You are logged into your bank account, and the balance shows ZERO.
This isn’t rare anymore. Identity theft has become a massive black-market business on the dark web. In 2025 alone, over 6.4 million cases were reported in the U.S., with the average victim losing $497.
This is an era when cyber threats are evolving at jet speed, and so should we, to protect our identities and our assets.
In this blog, we break down how personal information ends up on the dark web and the steps you can take to protect your data before it’s exploited.
Mitigata – Your Reliable Cybersecurity Partner
We at Mitigata operate in the shadows of the digital underground, so you don’t have to. With more than 500 cyber solutions and extensive experience in insurance, security, and compliance, we assist organisations in identifying, evaluating, and eliminating risks before they become major emergencies.
This is where we scan:
- Forums for Hackers
- Illegal Marketplaces
- Channels on Telegram
- Exposed Assets from Breach Archives
Cybercriminals can’t hide when Mitigata monitors dark web threats
Mitigata delivers real-time detection, expert-led response, and market-best pricing for which your budget shouldn’t compromise.

What Is Dark Web Identity Theft?
Dark web identity theft refers to the illegal use of private information for its sale or exploitation through online marketplaces.
Dark web identity theft is the term used to describe when personal data, such as user ID, passwords, bank info or identity papers, is revealed on illegal websites.
This illegal trade in dark web identities creates a cycle of fraud, account misuse, and financial loss.
The dark web identity theft case often begins with data breaches, phishing, or malware infections that result in the exfiltration of personal data, which is then sold on the dark web.
From data leaks to phishing, this article explains how to protect yourself from identity theft in everyday life.
Common Types of Identity Theft on the Dark Web
Several common forms of identity theft appear across dark web forums and marketplaces, such as:
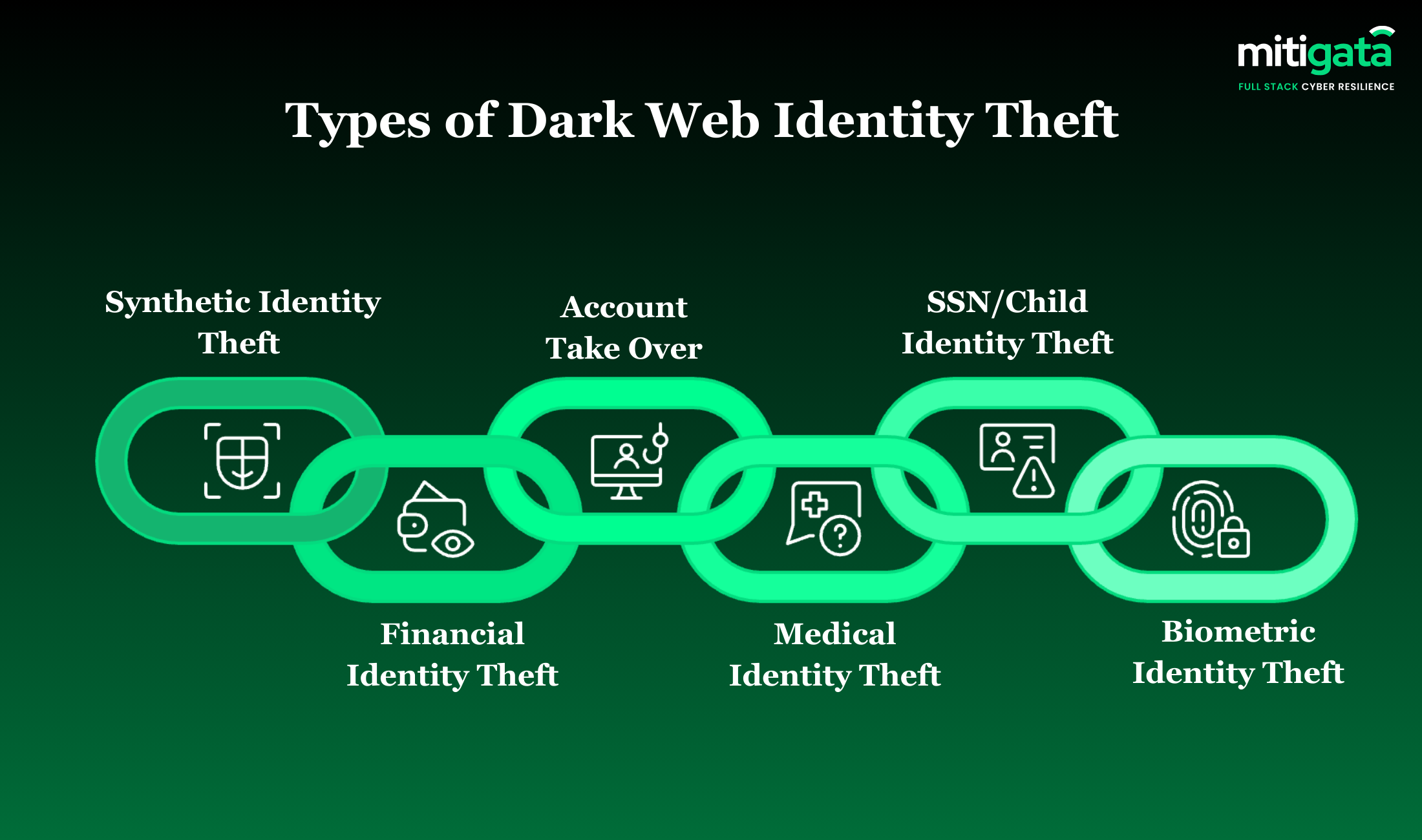
Synthetic Identity Theft
The hackers rely on fake identities and partial information, such as SSNs, dates of birth, or addresses, obtained from breach dumps and dark web listings of stolen identity data.
The attackers then use this data, combined with a fake name, to create new accounts, obtain loans, and commit financial fraud that remains undetected for many years.
Financial / Credit Card Identity Theft
This type of theft mainly deals with the direct financial abuse of the stolen payment information.
Financial identity theft occurs through dark web markets that sell card numbers, CVV data, expiration dates, and full billing profiles.
This information is used for unauthorised transactions, online purchases, and further sales within various fraud networks.
Stolen data on the dark web often includes bundled financial records.
Ever wondered how personal and company data ends up for sale? This guide explains the dark web data ecosystem.
Account Takeover
This approach aims to hijack existing user accounts using stolen login credentials.
Account takeover activity on the dark web is linked to credential theft from phishing campaigns, malware infections, and infostealer logs.
Reusing passwords across email, banking, cloud tools, and enterprise systems will result in data loss and service outages.
Medical Identity Theft
This type of theft leverages information from the healthcare and insurance sectors to commit fraud, with leaked data exposing patient records, policy numbers, and treatment data.
Criminals exploit this for filing false claims, accessing medical services, or reselling records. Often, victims realise the issue only after disputes over billing or coverage denials.
A practical guide to checking whether your email is on the dark web and what steps to take next.
SSN / Child Identity Theft
This type of theft affects the social security numbers of both adults and children.
SSN identity theft encompasses child identity theft, in which otherwise inactive SSNs are used to establish credit histories.
The dark web’s identity theft market subdivides into the selling of SSNs for employment fraud, tax scams, and loans.
Usually, the detection occurs several years after the fact, when the financial damage has already been done.
Biometric / Digital ID Theft
This category of theft targets identity data associated with physical or digital authentication.
Biometric and digital ID theft encompasses fingerprints, facial data, voiceprints, and government-issued digital identities.
Once in the thieves’ possession through data breaches or insecure storage, this information is traded on dark web forums under stolen identities.
Biometric data, unlike passwords, cannot be replaced, thereby increasing long-term risk.
Every leaked password or record can shut down your business
Trusted by 800+ businesses, our platform ensures continuous protection with advanced features for you and your data.

