In 2025, India emerged as one of the world’s most targeted nations for cyberattacks, with organisations facing an unprecedented wave of digital threats. According to industry reports, Indian enterprises faced an average of over 2,000+ attacks per week, which is a 45% increase year-on-year compared to global averages.
From AI-powered ransomware encrypting hospital systems to sophisticated phishing schemes draining bank accounts, the cyber threat landscape evolved faster than most security teams could respond.
This blog highlights the key cyber attacks in 2025 while providing actionable insights for strengthening your defences in 2026.
Why Businesses Choose Mitigata For Cybersecurity
Before we dive into the data, here’s why over 800 companies across 25+ industries trust Mitigata to protect their digital assets:
Proactive Threat Detection – We identify risks before they become breaches
24/7 Monitoring – Real-time surveillance of your attack surface to ensure zero dwell time for attackers.
Expert Response Teams – Immediate action when threats emerge, minimising downtime and financial loss.
Compliance Support – Stay ahead of DPDPA and industry regulations with automated reporting tools.
Proven Track Record – Zero successful breaches across our protected clients in 2025

Executive Summary: India’s Cyber Crisis by the Numbers
Record-breaking cyber threats hit India hard in 2025, exposing urgent gaps in defences.
| Statistic | Value | Context |
|---|---|---|
| Total Cyber Attacks | 265.52 million | Across websites and endpoints nationwide |
| Malware Detections | 369.01 million | Monitored across 8.44 million endpoints |
| Attacks per Org/Week | 2,000+ | 47% higher than the global average of 1,925 |
| Financial Fraud Losses | ₹36,450 crore | Reported through the National Cyber Crime Portal by Feb 2025 |
Cybersecurity automation sounds foolproof until you see what it misses. Here are 6 cybersecurity automation tools and the blind spots that come with them.
What the Data Reveals About India’s Cyber Vulnerability
In 2025, India experienced more malware attacks than almost any other nation worldwide. Here’s why Indian businesses were disproportionately targeted:
- Rapid digital adoption without security maturity – Organisations rushed to cloud platforms and digital services, but left security as an afterthought. This created a “security debt” that attackers eagerly exploited.
- Endpoint explosion – With 8.44 million monitored endpoints, each device became a potential entry point for attackers. The rise of IoT devices in manufacturing and logistics specifically widened this gap.
- Legacy infrastructure – Outdated systems, unpatched software, and poor access controls created easy targets. Many SMEs were found running End-of-Life (EOL) operating systems, lacking critical security updates.
- Valuable data concentration – Banking, healthcare, and government sectors hold treasure troves of personal and financial information.
The average cost of a data breach in India reached an all-time high of ₹22 Crore in 2025, a 13% increase from the previous year (2024).
Cyber Risk Insurance Policy Starting at Just ₹95,000/ Year*
With Mitigata, you get the best market pricing and fast claims—plus proactive defence through our free cyber risk console.

Most Targeted Sectors:
- Financial services managing billions in daily transactions
- Healthcare providers storing sensitive medical records
- Government agencies with citizen databases
- Telecommunications companies controlling critical infrastructure
- Educational institutions with valuable research data
AI-Powered Cybercrime: The Game Changer
Artificial intelligence fundamentally transformed the cybercrime landscape in 2025. What used to take attackers weeks now takes minutes, and what used to require expert skills can now be automated.
Automated phishing generation – AI creates convincing, personalised emails at a massive scale
Behaviour analysis – Malware learns user patterns to avoid detection
Rapid ransomware deployment – Systems encrypted in minutes instead of hours
Adaptive malware – Threats that evolve to bypass security measures in real-time
Deepfake impersonation – Fake videos and voices tricking employees into transferring funds.
In one notable case, a Mumbai-based firm lost ₹2 Crore when an employee was duped by a deepfake video call of their CFO.
Choosing the right DLP tool is critical to preventing data leaks. This guide explains how to choose a DLP tool based on real security and compliance needs.
Digital Expansion Creates New Vulnerabilities
The rapid adoption of cloud platforms, SaaS tools, mobile access, and third-party integrations drove cyber attacks to record levels in 2025. Organisations rushed toward digital transformation but left security gaps wide open.
Cloud security emerged as a critical risk area, with one breach exposing nearly 500GB of sensitive personal and biometric data due to an unsecured cloud storage environment. Misconfigured S3 buckets and poor IAM (Identity and Access Management) policies were the leading causes of these leaks.
The Expanding Attack Surface Problem
Endpoint proliferation – Every device, from laptops to IoT sensors, is a potential entry point
Third-party integrations – Vendors and partners create additional attack vectors
Remote access requirements – VPNs and remote desktop protocols are often poorly secured
API vulnerabilities – Application programming interfaces expose backend systems
Mobile device risks – BYOD policies without proper security controls
Pro Tip: Do not rely solely on traditional antivirus software. Implement Attack Surface Management (ASM) to continuously discover and map your digital assets.
Why overpay for features you’ll never use?
Mitigata helps SMBs secure systems instantly with zero training, smooth setup, and the industry’s most affordable pricing.

