Ever been asked, “Do you have SOC 2 Type 2?” and felt that quiet panic?
Or wondered why investors care so much about a compliance report that most founders don’t fully understand?
If you are running a tech company today, SOC 2 is your golden ticket to crack global markets, particularly in finance and healthcare sectors, where data security is completely non-negotiable.
Over 60% of fintech startups hit compliance walls early in their growth journey, forcing them to scramble for SOC 2 Type 2 reports just to maintain investor confidence and close enterprise deals.
And it’s not just fintech. A 2025 compliance survey revealed that SOC 2 now ranks among the top three “most important” security frameworks across all industries and revenue bands.
In this blog, we’ll break down the complete SOC 2 Type 2 controls list, explore the specific security controls and reveal the common compliance controls companies miss.
How Mitigata Helps You Meet SOC 2 Compliance Requirements Faster
Most compliance tools are built by teams that have never faced a real audit. Mitigata is different. We are certified to ISO 27001, HIPAA, GDPR, and SOC 2. We do not just explain compliance. We have lived it, passed audits, and refined what actually works.
Here is how Mitigata helps you move faster:
Guided SOC 2 readiness workflow
Step-by-step guidance for every SOC 2 control, with clear instructions, templates, and evidence requirements.
Human support + automation
Automation handles evidence collection and monitoring, while experienced compliance experts support you when you need clarity.
Clear audit preparation
All evidence is organised, mapped to controls, and ready for auditors, reducing last-minute stress.
Complete GRC automation platform
Manage SOC 2, ISO 27001, HIPAA, and GDPR in one place as your compliance needs grow.
Transparent, market-friendly pricing
Pricing that scales with your company, without hidden costs or surprises.
Trusted auditor partnerships and 500+ tools
Work with top auditors and access built-in tools for risk management, policies, vendors, and incident response.
See All Your Risks Clearly on a Single Dashboard
Track open risks, control status, vendor assessments, and audits instantly with Mitigata’s cost-effective and scalable GRC platform.

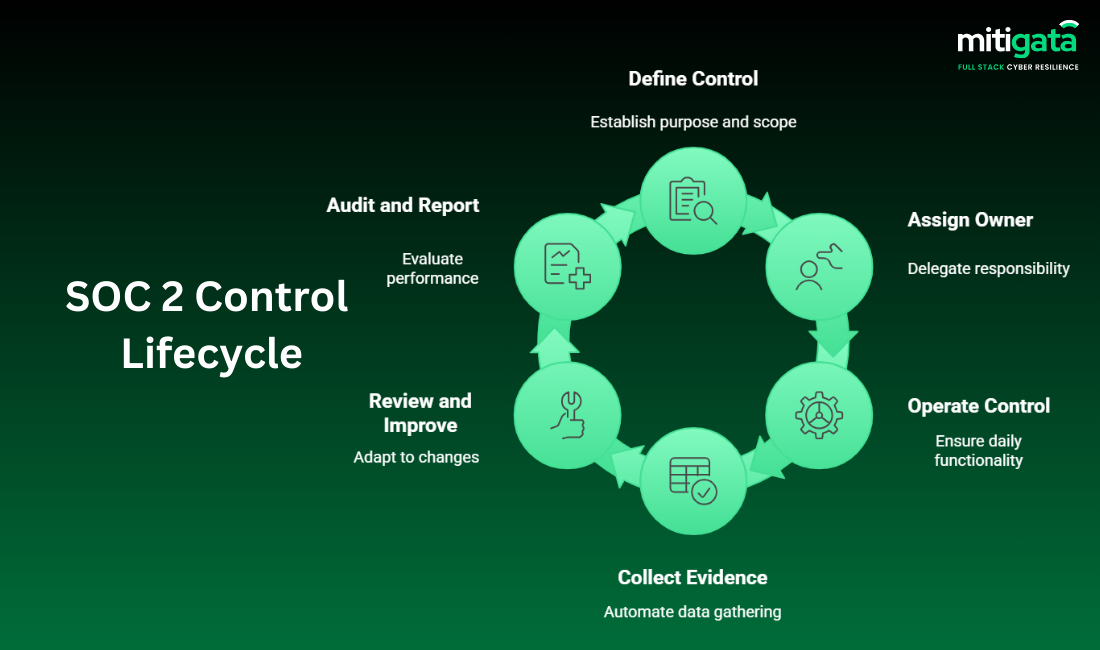
What Are SOC 2 Compliance Controls?
SOC 2 controls are specific security measures and processes your organisation implements to protect customer data and systems.
Controls can be:
- Preventive (stopping bad things from happening, like firewall rules)
- Detective (catching bad things when they happen, like intrusion detection)
- Corrective (fixing bad things after they happen, like incident response)
Your job isn’t to implement every possible control. It’s to implement the right controls for your specific risk profile and document that they’re working effectively over time.
Are you counted among those 60% of GRC users who manage compliance manually? It’s high time to check these popular automated GRC tools in India
SOC 2 Type 2 vs Type 1
SOC 2 Type 1 is a point-in-time assessment. An auditor examines your controls on a specific date and confirms they’re designed appropriately. It’s a snapshot. It proves you had your security house in order on inspection day.
SOC 2 Type 2 is the real deal. It covers a period of time, usually 3, 6, or 12 months. The auditor doesn’t just check if your controls exist. They verify that you’ve been operating those controls consistently and effectively throughout the entire audit period.
| Requirement Category | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Control design | Yes | Yes |
| Control operation over time | No | Yes |
| Evidence required | Light | Heavy |
| Audit duration | Short | Longer |
| Market value | Moderate | High |
SOC 2 Type 2 Controls List
Here’s a comprehensive breakdown of the SOC 2 Type 2 controls organised by category.
Key SOC 2 security controls list:
- User access management and role-based access
- Multi-factor authentication for critical systems
- Secure onboarding and offboarding of employees
- Change management approvals
- Incident response planning and testing
- Security awareness training
- Vendor risk management
Example: If an engineer leaves the company, the control requires proof that their access was removed promptly across all systems.
From Policy to Proof Manage Everything in One Place
Mitigata GRC streamlines compliance tasks so you save time, reduce errors, and focus on what really matters.

