training logs
Incident Response Program
A surprising part of SOC 2 is that auditors expect to see how your team would handle an incident, even if you have never faced one.
So they look for:
- An incident response policy
- The communication plan (who gets notified and how)
- Escalation steps
- Training records or tabletop exercises
If you did have an incident, auditors usually ask for evidence of how it was resolved and what you learned from it.
Why are cyber insurance approvals getting tougher? Discover the application pitfalls most businesses never notice.
Common Mistakes Companies Make During SOC 2 Audit Preparation
SOC 2 preparation is often where companies lose time and money. Here are the mistakes we see most often.
Not understanding the SOC 2 requirements clearly
Many teams jump into the SOC 2 certification process without understanding which controls apply to them. This leads to confusion during evidence collection and delays during remediation.
Relying only on tools with no expert guidance
Automation is helpful, but SOC 2 needs interpretation. Without a human context, teams misconfigure controls or prepare incorrect evidence.
Poor documentation and scattered information
A lot of companies use spreadsheets, files, and email threads. This causes lost files, outdated versions, and incomplete evidence.
Starting without a SOC 2 readiness assessment
Skipping a readiness assessment is one of the most expensive mistakes. Teams discover gaps during the audit, which extends the timeline and increases auditor costs.
Before you buy cyber insurance, discover the selection criteria most companies overlook until it’s too late.
Conclusion
SOC 2 compliance requirements are comprehensive, but success comes down to understanding how you are preparing for SOC 2 compliance.
Mitigata gives you a guided SOC 2 readiness workflow, automation to reduce manual work, and real experts who help you prepare faster with fewer surprises.
If you want a simpler, clearer, and faster path to your SOC 2 audit, talk to our team today.

