Modern businesses rely on third-party vendors, who, unfortunately, come with significant risk.
More than 60% of data breaches are linked to these partnerships, worsening supply chain and data access issues.
More penalties imposed by authorities such as DORA, NIS2, and SEC rules do not require only a reactive response.
The use of TPRM (Third-Party Risk Management) techniques, including monitoring, risk tiering, and visibility into the fourth party, helps protect compliance, reputation, and finances.
This guide discusses about the definition of TRPM, its key benefits, and best practices.
Manage Vendor Risk
Like a Pro
Access powerful TPRM features at competitive pricing trusted by 800+ businesses.

Why Businesses Choose Mitigata for Third-Party Risk Management
Mitigata’s Third-Party Risk Management solution provides an efficient, automated approach to managing and mitigating risks associated with third-party vendors.
What you get with Mitigata:
Vendor Risk Monitoring: Continuous visibility into third-party applications, permissions, and access rights to flag compliance risks.
Custom Risk Questionnaires: Automated questionnaires assess vendor security and expose potential weaknesses.
Continuous Risk Assessment: Ongoing scans and checks confirm vendors meet security requirements.
Employee Risk Control: Tracks employee-granted access to third-party platforms and identifies associated vendor risks.
What Is Third Party Risk Management (TPRM)?
Third-party risk management is a process that takes into account all the risks that can be introduced by outside companies.
Such as vendors, suppliers, partners, and service providers, to recognise, assess, monitor, and mitigate them in a structured way.
A variety of risks are included in TPRM, such as:
- Cybersecurity and managing third-party cyber risks
- Data privacy and the exposure to regulatory fines
- Operational and risk of relying on a few suppliers
- Financial stability and vendor risk assessment
- Fourth-party risk management associated with subcontractors
How Does Third-Party Risk Management Work?
The TPRM procedure is based on a life cycle and has a life span of roughly two to three years, applying controls from onboarding to offboarding.
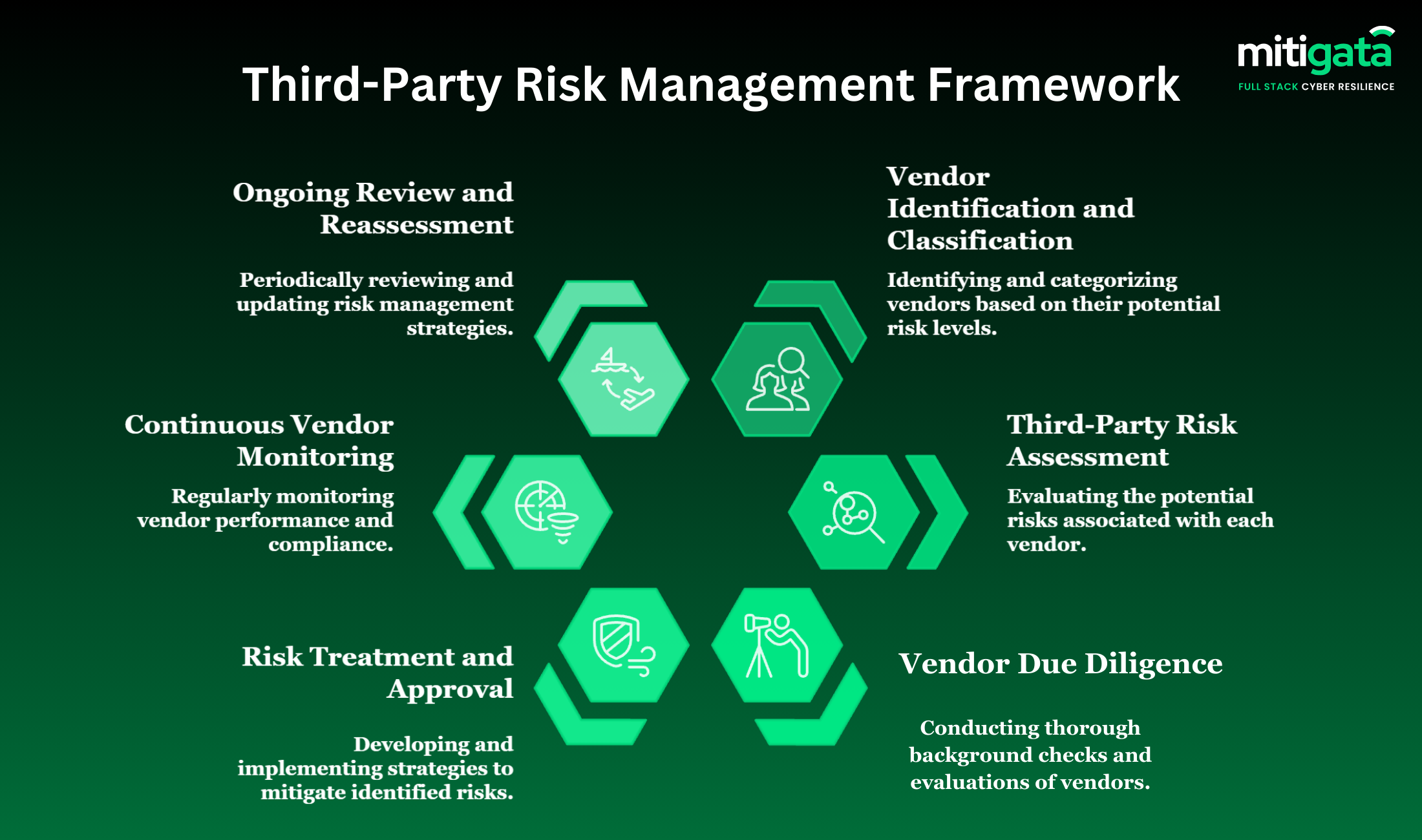
Vendor Identification and Classification
Each vendor is assigned an identifying code in a third-party vendor management system.
Vendors are classified by risk level based on data access, system exposure, and business dependency.
This stage helps in analysing the risk posed due to vendor concentration.
Third-Party Risk Assessment
A third-party risk assessment is conducted using a vendor risk assessment questionnaire or vendor due diligence form.
The documentation of policies, certifications, and security controls is examined. High-risk vendors undergo deeper supplier risk assessment procedures.
Learn why SMBs need cyber risk planning alongside insurance to stay resilient against modern threats.
Vendor Due Diligence
Vendor due diligence confirms the assessment responses through documentation, audits, and external intelligence.
The outcomes include a vendor due diligence report and a vendor risk rating.
Risk Treatment and Approval
On the one hand, the identified risks are linked to the corresponding mitigation measures.
This could mean, among other things, that the supplier has contractual provisions, remediation plans, or risk controls in place before onboarding is considered.
Take Control of Vendor Risk
With Mitigata
Centralise vendor assessments, due diligence, and monitoring with fast deployment.

