In 2025, the average loss per organisation from cyber breaches reached $4.88 million, a 10% increase from the previous year.
Consequently, the adoption of red, blue, and purple teaming has dramatically increased.
With 68% of companies conducting purple team drills every three months, companies reduce mean time to detection (MTTD) by up to 40% and attacker dwell time from 21 days to less than 10 days.
The collaboration among these three teams not only boosts the validation rates of security controls by 55% but also minimises alert fatigue through shared knowledge.
Why Businesses Choose Mitigata for Cyber Defence
Mitigata is India’s leading cyber resilience company, trusted by more than 800 companies across 25+ industries.
Our teaming services offer:
- Real-world attack simulations illustrating actual threats across systems, users, and processes.
- Employee readiness against social engineering attacks is tested through practical exercises.
- Clear, actionable insights, with prioritised improvement activities.
- Trusted by businesses in BFSI, Aviation, Retail, and Manufacturing.
- Red, Blue, and Purple Teaming offered within a single cohesive framework.
- Market-leading pricing with enterprise-grade security outcomes.
- 24-hour expert help from qualified security professionals.
How Strong Is Your Security When No One’s Watching?
Test it with Mitigata’s red, blue, and purple teaming, trusted by 800+ global clients.

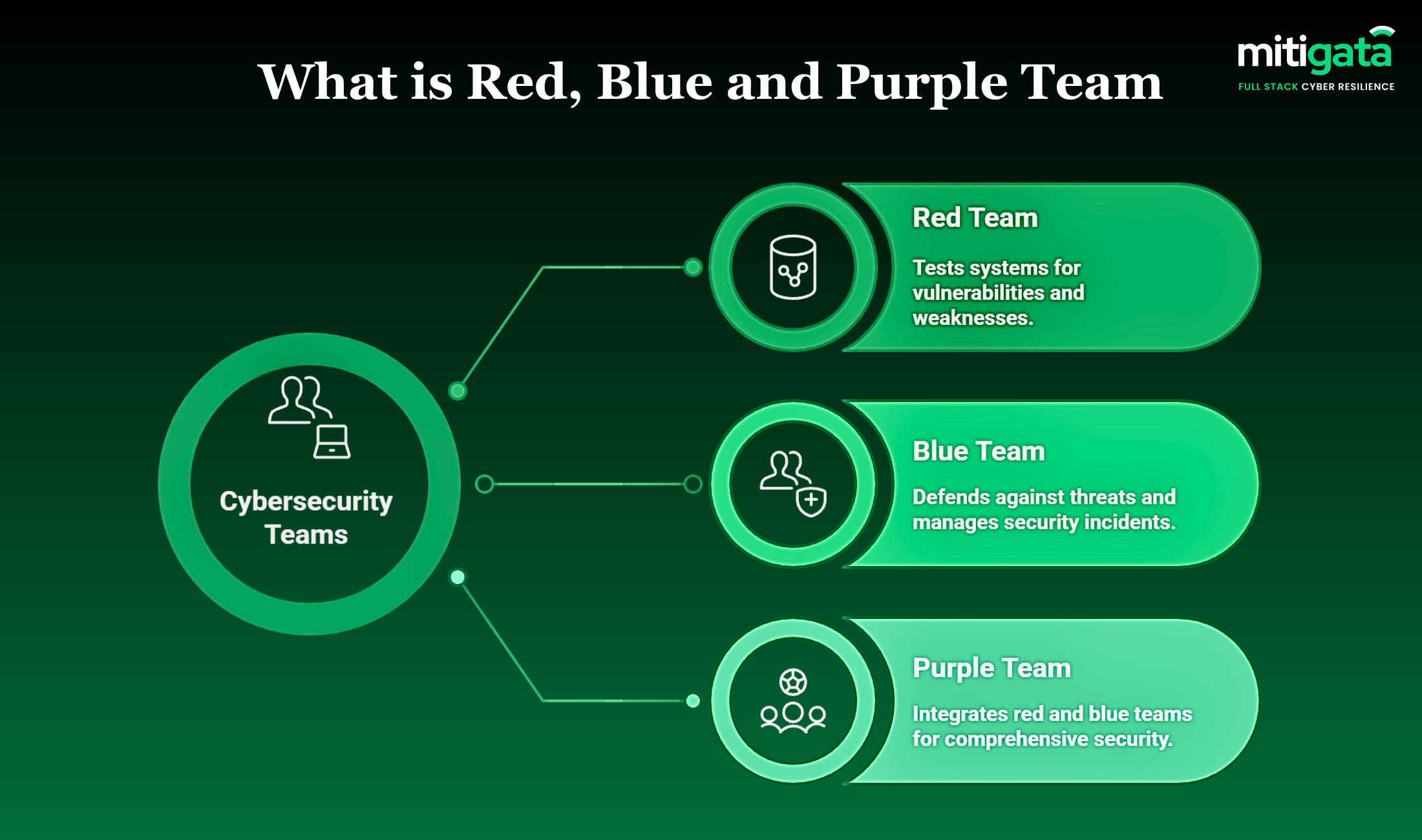
Benefits of Red Teaming
In cybersecurity, offensive testing is the primary focus of a red team. A cyber red team tests the human element, procedures, and controls in place, and focuses solely on identifying technical flaws. A few key benefits of the red team are:
- Simulates how real attackers think, plan, and operate in your environment
- Reveals how small security gaps can combine into significant business risks
- Shows leadership absolute attack paths, from phishing to data loss and disruption
- Enables more intelligent risk management and security planning based on real scenarios
Understand the difference between vulnerability assessment and penetration testing to choose the right security approach for your business.