Availability Controls
These controls ensure systems stay up and recover quickly.
- Uptime monitoring
- Incident response for outages
- Backup and recovery testing
- Capacity planning
Example: Showing logs from backup tests performed quarterly can satisfy availability control requirements.
Confidentiality Controls
These protect sensitive or restricted data.
- Data classification policies
- Encryption at rest and in transit
- Restricted access to confidential data
- Secure data disposal
Example: Evidence that customer financial data is encrypted and access is limited to approved roles.
Most companies confuse digital forensics and incident response, but the difference can make or break recovery. Do you know what your business needs first?
Processing Integrity Controls
These ensure systems process data accurately.
- Input validation checks
- Error handling procedures
- Change approvals for system updates
- Monitoring and alerting
Privacy Controls (If Applicable)
Required if you handle personal data.
- Privacy notices
- Consent management
- Data retention rules
- Data subject request handling
Common SOC 2 Compliance Controls Companies Miss
Here are the most common issues SOC 2 compliance auditors flag:
Access reviews without evidence
Many teams regularly review user access, but fail to document it. Auditors need proof, not promises. This usually means screenshots, approval records, or system-generated logs showing who reviewed access, when it was done, and what actions were taken.
Vendor risk management gaps
Vendor assessments are often treated as a one-time activity during onboarding. SOC 2 expects ongoing monitoring. Auditors look for periodic reviews, updated risk assessments, and evidence that high-risk vendors are re-evaluated regularly.
Change management shortcuts
Emergency fixes happen, especially in fast-moving teams. The problem arises when changes are pushed without approvals or documentation. SOC 2 requires proof that even urgent changes are reviewed, tested, and logged after the fact.
Incident response plans that are never tested
Having an incident response policy is not enough. Auditors expect evidence of testing, such as tabletop exercises or simulations. Without proof that the plan was practised, the control is considered weak.
Overlooking internal tools and scripts
Internal dashboards, scripts, and admin tools often handle sensitive data but are excluded from security reviews. Auditors expect these tools to follow the same access controls, logging, and monitoring as customer-facing systems.
Why are cyber insurance approvals getting tougher? Discover the application pitfalls most businesses never notice.
Tools That Help Manage SOC 2 Controls
Sure, using spreadsheets for SOC 2 is an option, but it involves a lot of hassles and mistakes. The following are the must-have tools for your SOC 2 compliance:
GRC Platforms: Integrate control frameworks, automate evidence collection, monitor status, and create audit packs.
Identity and Access Management (IAM): Unifies the authentication and access control procedures.
SIEM – Gather logs from various sections of your system, determine the security events that occurred, and retain the trails for audits.
Vulnerability Management: Entails regularly scanning your systems for flaws and keeping records of the efforts taken to remedy them.
Endpoint Detection and Response (EDR): Ensure that the endpoints are not vulnerable to threats, and at the same time, allow the monitoring of endpoint activities.
Change Management and Ticketing: The whole process of change requests, approvals, testing, and finally, the implementation.
Vendor Risk Management: Facilitate the evaluation and continuous observation of the security posture of the vendors.
Pro tip:
Auditors prefer tools that automatically generate audit-ready evidence rather than manual uploads.
Ready to simplify compliance and cut manual work?
Mitigata’s GRC automation tool keeps your controls monitored, evidence organised, and audits stress-free.

Conclusion
Understanding your SOC 2 compliance control list, implementing proper security measures, and avoiding common compliance issues will help you win deals with confidence.
Schedule a demo with Mitigata today to turn SOC 2 into a growth booster.

