Cybercriminals are making identity theft worse every day. They create fake profiles and use social engineering to trick people into sharing personal data.
In India, there could be about 8,500 cases of identity theft and data breaches in 2025, up 15% from before, with millions worldwide affected by recent fraud reports.
Old defences leave people and companies vulnerable to hacked accounts, financial losses, and data leaks. Strong identity protection is now a must.
This blog explains identity theft tricks, how attackers get your data, and simple steps to cut your risks.
Why Businesses Choose Mitigata for IAM Services
Mitigata is the top cyber resilience firm in India, protecting over 800 businesses in more than 25 sectors. We collaborate with top OEMs to deliver the optimal identity and access management solution tailored to your requirements.
Graphic: Reasons to Choose Mitigata For IAM Services
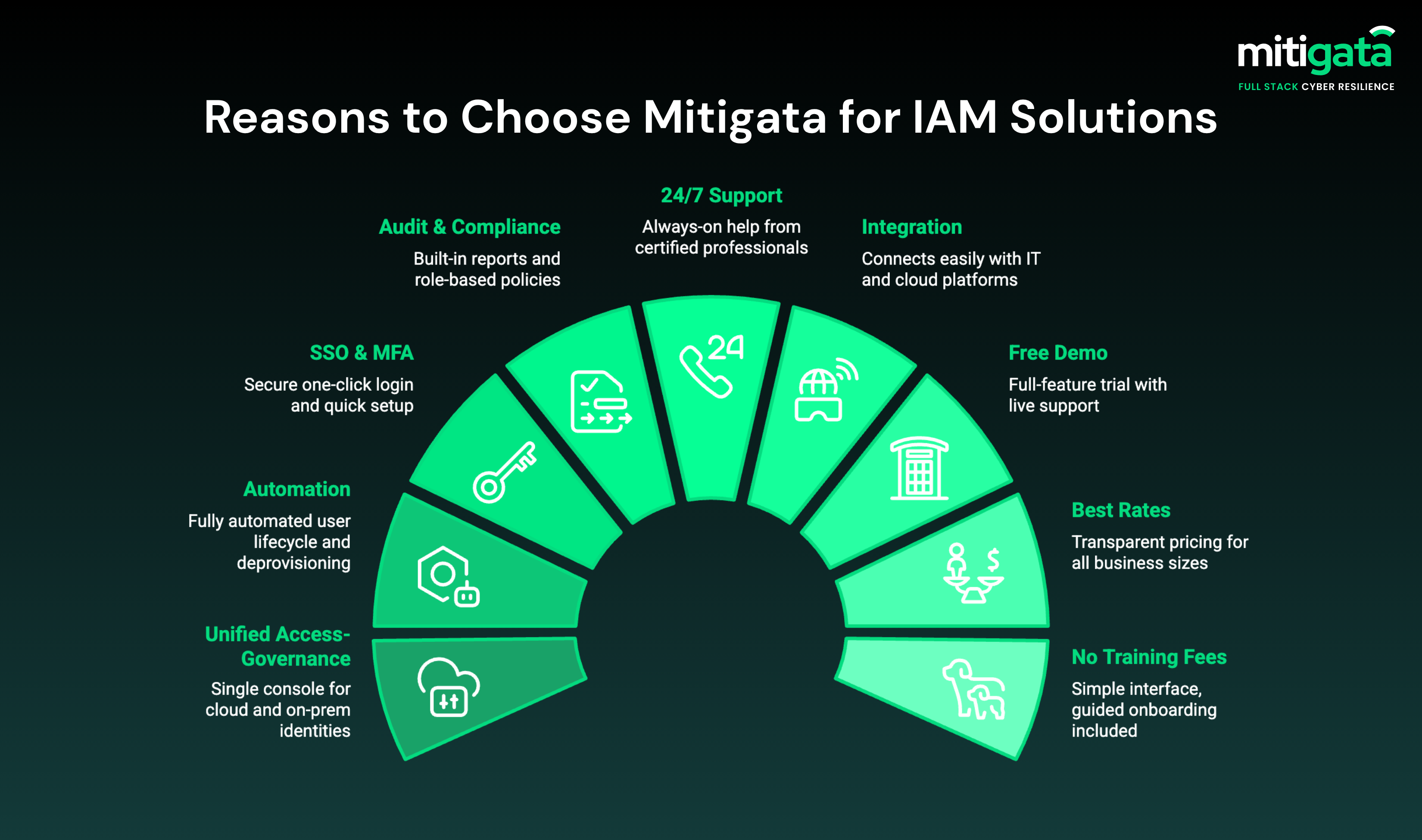
What do you get with us:
- Unified access-governance platform
- Automation of user lifecycle & deprovisioning
- Single sign-on (SSO) + strong MFA + smooth onboarding
- Audit-ready reporting + role-based policy templates + compliance tracking
- 24/7 support from experienced professionals
- Smooth integration with existing security systems
- Free demo
- Best market rates
- No extra training fees
What Is Identity Theft
“Identity theft” is a term used when someone obtains your private information and uses it to commit illegal transactions or carry out activities without your consent. Hackers focus on the most sensitive data, such as IDs, phone numbers, passwords, bank details, and even company accounts.