Benefits of Blue Teaming
In cybersecurity, a blue team focuses on defence, detection, and reaction.
This group is responsible for monitoring systems, investigating alarms and incidents, and taking corrective action as necessary.
Key benefits of the blue team are:
- Strengthens day-to-day security by improving threat detection and response across systems using the right tools and processes
- Helps teams quickly recognise which alerts require action and which can be safely deprioritised over time
- Improves visibility into security events, enabling faster decisions during incidents
- Limits business impact through quicker containment, reduced downtime, and well-coordinated incident response between IT and security teams
Discover the key factors to consider when choosing a SOC monitoring tool that fits your security and compliance needs.
Benefits of Purple Teaming
In cybersecurity, purple teaming refers to collaboration. In cybersecurity, a purple team unites the red and blue teams during testing rather than keeping them apart. Key benefits of a purple team are:
- Most effective when both red and blue teams are already active, bringing offence and defence together.
- Improves detection during live testing instead of weeks later through static reports
- Enables security teams to review attack activity, validate alerts, and fine-tune controls in real time
- Promotes shared learning and continuous improvement rather than one-time testing outcomes
Know How Your Attackers Move
Validate exposure, detection gaps, and response speed through integrated red, blue, and purple team testing.

Common Challenges Across Red, Blue, and Purple Teams
These are a few common challenges organisations face when running red team, blue team, and purple team operations.
The Read Team:
Red team exercises may be frustrating if findings are not reported promptly.
Without timely feedback, the teams will find it challenging to link attack methods to gaps in the defences.
The Blue Team:
The blue teams often face an alert overload, where real threats are mixed with the system’s usual noise.
This occurs frequently and makes prioritisation difficult during active incidents.
The Purple Team:
The adoption of the purple team approach requires excellent coordination.
Teams that previously operated independently must now share tools, timelines, and outcomes.
If ownership is unclear, it may take longer to respond to the incident, even if the detection is functioning as intended.
For instance, a red team vs. blue team cybersecurity exercise may demonstrate that alerts are triggered correctly, but response delays still occur due to unclear escalation paths.
Conclusion
The red, blue, and purple teamings build up a strong triadic relationship, which changes the security measures from “fire-fighting” to “mastery”, thus enabling the organisations to conquer the continuous threats.
Through this collaboration, the partners are not only minimising breach costs that run into the millions of dollars but also creating strong cultures in which attackers cannot penetrate.
Contact us today and turn security gaps into proven strengths with Mitigata’s affordable teaming services.
FAQ
What are the benefits of red teaming?
It reveals real vulnerabilities before actual attackers find them and shows you how hackers actually think and operate.
What is the difference between SOC and the blue team?
SOC is the entire security monitoring operation. Whereas the blue team is the defensive squad within it that actively stops and responds to attacks.
What is the primary outcome of a purple team exercise?
In a purple team exercise, defenders learn exactly how attacks work and immediately improve their detection, making security stronger and faster.
What is the difference between red teaming and purple teaming?
Red team attacks secretly to test defences. On the Purple team, attackers explain their moves so defenders can improve in real time.
What is a real-life example of red teaming?
A bank hires ethical hackers to break in, using phishing and social engineering. They succeed through a fake email, exposing gaps in employee training.