Key Benefits of Third-Party Risk Management
Third-party risk management enables enterprises to manage vendor and supplier risk by recognising, analysing, and monitoring external relationships. Vendor-related security incidents have been reduced. Third party risk management is the process that helps identify vulnerabilities in vendors before incidents occur. The visibility of prompts reduces the risk of data breaches, system abuse, and third-party cyber risk. Regulatory and Audit Readiness are improved An unstructured third-party risk management framework, however, creates even more chaotic records for the vendor risk assessment, vendor due diligence, and remediation. It actually supports audits and regulatory reviews without last-minute effort.Stay up to date on PAM trends that help security teams reduce insider risk and privileged account misuse.Risk control over vendors and suppliers Vendor risk management consistently provides supplier risk insight across IT vendors, service providers, and outsourcing partners. Risk-based reviews limit the chance of a relationship with a high-risk vendor. Monitoring offers risk visibility over time. Third-party and continuous vendor monitoring track changes in risk between assessments. This helps teams respond more quickly to new security, compliance, or operational issues.
From Vendor Chaos
To Risk Control
Replace spreadsheets with automated TPRM workflows, risk scoring, and audit-ready reports in one platform.

Vendor accountability is stronger
Transparency in vendor risk ratings, due diligence reports, and remediation tracking leads to accountability. Vendors are clear on the expectations and the timeline for closing the gaps.
Onboarding decision-making has improved
The results of the third-party risk assessment provide guidance for onboarding approvals, contract terms, and risk acceptance decisions. This helps to select a vendor based on the right criteria.
Fourth-party exposure impact has been reduced
Management of fourth-party risk highlights the dependence on subcontractors and the risk of suppliers that are not covered. This reduces the exposure that stems from downstream vendors.
Compare leading IAM tools to choose the right access control solution for your business.
Scalable operational efficiency
Tools for third-party risk management and vendor risk management software cut down on manual follow-ups, assessments done via email, and tracking through spreadsheets.
Protection against vendor concentration risk
TPRM illuminates the over-reliance on particular suppliers. This is an indication that diversification and continuity planning are needed.
Stronger trust along the supply chain
The regular execution of supplier due diligence and vendor monitoring fosters trust among customers, partners, and internal stakeholders.
Best Practices of Third-Party Risk Management
Effective third-party risk management focuses on visibility, consistency, and accountability across the whole vendor ecosystem.
These practices help organisations manage vendor risk, supplier risk, and third-party cyber risk without slowing procurement or operations.
Risk-based vendor classification
Vendors can be classified by risk based on factors such as data access, system connectivity, and business dependency.
It is mandatory for high-risk vendors to undergo a more extensive vendor risk assessment and supplier due diligence, while low-risk ones have simple reviews only
This prevents the third-party risk management process from being bottlenecked and helps in keeping it scalable.
Discover the patch management tools that simplify updates and lower security risk.
Standardised third-party risk assessment
The use of consistent third-party risk assessment questionnaires and scoring models for all vendors is to be applied.
The standardisation enhances the quality of the assessment, facilitates vendor comparison, and lessens the delay in reviews through procurement and security teams across the organisation.
Strong vendor due diligence
The confirmation of assessment replies will be made by reviewing the policies, certifications, and audits and using third-party intelligence.
Vendor due diligence reports should record the gaps, the evidence that has been reviewed, and the vendor risk ratings for the purpose of audit and governance use.
Continuous vendor monitoring
The vendor’s security operational state, compliance status, and operational indicators are monitored continuously, so there will be no need for a delay in the response to vendor incidents, and the ongoing supplier risk mitigation will be supported.
Create Smarter
Risk Assessments
In Minutes
Deploy customisable questionnaires and scoring workflows that adapt to vendor type, industry, and compliance needs.

Fourth-party risk visibility
The suppliers and service dependencies critical to the major vendors will be revealed.
The fourth-party risk management not only mitigates the risk generated by the unknown supplier relationships but also enhances the transparency of supplier risks.
Clear remediation ownership
The risk owners, timelines, and follow-up actions for the identified gaps should be specified.
Vendor risk management tools should facilitate tracking remediation progress and maintain accountability across vendor third-party relationships.
Regular reassessment cycles
Vendors will be reassessed based on risk tier, regulatory expectations, and business impact. The scheduled reassessment keeps the third-party risk management framework.
Conclusion:
Implementing third-party risk management (TPRM) best practices enables organisations to navigate vendor risks proactively.
From tiering and assessments to continuous monitoring and reassessments.
This lifecycle approach not only ensures compliance with DORA and NIS2 but also minimises breach exposure and optimises operations for long-term resilience.
Contact Mitigata today to book a free demo, and we’ll help you get started with third party risk management with ease.