Among the most common scenarios are:
- Credit card and banking fraud
- SIM swap attacks
- Social media impersonation
- Online shopping fraud
- Synthetic identity creation
The whole process of phishing, fake OTP requests, harmful apps, and setting up trick websites helps hackers to collect enough data to impersonate someone. This is why cyber awareness training on identity theft is becoming a must for organisations.
Gain Full Visibility Into Who Has Access to What
Manage identities, permissions, and compliance effortlessly with IAM – fast deployment, minimal maintenance, maximum protection.

10 Practical Steps to Protect Yourself From Identity Theft
These ten helpful ideas work together to form a robust identity theft safeguarding measure for personal, banking, and work-related accounts.
Use strong, unique passwords: Attackers usually proceed with leaked passwords. If you use the same password everywhere, a security breach could reveal your entire online identity. A password manager can help by generating and storing unique passwords for every account.
Turn on Multi-Factor Authentication (MFA): MFA introduces a second step in your login procedure. Even if your password gets stolen, the person cannot access your account, as the verification code is needed too. This method is among the quickest ways to ensure you remain safe from identity theft.
Watch out for phishing attempts: Despite technology improvements, phishing continues to be an easy method for attackers to get their hands on your identity data.
Think you know phishing? These sneaky email tricks are more dangerous and more common than you can imagine. Find out how to spot them before it’s too late
Emails, messages, and sometimes even phone calls requesting one-time passwords, access codes, bank or personal information should be treated with utmost caution.
Stay away from links that you have not been sent and do not open attachments from people you do not recognise.
Limit personal information shared online: Gradually, attackers will get your small details through social media and use them to answer security questions or impersonate you.
Posting ID numbers, birthdays, phone numbers, travel updates, and financial information are the first steps toward exposing yourself to dealers on the dark web.