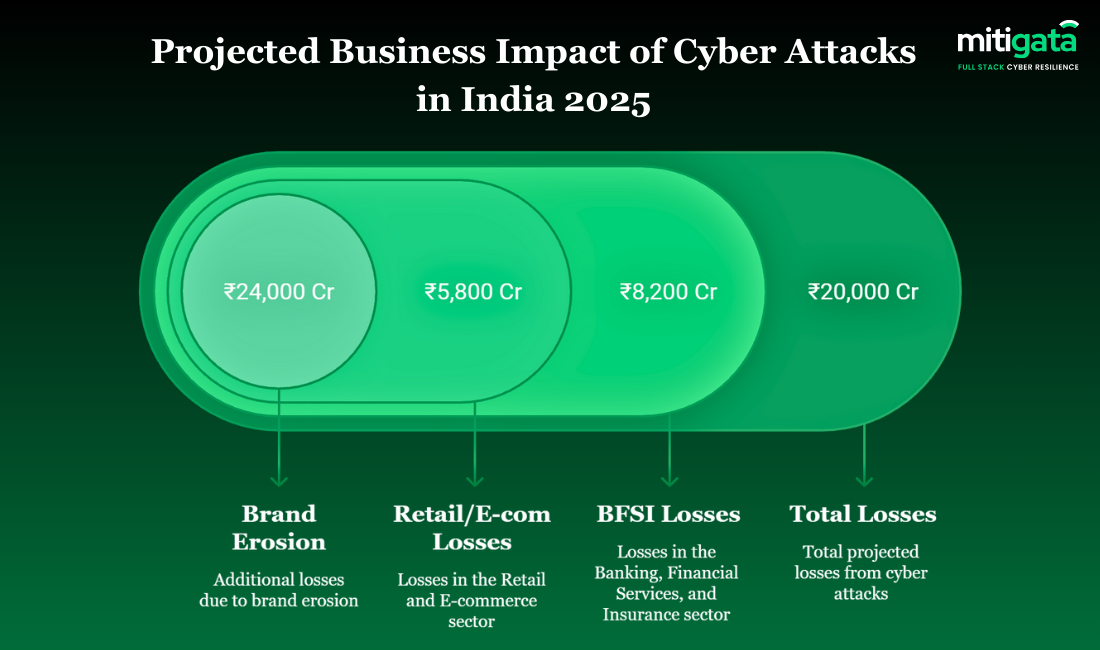
Business Impact of Cyber Attacks in India 2025
Attackers targeted vulnerable areas like payment systems, customer data, and unmonitored internal platforms.
The impact went beyond money; businesses faced:
- lost customers
- disrupted services
- reputational damage
- regulatory scrutiny
- lawsuits, and higher cybersecurity costs, which hurt growth.
Real-World Example: The SME Ransomware Crisis
A mid-sized logistics firm in Pune faced a lock-bit ransomware attack in mid-2025. Without cyber insurance or offline backups, they were forced to halt operations for two weeks, resulting in a ₹3.5 Crore loss and the cancellation of two major client contracts.
Regulatory Focus and National Cybersecurity Efforts
The Indian government introduced tougher rules requiring companies to report security breaches and follow stricter safety standards.
However, these new rules affected companies differently:
- On the one hand, organisations became more transparent and accountable for protecting data.
- On the other hand, many struggled to keep up, especially smaller companies that lacked strong security systems or couldn’t find enough trained cybersecurity professionals.
Key Compliance Mandates:
- Mandatory breach notification within statutory timelines (often 6 hours for CERT-In and 72 hours for the Data Protection Board).
- Regular security audits and vulnerability assessments
- Data protection impact assessments for high-risk processing
- Appointment of data protection officers
- Incident response and business continuity planning
- Enhanced access controls and encryption requirements
Looking for the best network security tools? This complete guide breaks down top solutions, use cases, and how to choose the right one.
Consequences of Non-Compliance:
Organisations that failed to meet requirements faced:
- Financial penalties – Hefty fines based on revenue or severity, reaching up to ₹250 Crore under the DPDPA.
- Operational restrictions – Temporary business suspensions
- Surprise audits – Disruptive regulatory inspections
- Public disclosure – Reputational damage from published violations
- Criminal liability – Personal accountability for executives
Cybercriminals can’t hide when Mitigata monitors dark web threats
Mitigata delivers real-time detection, expert-led response, and market-best pricing.

Essential Security Steps for 2026
Immediate Actions
- Conduct comprehensive security assessments to identify vulnerabilities
- Implement multi-factor authentication across all systems
- Deploy endpoint detection and response (EDR) solutions
- Establish regular backup and recovery procedures
- Create an incident response plan and test it
Strategic Initiatives:
- Adopt zero-trust architecture principles
- Implement advanced threat detection using AI/ML
- Establish a security operations centre or partner with an MSSP
- Develop a comprehensive vendor risk management program
- Invest in security awareness training for all employees
From phishing to password hygiene, this guide outlines core cybersecurity awareness training topics that actually reduce risk.
Conclusion
Smart organisations are leveraging threat intelligence and optimising their security monitoring to detect threats early. Don’t wait for a breach to prioritise cybersecurity.
Contact Mitigata today to strengthen your defences for 2026 and build complete cyber resilience.