How Identity Theft Operates on the Dark Web
The methods used for identity theft on the dark web are similar to those employed in non-identity theft operations and follow a well-defined pattern dictated by cybercriminal networks.
To begin with, hackers acquire sensitive user information through phishing attacks, malicious software infections, and compromised databases.
Infostealers operate on the dark web to monitor and collect browser data, saved passwords, and session tokens.
Dark web forums list this data for sale, including the identities of individuals whose information was stolen.
Buyers gain access to criminals’ impersonation, resale, or use of the information across different platforms.
The cycle of identity theft and impersonation on the dark web follows a pattern of repeatedly using stolen credentials to exploit accounts.
Prevention of Dark Web Identity Theft Threats
The best defence is spotting risks early and reducing the chances of misuse. Key prevention measures include:
Dark web monitoring
Tracking stolen data helps identify what information is being traded and who may be targeting it.
Strong password practices
Unique, regularly updated passwords lower the risk of attackers reusing leaked credentials.
Multi-factor authentication (MFA)
Adding an extra layer of verification makes account takeovers far more difficult, even if passwords are exposed.
Employee awareness training
Informed employees are less likely to fall for phishing attacks, which remain a common entry point for data theft.
Ongoing breach monitoring
Continuous checks help detect leaked data early, before it leads to financial or identity damage.
Train Your Workforce with India's Leading Phishing Simulation
Mitigata’s simulations offer experience-based learning, role-specific campaigns and regular tests.

Conclusion
Dark web identity theft exploits stolen SSNs, credentials, and full kits sold for pennies.
Proactive steps such as dark web monitoring, VAPT scans, MFA, and GRC frameworks help prevent synthetic fraud, account takeovers, and medical ID breaches.
Contact Mitigata now to secure your identity and operations.