Keep devices updated: Security holes that attackers use to their advantage get blocked with the latest updates. Make use of security products that you can trust to prevent spyware and viruses that can collect your information without you knowing.
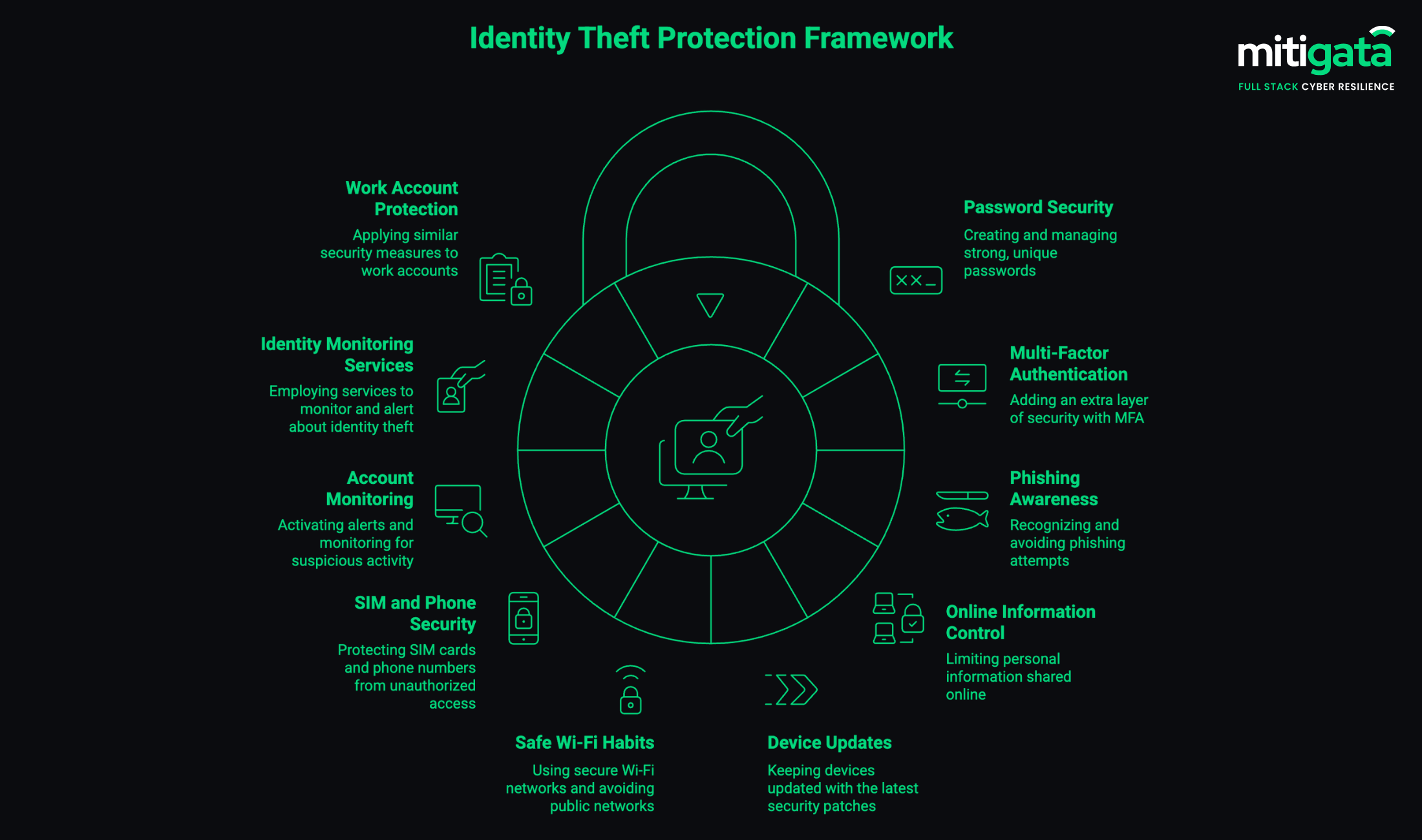
Use safe Wi-Fi habits: Using public Wi-Fi allows attackers to easily access your logins or payment information. Stay away from sensitive accounts on public networks. If there is no other way out, at least use a VPN as a shield for your connection.
Secure your SIM and Phone Number: Your mobile number is used for one-time passwords, password resets, and account recovery.
To prevent identity theft through SIM swapping:
- Set a SIM PIN.
- Never disclose one-time passwords.
- Call your mobile operator if you suddenly lose your network signal.
Using a phone for ID fraud protection is often underrated, but it is actually very crucial.
Activate Account Alerts and Monitoring: Set up alerts for your account movements, changes in password, and logins. Fast alerts allow you to spot dubious activities instantly and frustrate the attempts of identity theft before any damage is incurred.
Employ Identity Monitoring Services: Dark monitoring tools will inform you about leaks, password hacks and unusual activities associated with your name or email. You will thus be in a position to take action before the hackers can actually make use of the acquired information.
Use Similar Protection for Work Accounts: Workers frequently operate from personal devices that pose an increased security risk. Apply the same rules for emails, cooperation software, cloud storage, and internal tools. This not only stops the leaking of company data but also protects the whole team by minimising exposure.
Secure Every Login, Simplify Every Access
Get an IAM solution built for your workflows – flexible, scalable, and backed by 24/7 assistance without extra setup or training costs.

Key Signs That You Might Be a Victim of Identity Theft
Pay attention to these red flags; responding early can limit damage:
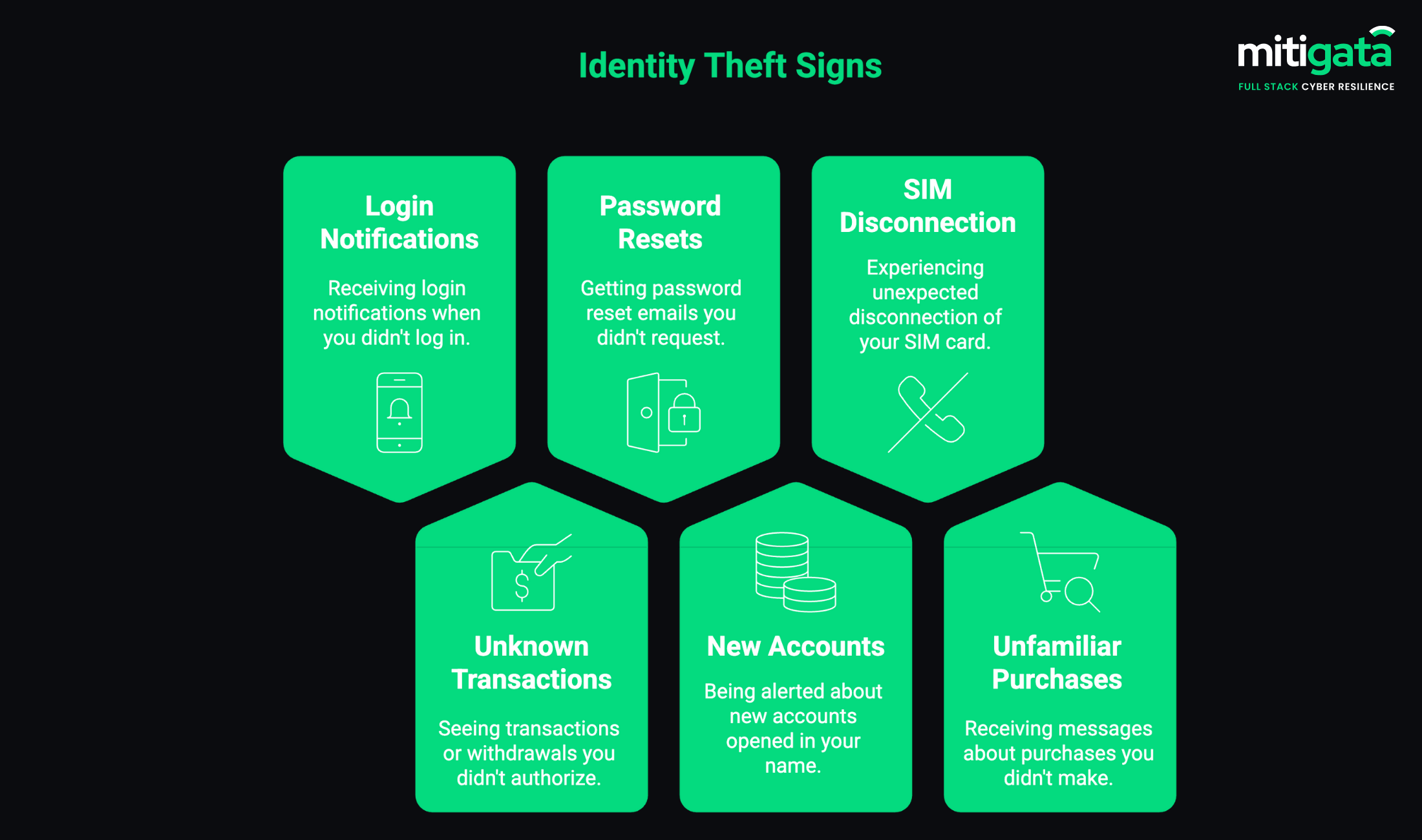
- Unexpected login notifications
- Transactions or withdrawals that you are not aware of
- Emails with concerning password resets that you did not ask for
- Alerts about new accounts created using your name
- Unexpected disconnection of the SIM
- Messages concerning buying that you did not do
Acting on this quickly can mitigate the harm.
Why IAM is Necessary for Identity Protection
IAM (Identity and Access Management) is now a cornerstone of the company’s digital security. Traditional access controls can’t keep up due to the growing number of teams, devices, and workloads moving to the cloud.
IAM is the one that provides the order of who will access what, when, and under what conditions. Most breaches today start with compromised identities, thus making strong identity control an essential security layer.
Check out our guide on the best identity-access management toolsfor businesses. Step towards better access control and secure identity protection.
IAM provides clear benefits such as:
Control in access: Only approved users will have access to apps, systems, and data that are sensitive.
Lower risk of credential misuse: Strong authentication will prevent attackers from accessing even if passwords are leaked.
Protection for remote and hybrid teams: Access is secure regardless of the place where users log in.
Simplified onboarding and offboarding: New users are granted the necessary permissions immediately, and when someone leaves, access is revoked immediately.
Compliance support: IAM is a tremendous help in allowing organisations to keep audit trails and to meet the security requirements.
IAM not only reinforces the identity protection but also reduces human errors as well as the attack surface. It enables organisations to identify theft, unauthorised access, and internal misuse in a structured way, thus making it an integral part of modern cyber awareness and defence.
Not sure which IAM tool suits your business? Read our latest blog on choosing the right IAM tool for businesses and make identity protection easy and effective.
Conclusion
Even if it is just about using strong passwords, MFA, safe browsing, and monitoring the account, the attackers would find it very difficult to get your information.
Such identity theft safety tips support not only the individuals but also the employees in securing their accounts and thus minimise the risk of falling victim to modern ID fraud threats.
For a partner that delivers all key network security tools, ensures round-the-clock monitoring, provides DFIR, and offers comprehensive cyber resilience in one place, Mitigata stands out as the best option.
Schedule a free demo call with our specialists today!

